Summary
- Written in C++
- First discovered in 2023
- Poor handling of resources due to inadequate logic in encryption
- Does not change the encrypted file’s extension
Introduction
The purpose of Money Message ransomware is to encrypt files on a targeted computer, rendering the victim's system unusable. It was first reported on Twitter by the Zscaler ThreatLabZ research team. Their tweet gave the SHA-256 hash value of the malware and the data leak site on the dark web. There was no analysis that could link the provided intel directly to the Money Message gang. When the malware executes, it loads a pre-set configuration in the form of a JSON file that is extracted from the executable itself. It has been noted that Money Message executes the encryption stage much more slowly than other known ransomware variants such as LockBit or BlackCat.
Technical analysis
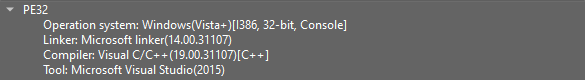
First, looking at the available info, it appears that the malware is a 32-bit architecture Portable Executable (PE) that was compiled with C\C++ compiler.
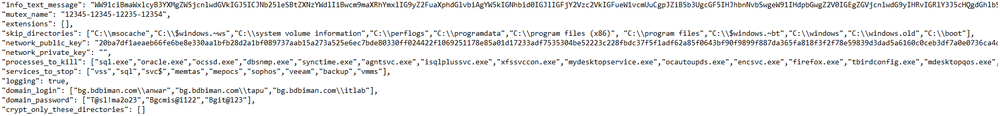
String analysis shows that Money Message contains a block of strings in a data structure that resembles JSON format, which might indicate that the ransomware is storing a pre-set configuration.
Upon executing the ransomware, it can be seen that Money Message attempts to load data from the PE header overlay.
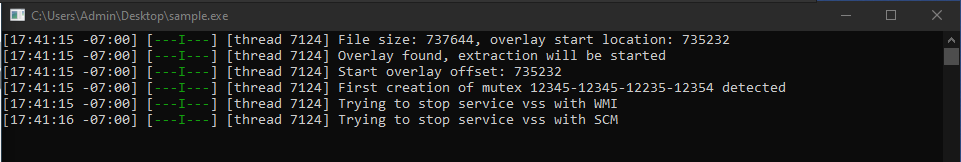
When accessing the overlay segment, we can see exactly what is being loaded into the stack — the “info_text_message” variable.
The “info_text_message” variable contains a possible Base64 encoded string. After attempting to decode the string, the result appears to be the ransom note.
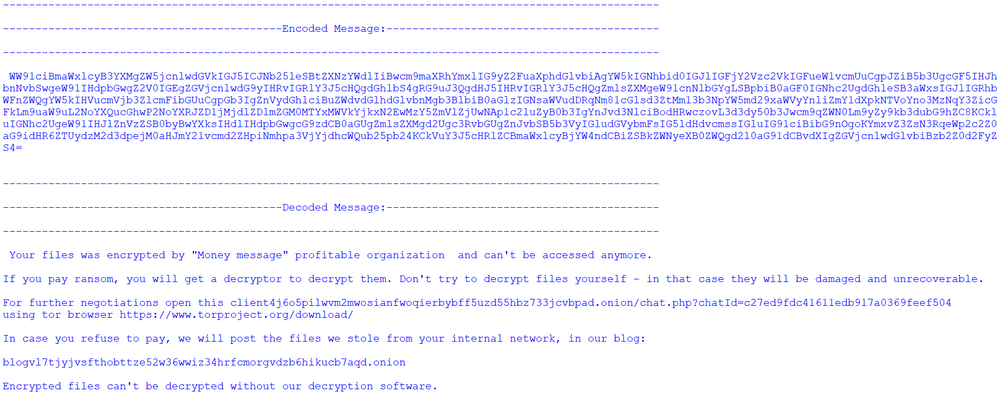
During execution, it is clearly seen that Money Message uses a significant amount of system resources.
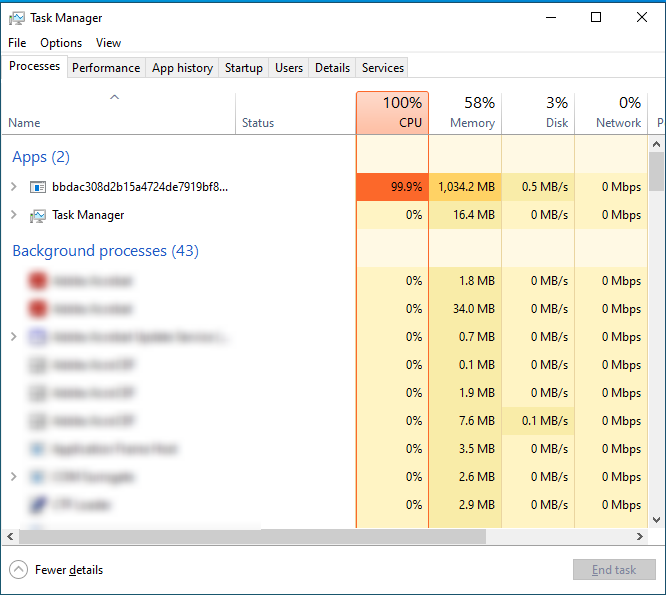
If the ransomware is allowed to execute with its default configuration, it will target the entire system by default, except for a few directories that are pre-configured in the "skip_directories" variable to be avoided. However, this will cause the victim's system to crash and the final steps of execution will not be reached. In order to evade the system crash that is caused by the default configuration, the configuration was modified to encrypt a specific directory.

