Summary
- Discovered in 2022
- Samples are PE64 executables, written in C/C++
- Discovers other computers in the local network, scans for network shares and deletes shadow copies
- Can be executed only with a specified ID given as an argument
- Can encrypt particular folders and percentages of file
- Encrypts files using AES and RSA algorithms from OpenSSL library
- Encrypted files have ‘.royal’ extension
Introduction
Royal ransomware was first spotted in January 2022, targeting different corporations. This group does not provide ransomware-as-a-service. The attackers demand figures ranging from $250,000 to over $2 million from their victims.
On December 1, 2022, Royal ransomware was used to attack the telecom provider Intrado, with the gang demanding $60 million in ransom. We have not yet seen the leaked data, but the criminals shared a ~50 MB archive with some stolen files (including passports and other documents) as proof of breach.
Technical details
Overview
The Royal ransomware sample (sha256:5fda381a9884f7be2d57b8a290f389578a9d2f63e2ecb98bd773248a7eb99fa2) is a PE64 executable, not packed or obfuscated and written in C/C++:
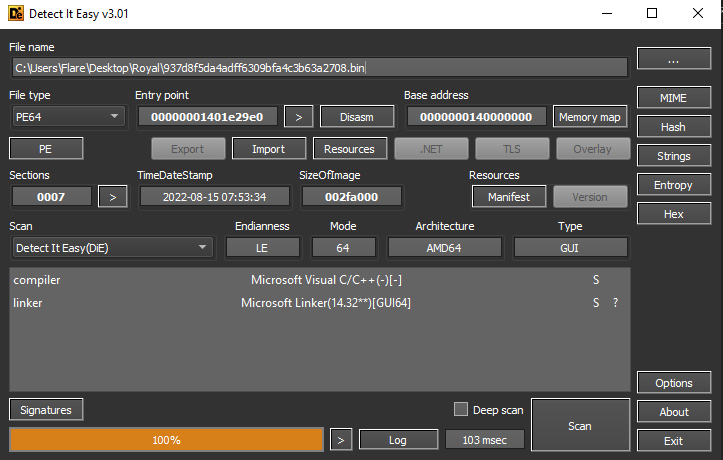
Execution
The Royal ransomware sample was developed as a console application. At the start of execution, it takes parameters using the CommandLineToAtgW() function.
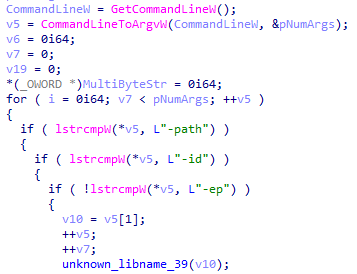
These arguments are:
- -path — the path to files that must be encrypted
- -id — 32-byte victim’s ID
- -ep — encryption percentage of the file
Royal ransomware requires the ID parameter — without it, encryption will not begin.
After receiving parameters, the malware deletes all volume shadow copies using the ‘vssadmin.exe’ tool. The interesting thing is that this operation occurs before checking the ID parameter, so even if this parameter was not provided (or is wrong), Royal deletes shadow copies from the system.
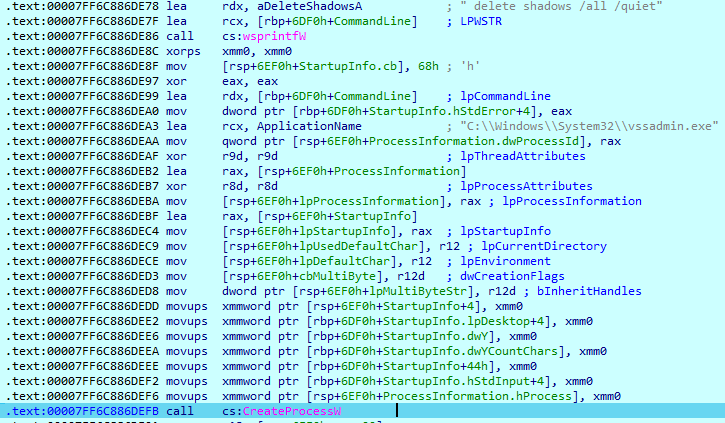
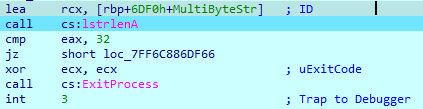
The ID parameter must be a 32-byte value. This is the only check of this ID, so any 32-character value in this parameter will cause the program to start the execution.
The next routine is to check if there are other computers on the network. To do this, it begins with use of the Winsock DLL and then retrieves the interface–to–IPv4 address mapping table using the GetIpAddrTable() function.
