Summary
- Primarily targets medical industry companies in the United States
- Executed via the command line
- Encrypts a specific path but not the entire system, nor system files
- Created under North Korea's supervision
Introduction
Maui is a wiper that is designed to delete or overwrite data on a computer or digital device, causing damage and disrupting operations. This malware is considered new, being first discovered by the FBI in May 2021, and is presumed to have been developed under the guidance of North Korea.
The main victims to date have been large hospitals and other parts of the medical sector in the United States. Some attacks left systems — including electronic health records services, diagnostics services, imaging services, and internet access — disabled for an extended period of time. In May 2021, a Kansas hospital was infected and opted to pay a ransom of approximately $100,000 in Bitcoin to decrypt its servers.
Technical overview
- Sample name: sample.exe
- Creation time: 2021-04-15
- SHA-256: 5b7ecf7e9d0715f1122baf4ce745c5fcd769dee48150616753fec4d6da16e99e
Maui is only manually activated, possibly as part of a wider attack chain in which it is simply a component run by remote attackers. In order to run, it must be given a path to encrypt through CMD.
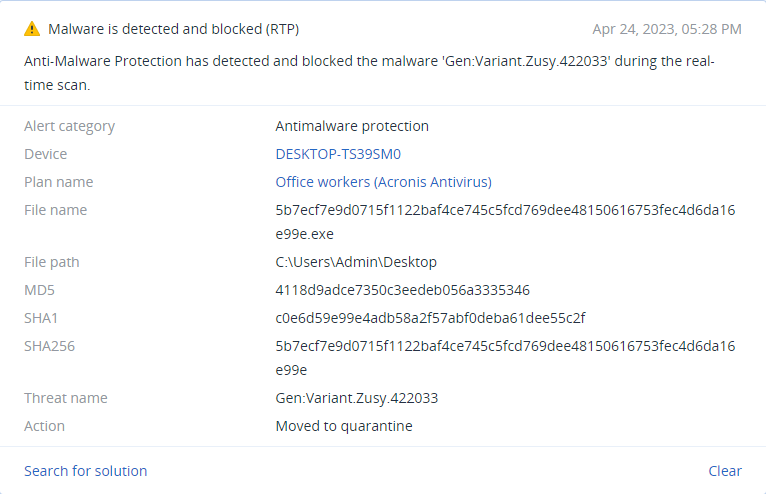
If the malware is not given any path, the user will be presented with a menu containing three different options for running Maui and an explanation for each one.
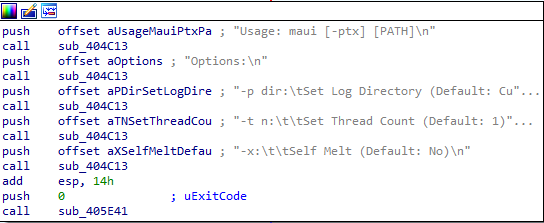
The available options are:
- Set Log Directory — Changing the path which the Maui’s activity logs will be saved. The default is from the path from which Maui was launched.
- Set Thread Count — Choosing the number of threads that will be used for the encryption process. The default is one thread.
- Self Melt — By activating this option, the wiper deletes itself from the drive at the end of the run. The default is “no.”
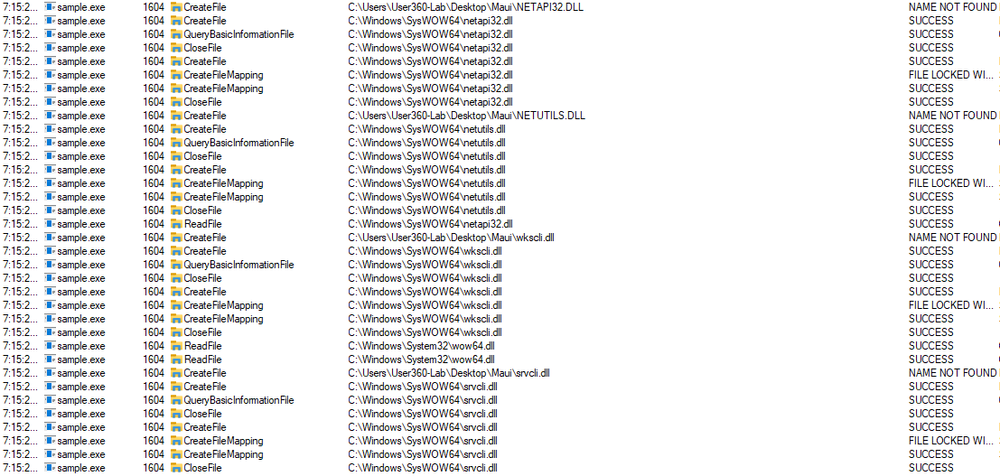
Maui needs some DLLs to work properly. It first seeks them in the folder that it’s located in, and if they are not found, it searches for them in the SysWOW64 folder. Maui needs NETAPI32.DLL, NETUTILS.DLL, wkscli.dll, srvcli.dll, CRYPTSP.dll.
