Summary
- Encrypts files using AES-256 and RSA-2048 ciphers, which makes decryption impossible without paying a ransom
- Adds ‘.CRYPTO’ extension
- Replaces the content of the original files with “A”
- Also known as “Ransom:Win32/DoejoCrypt.A” according to the Microsoft’s malware naming convention
- Targeting organizations in the United States, Luxembourg, Indonesia, Ireland, India and Germany
Attack vectors
The attackers use the recently disclosed zero-day ProxyLogon vulnerabilities to hack into Microsoft Exchange servers. The first DearCry attack was discovered on March 9, 2021.
Static analysis
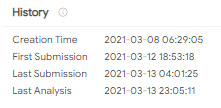
The file under analysis is 1322521 bytes in size (SHA256: fdec933ca1dd1387d970eeea32ce5d1f87940dfb6a403ab5fc149813726cbd65), and at the time of writing was detected by 45 antiviruses out of 68 mentioned on VirusTotal.
This sample was first submitted to VirusTotal on March 12, 2021:
The original file name is ‘encryptfile.exe’ according to static
analysis of the executable file. This can be guessed from the debug information
available in the binary:
c:\users\john\documents\visual
studio 2008\projects\encryptfile -svcv2\release\encryptfile.exe.pdb
Installation
Once executed, the malware registers a service named ‘msupdate.’
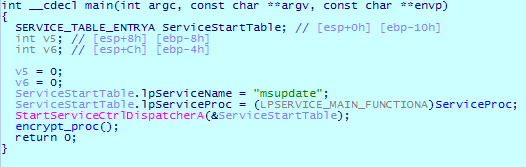
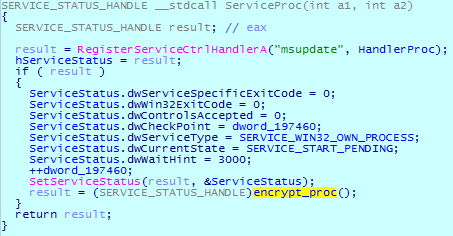
It begins file encryption using this service.
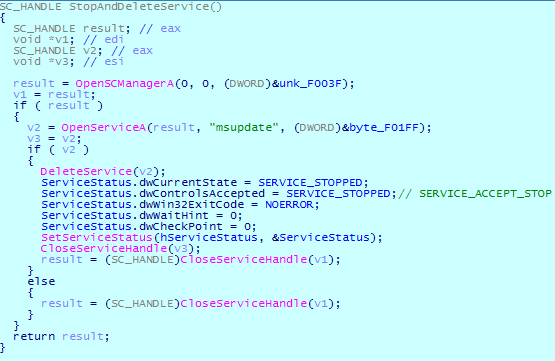
After file encryption is completed, DearCry stops and deletes the service.