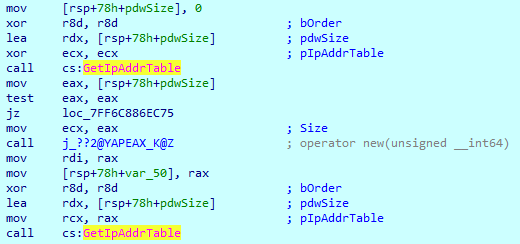
Royal then creates a socket that is bound to a specific transport-service provider with the WSASocketW() function, using the following arguments:
- af = 0x2 — AF_INET (The Internet Protocol version 4 (IPv4) address family)
- type = 0x1 — SOCK_STREAM (A socket type that provides sequenced, reliable, two-way, connection-based byte streams with an OOB data transmission mechanism)
- protocol = 0x6 — IPPROTO_TCP (The Transmission Control Protocol (TCP))
- g = 0 – No group operation is performed
- dwFlags = 0x01 — WSA_FLAG_OVERLAPPED (Creates a socket that supports overlapped I/O operations)
After that, the created I/O completion port is associated with a TCP socket using the CreateIoCompletionPort() function.

Then it begins to connect to other hosts on the network via port 445:
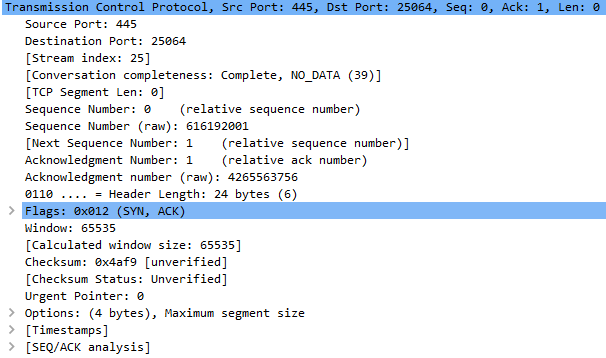
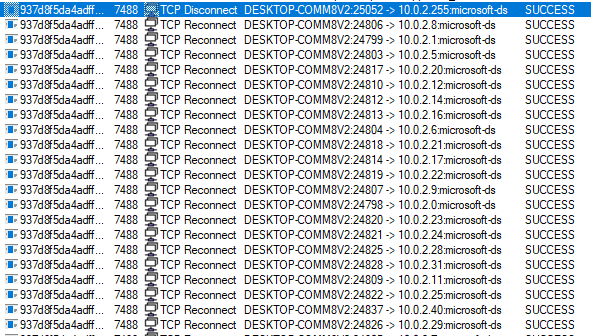
Royal can enumerate all available shares on the system using the ‘NetShareEnum’ function call. It will scan shares, and if the found name matches with the “ADMIN$” or “IPC$” strings, it will skip them during encryption.
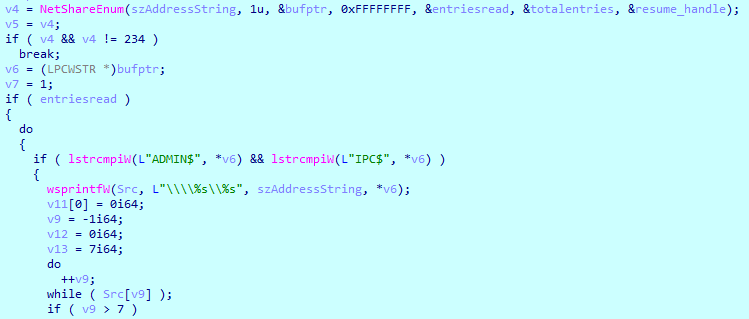
File encryption
Once executed, Royal adds a stored list of extensions to the exclusion list. The strings are encoded in HEX format in reverse order. The decrypted strings look as follows:
0x7400610062002Ei64 –
.bat
0x6C006C0064002Ei64 –
.dll
0x6500780065002Ei64 –
.exe
0x7400610062002Ei64 –
.lnk
.royal
In addition to file extensions, it excludes some folders from encryption:
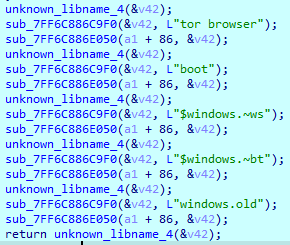
To prevent the use of targeted files by other applications, Royal restarts the ‘explorer.exe’ process using Restart Manager API calls.

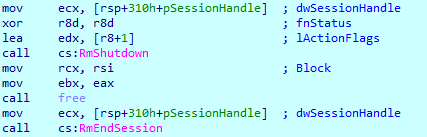
Before starting the encryption process, Royal checks the system information to know how many threads it can spawn. Threads will be started with the ‘sub_7FF6C88F870’ function start address.
