Summary
- Discovered in 2014
- Packed in custom packing
- Steals passwords by logging keystrokes and browser information, such as cookies
- Communicates through SOCKS and VNC operations, acting as a proxy for victim communication
- Spreads in the compromised network through SMB protocol
- Removes itself from the victim’s system once it completes all actions
Distribution
Vawtrak is a banking trojan — a form of malware that attempts to steal credentials from banks. It spreads via phishing emails and spam emails that contain a malicious document, loaded with a macro. The primary target of this malware are banks and insurance companies, mainly in Germany.
Behind Vawtrak is the group dubbed “Moskalvzapoe,” which debuted the malware in 2014 and operated it until 2019, when the main actor was arrested. These days, the trojan is distributed sparsely by independent operators.
Vawtrak was offered as a service, offering customers on the dark web access to a specified number of credentials from a specific bank, according to their order. In addition, research uncovered that orders of attack could be placed through Telegram groups that are no longer active.
This banker-trojan gains access to bank accounts via custom keylogging, utilizing the access granted by a wide range of credentials — such as passwords stored in browsers, FTP client private keys and information stored within remote desktop settings.
To communicate, the Vawtrak utilizes a SOCKS connection and exfiltrates information such as screenshots and video captures.
Technical analysis
After placing a breakpoint on WriteProcessMemory (in order to catch the injection of the malware) and checking the functionality of the API calls within the code in MSDN, the parameter to dump the MZ header is clearly shown.
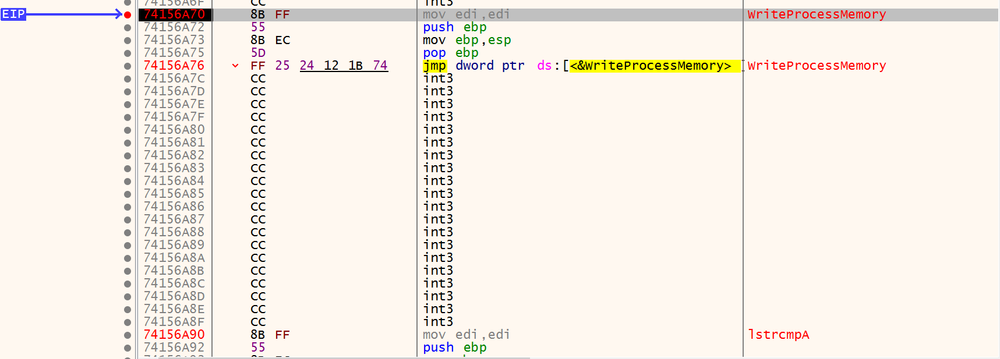
The parameter required to dump the packed information is “lpBuffer” — a pointer to the buffer that contains data to be written in the address space of the specified process.
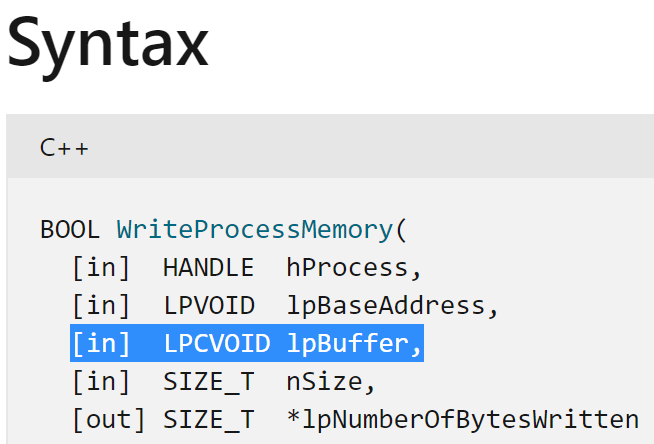
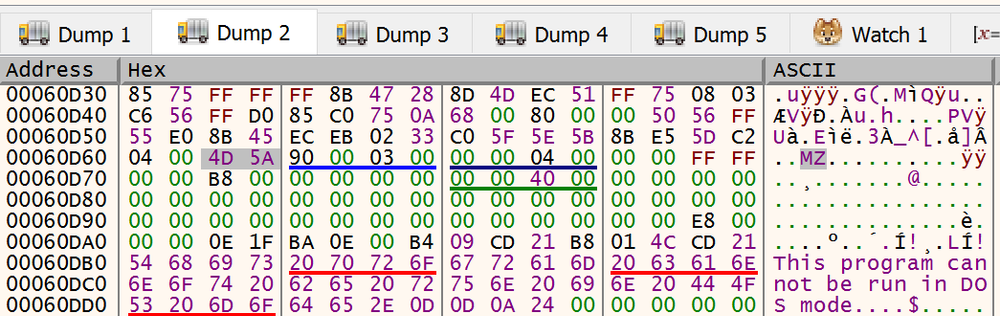
This parameter contains the address 00060000 in this sample, and upon checking the binaries, the MZ file header is clearly shown.
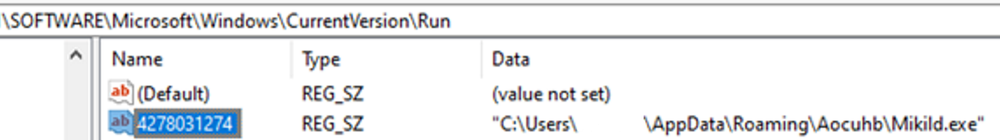
Vawtrak immediately writes itself into the autorun’s paths, in order to gain a foothold on the host upon startup or restart.

As an additional persistence method, the trojan adds itself to the CurrentVersion registry value, under the HKEY_USERS hive, which contains configuration for the users.
After running, Vawtrak creates a child process with same name as the original running process. Thirty seconds into the run, the original malware process terminates. It removes itself from the original running path and copies itself into APPDATA\LOCAL\TEMP, in order to elevate privileges.