Modifying the JSON configuration file was achieved by editing the content of the “crypt_only_these_directories” variable, which was the presumable variable responsible for encrypting a specific list of directories.
After executing Money Message with this new configuration, the malware attempts to start SCM.
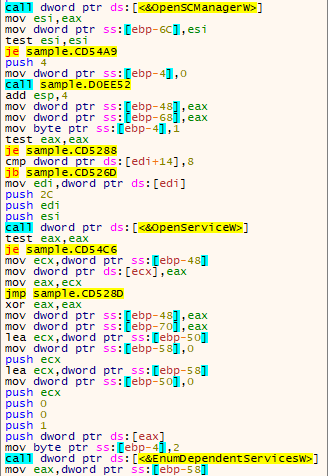
This is done in order to enumerate and stop the pre-configured services list on the infected system, which is stored in the “services_to_stop” variable.
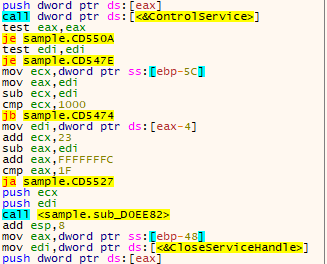
The services mentioned on the list are associated with backup operations.

The ransomware will then attempt to enumerate all running processes and terminate the pre-configured processes that are stored in the “processes_to_kill” variable.
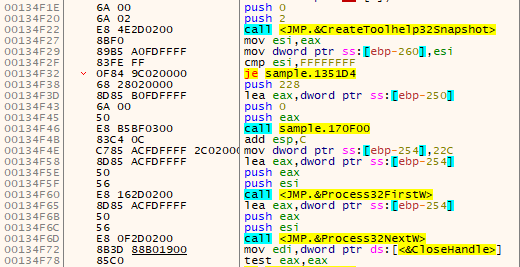
The processes mentioned on the list are associated with backup operations and are stopped in order to ensure that no backup and roll-back can be done to the infected machine.

After Money Message stops these services and terminates these processes, it deletes shadow copies from the system, to prevent the user from restoring the system with previous backups. This is done by using the vssadmin.exe tool and initiated by cmd.exe.