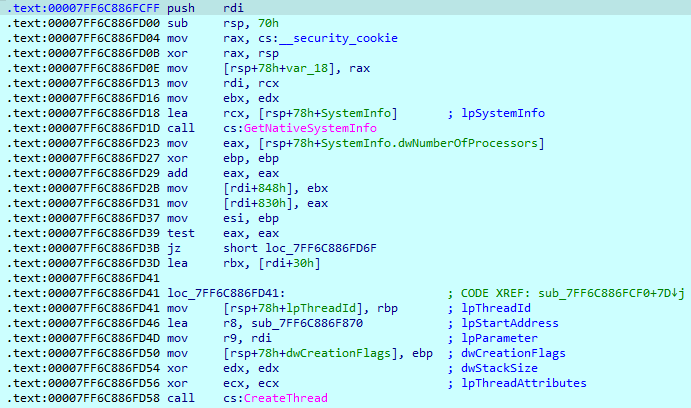
This function contains the main encryption routine. First, it loads an RSA public key hardcoded in the sample.
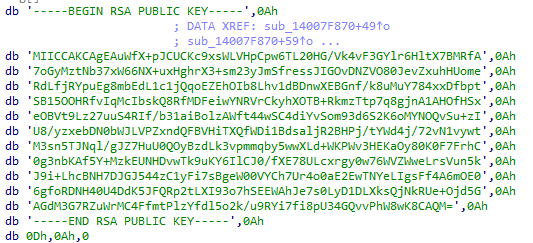
It loads these modules, which are part of the OpenSSL crypto library.
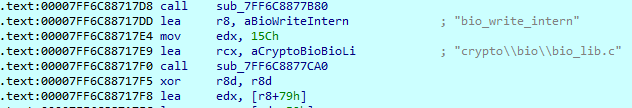
Royal obtains all available logical drives in the system with GetLogicalDrives() function and drops a ransom note titled “README.txt” on each found drive.
Then, it starts searching files using the FindFirstFileW() and FindNextFileW() functions. When an appropriate file is found, it reads the content with ReadFile() and encrypts it using AES-256 algorithm from the OpenSSL library. All encrypted files get ‘.royal’ extension.
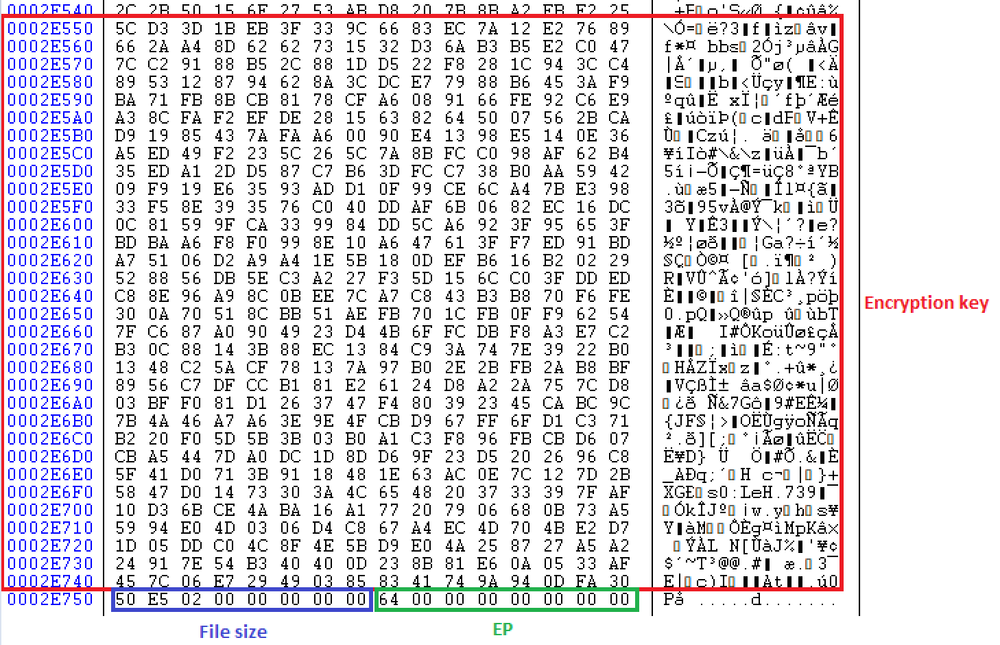
Royal also writes encryption key, file size, and percentage of encrypted data (‘0x64’ = 100%) to the footer at the end of the file.