File encryption
To encrypt files, DearCry uses the AES-256 cipher, the keys for which are encrypted afterwards with the following master public RSA-2048 key:
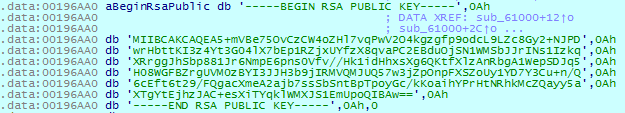
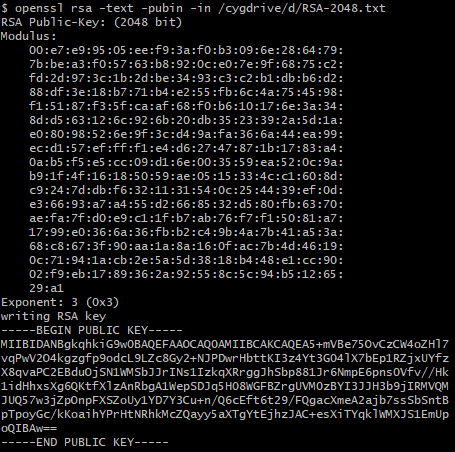
The ransomware calculates the MD5 hash of the public key:
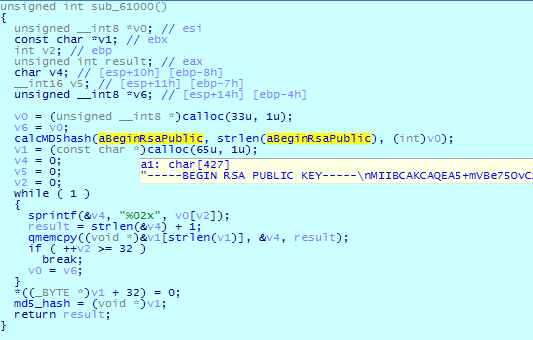
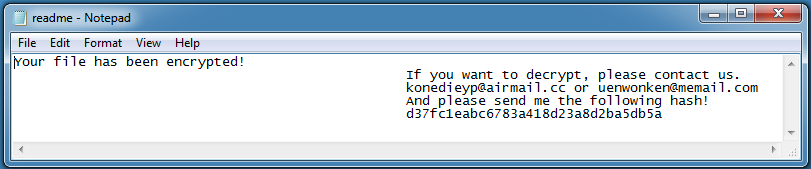
It then inserts this hash into a ransom note:
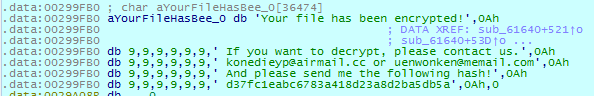
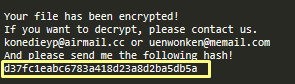
DearCry locates all logical drives from ‘C:’ to ‘Z:.’ If the disk is not a CDROM drive, it creates a text file in the root directory named ‘readme.txt’ and saves the ransom note there.
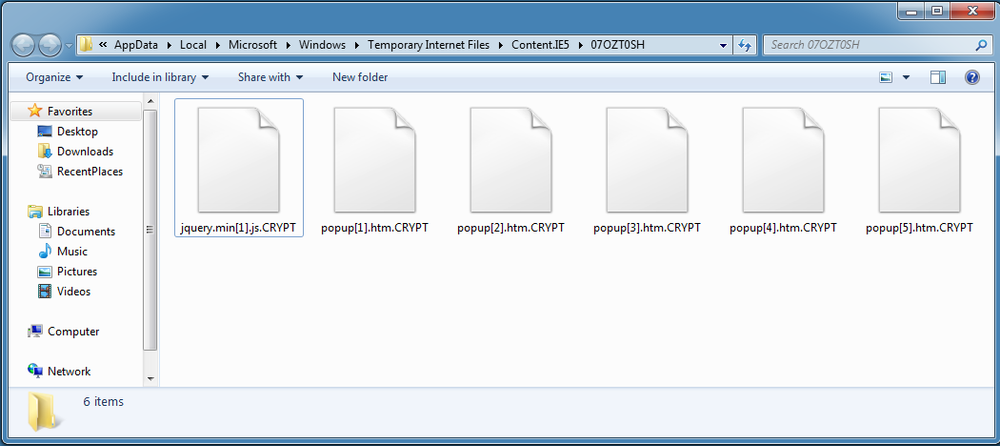
DearCry searches for files on the disk with a filename less than 1300 characters. It encrypts all such files with the following extensions:
.TIF
.TIFF
.PDF
.XLS
.XLSX
.XLTM
.PS
.PPS
.PPT
.PPTX