Vawtrak then checks whether placing persistence methods was successful, in addition to receiving a handle for itself, as well as file type. If those are not present, and any failed to be fetched, the malware terminates itself and will not run.
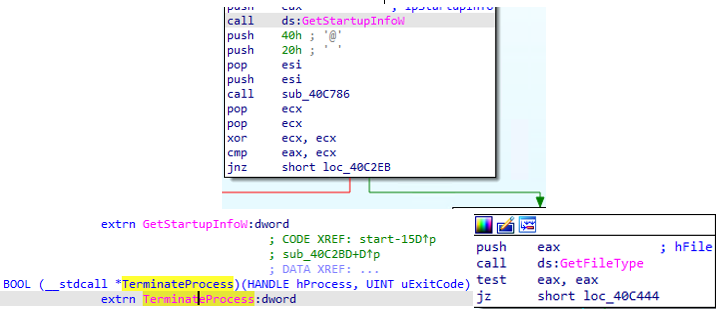
After getting a foothold on the system, Vawtrak — through the injected process — drops additional PE files, which include a DLL file and an executable.
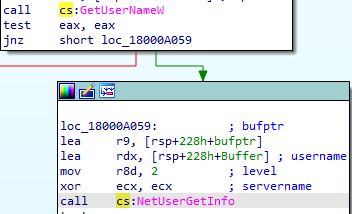
The DLL file contains methods of reconnaissance, such as retrieving usernames and server names through Windows API, as well as extracting the user’s password through Registry keys.
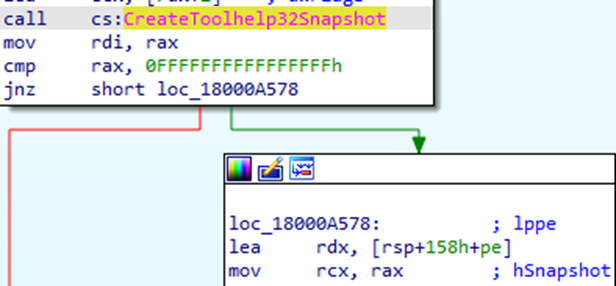
Another of the DLL’s tactics is creating a snapshot and list of all currently running processes. This is usually done by reconnaissance malware in order to target specific artifacts within the host.
When reconnaissance is complete, Vawtrak extracts its C2 server from a seed that’s hard-coded into the malware. It will perform certificate validation in order to check if the server is still available; if not, the Vawtrak goes to sleep for a random amount of time.
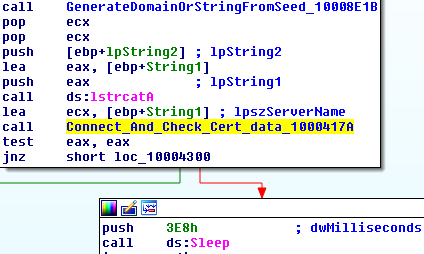
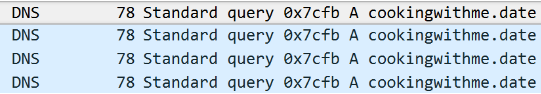
In addition to certificate validation, Vawtrak checks wheter any reconnaissance information has been retrieved. If not, the malware does not initiate communication methods.
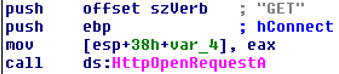

Following all these steps, Vawtrak will attempt to spread through the network utilizing Server Message Block (SMB) — a legitimate Windows filesharing protocol.
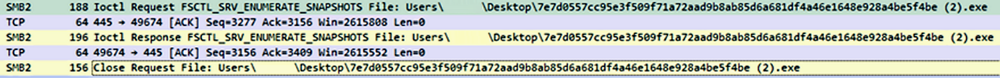
After completing all activities within the host and attempting to perform lateral movement, the malware wipes itself off the host and terminates its process.
Detected by Acronis Cyber Protect
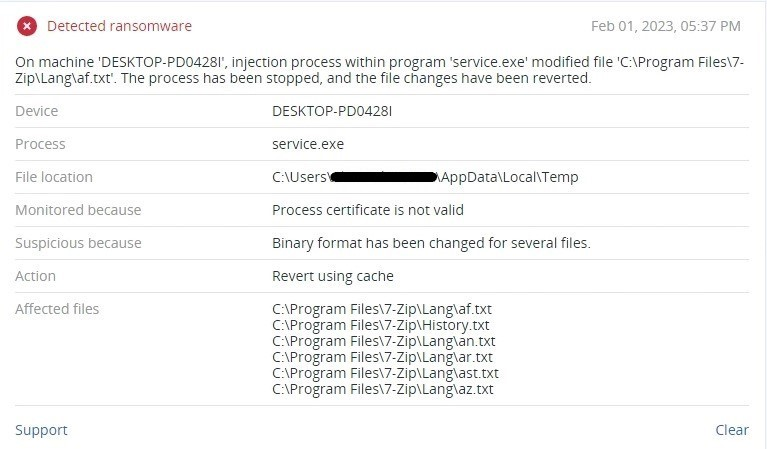
Conclusion
Even back in 2014, when Vawtrak was first spotted, the issue of malicious actors abusing banking information gathered from victims was a prominent one. These days, with more sophisticated malware in the wild — packed, self-extracting and generating unique communication methods — it’s important to stay vigilant about data that is shared online.
Paying attention to the information that is stored on our computers is also crucial, which is why finding a solution that can cover any irregular activity surrounding sensitive services is a must.
Acronis Cyber Protect deals with threats to daily operations, allowing data to remain safe and secured — both online and offline.