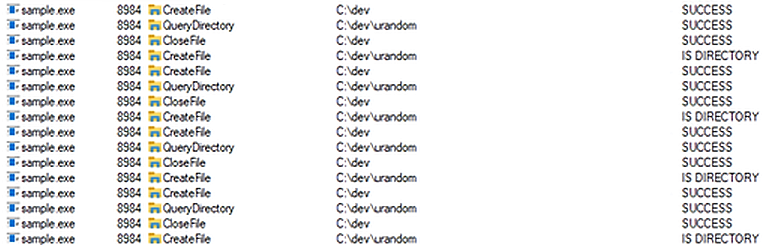
After searching for the DLLs, the malware looks for the path C:/dev/urandom. It's unclear why it seeks this path specifically, as whether or not this path exists, the encryption operation is carried out in the same manner.
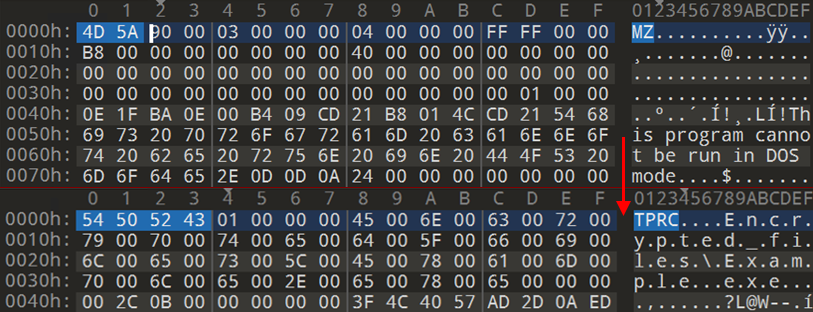
The encryption procedure modifies the file header, which now includes the file's name and full path, as well as an encrypted copy of the AES key.
This informs the wiper of the files it has already encrypted, allowing it to avoid encrypting them again if the attacker inputs the same files for encryption twice.
Despite being able to receive any path to encrypt, an error is returned if Maui is executed with the command to encrypt an OS path. Even when the process receives elevated permissions, it does not encrypt.
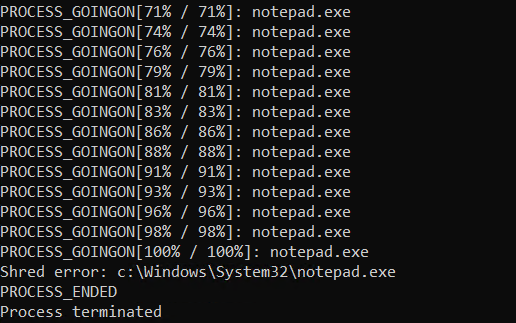
Encrypting critical system files could potentially prevent the wiper from properly executing, hindering its ability to carry out its malicious activities.
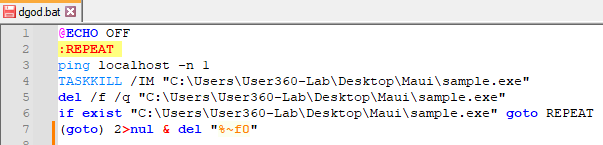
In addition to being able to encrypt paths, Maui has a “Self Melt” option, which is used to remove itself from the infected host. This is done by executing the BAT file that is dropped to the path C:\Users\<Username>\AppData\Local\Temp\dgod.bat.
The file attempts removal of Maui repeatedly, until successful.
Conclusion
Although many vendors state that Maui is an example of ransomware, the evidence to support this claim is lacking. There is no ransom note dropped, and no victim information is collected.
Its behavior is odd in a number of aspects, beginning with the fact that it requires manual activation and provides an explanation of how it works, through the fact that it encrypts robustly but safeguards against harm to system data.
As evidence shows, the medical sector in the United States has already been specifically targeted, which is why having a security solution that can detect and protect against wiper assaults is critical. Acronis Cyber Protect provides complete protection against both known and unknown malware and harmful system processes, ensuring the security of crucial documents and information.
Detected by Acronis
Acronis Cyber Protect successfully detects and prevents execution of Maui’s malicious activities, regardless of whether the malware is in fact a data wiper or ransomware.