.DOC
.DOCX
.LOG
.MSG
.RTF
.TEX
.TXT
.CAD
.WPS
.EML
.DBF
.INI
.CSS
.HTM
.HTML
.XHTML
.JS
.JSP
.PHP
.KEYCHAIN
.PEM
.SQL
.APK
.APP
.BAT
.CGI
.ASPX
.CER
.CFM
.C
.CPP
.STM
.GO
.CONFIG
.CSV
.DAT
.ISO
.PST
.PGD
.7Z
.RAR
.ZIP
.ZIPX
.TAR
.PDB
.BIN
.DB
.MDB
.MDF
.BAK
.LOG
.EDB
.ORA
DearCry does not encrypt files in the following folders:
%WinDir%
%AppData%
%ProgramFiles(x86)%
%Temp%
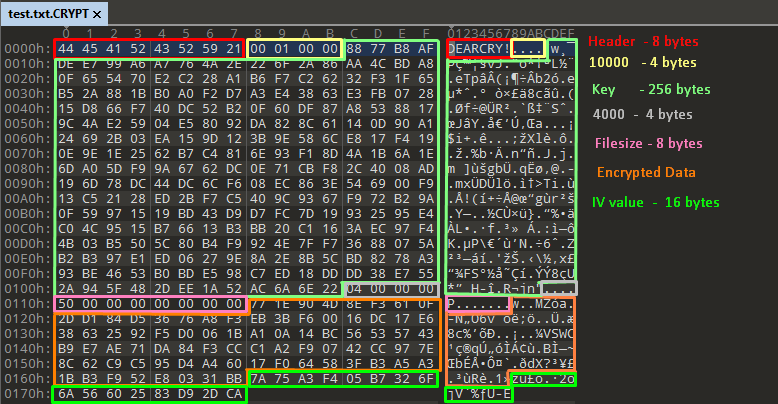
The ransomware adds the header “DEARCRY!” to the encrypted files and also adds the extension “.CRYPT.”
The structure of the encrypted file is as follows:
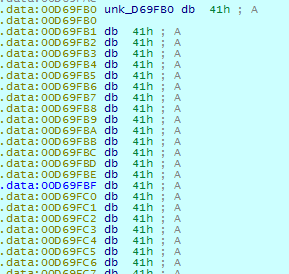
To complicate the recovery, the ransomware overwrites the data in the original file with the character ‘A’:
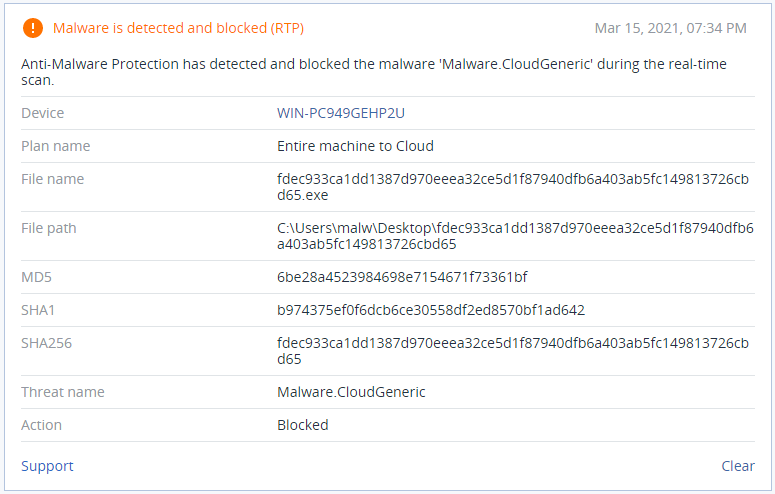
Detection by Acronis
Acronis Cyber Protect not only detects and blocks DearCry ransomware, but can also automatically restore affected files in a matter of seconds.