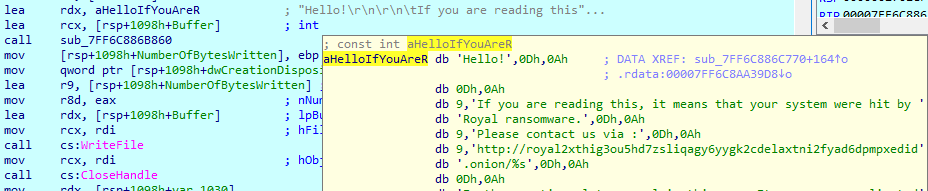
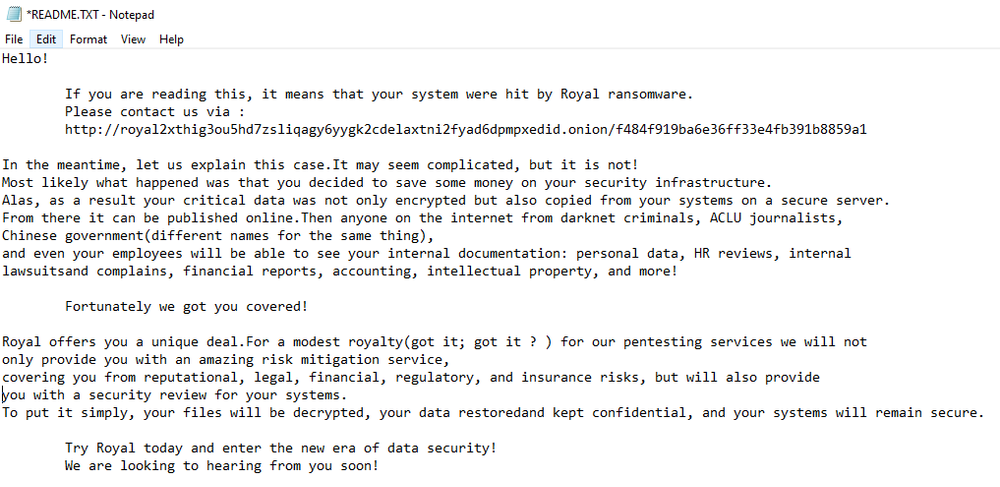
Ransom note
The ransom note contains a URL to contact criminals that includes the victim’s ID, which was provided as a command line argument.
Data leak site
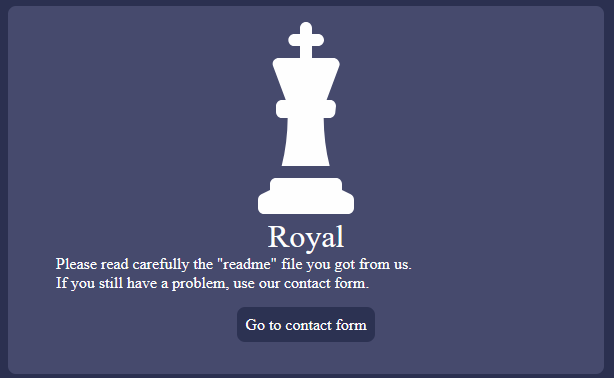
Because the ID was chosen randomly, the URL to the victims' leak site is not valid. The data leak site suggests contacting the criminals.
Conclusion
The Royal ransomware group started its operations in the beginning of 2022, and has successfully breached various companies while demanding high ransoms.
The ransomware uses the OpenSSL library to encrypt users’ files. It can search for other computers on the local network, encrypt files in shared folders, delete shadow copies and terminate the ‘explorer.exe’ process to obtain access to files. It must be executed with provided 32-byte ID as an argument, and it can encrypt specific folders and even percentages of the file. All encrypted files get the ‘.royal’ extension. The encryption key, file size, and encryption percentage are added to the end of the file.
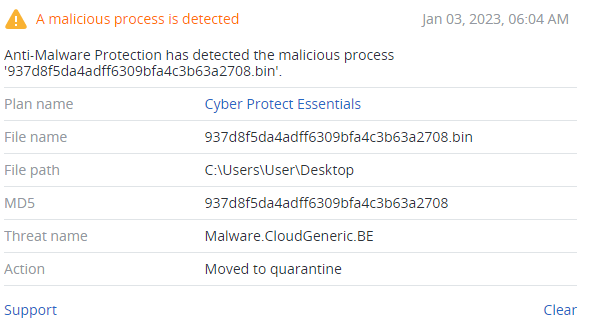
Detected by Acronis
IoCs
Files
SHA256
5fda381a9884f7be2d57b8a290f389578a9d2f63e2ecb98bd773248a7eb99fa2
Network indicators
URL
http://royal2xthig3ou5hd7zsliqagy6yygk2cdelaxtni2fyad6dpmpxedid.onion/[Unique
victim ID]