Money Message will then attempt to enumerate all storage drives — from “A:\” through “Z:\” — in the system, in order to achieve a wider impact of the encryption stage. It retrieves the letters to go through from a static string.
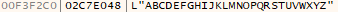


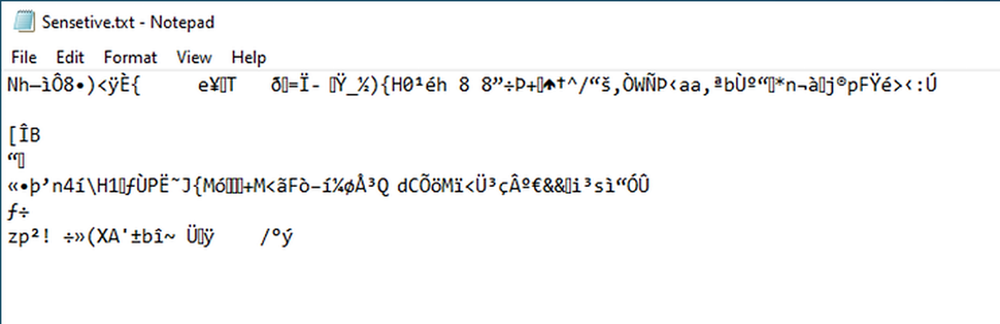
We note that Money Message encrypts files using ChaCha20 protocol. A report published by Cyble states that it is in fact performing encryption using the ECDH protocol next to ChaCha20, leaving the affected files unusable.
After the encryption stage is done, Money Message leaves a ransom note (“money_message.log”) specifying the address of the gang’s leak site and a forum for victims to communicate with their attackers. It’s important to note that while during our analysis, the message was left in a dummy folder created for research purposes, the code shows that this message will normally be left at the highest root folder in the encryption tree.
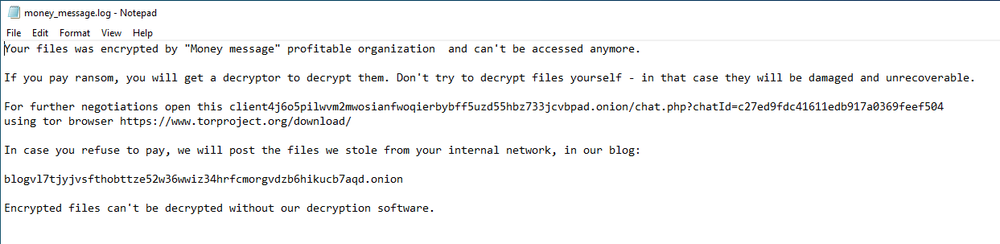
After the malware finishes execution, it terminates its process but does not attempt to delete itself from the victim’s system.
Conclusion
Although the Money Message gang is a new threat actor in the cybersecurity landscape, they have managed to create a significant impact — even claiming to compromise organizations as large as MSI. However, in-depth analysis shows that the ransomware’s encryption logic is inefficient in both runtime and resource management.
It’s important to have a security solution that can identify these threats early in the attack chain and neutralize them even before any attempt to run is made. Acronis Cyber Protect offers full protection against any known destructive malware and unknown operations in the system, ensuring the safety of sensitive documents and information.
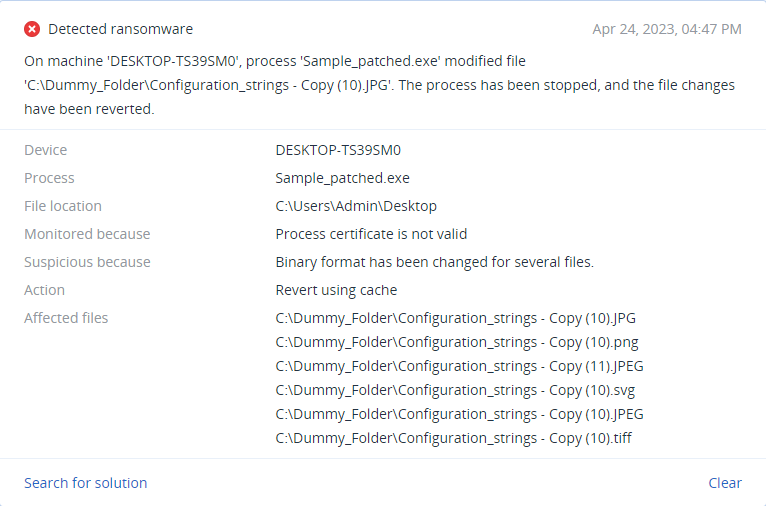
Detected by Acronis
Acronis Cyber Protect successfully detects and prevents execution for the ransomware, despite the slow execution time and evasive techniques.