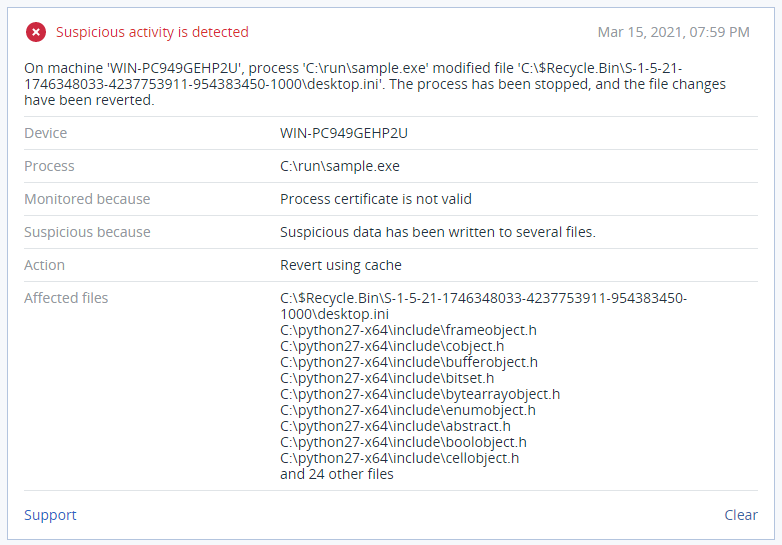
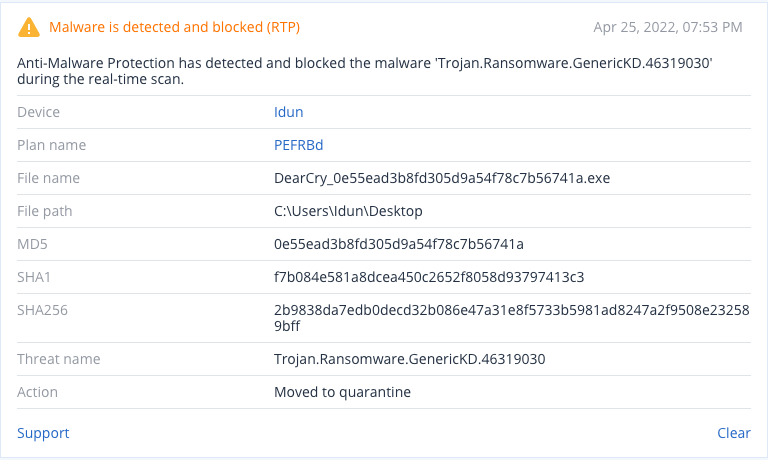
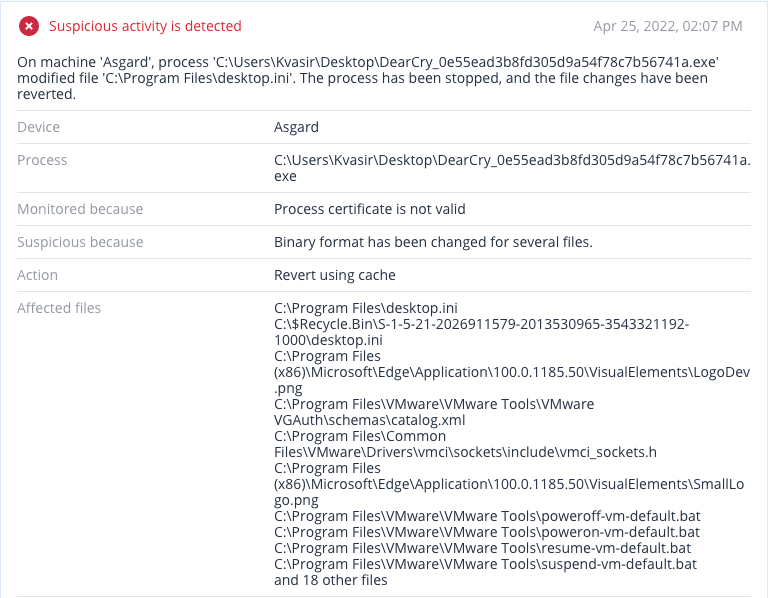
Conclusion
Attacks with controlled execution, in which the attackers exploit zero-day vulnerabilities discovered in popular services, are especially dangerous. The file encryption scheme employed by DearCry — which includes both symmetric and asymmetric encryption — leaves no chance of file decryption without the right key. In addition, overwriting the content of the original files complicates recovery.
Hash: 0e55ead3b8fd305d9a54f78c7b56741a



