We’ve blogged about RanSim before: it’s a nice tool from KnowBe4, a security awareness training company that employs the famous former hacker, Kevin Mitnick. They help people learn about IT security and prepare for various security threats. RanSim originally served as a ransomware simulator – allowing users to see if their systems were protected against ransomware attacks without the risk of the real thing.
Recently, KnowBe4 updated RanSim so that it also emulates cryptojackers – the latest, fast-growing malware threat that targets computers and mobile devices to hijack system resources to secretly mine cryptocurrency.
At first, it may seem strange to expand a ransomware test tool to include cryptomining malware, until you understand that is exactly what cybercriminals are doing. They are combining ransomware and cryptojacking to deliver one, multi-pronged payload that includes ransomware, cryptojackers, backdoors, worms, and other malware. Different attacks can be executed depending on the operating system, configuration, and defenses. An example of this approach malware named XBash that combines ransomware, coin miner, botnet, and worm features to create a deadly combination.
How the upgraded RanSim works
In general, RanSim is checking to see if an endpoint device is protected by security software that can detect and prevent actual ransomware attacks. It also reports on whether the anti-ransomware software is generating any false positives – incorrectly blocking harmless processes by mistakenly identifying them as malicious. RanSim’s newly added cryptojacking test simulates a Monero cryptocurrency miner. Monero mining is the most popular real-world attack, which steals processing power from the targeted system’s CPU and GPU to complete the complex calculations needed to create the cybercurrency.
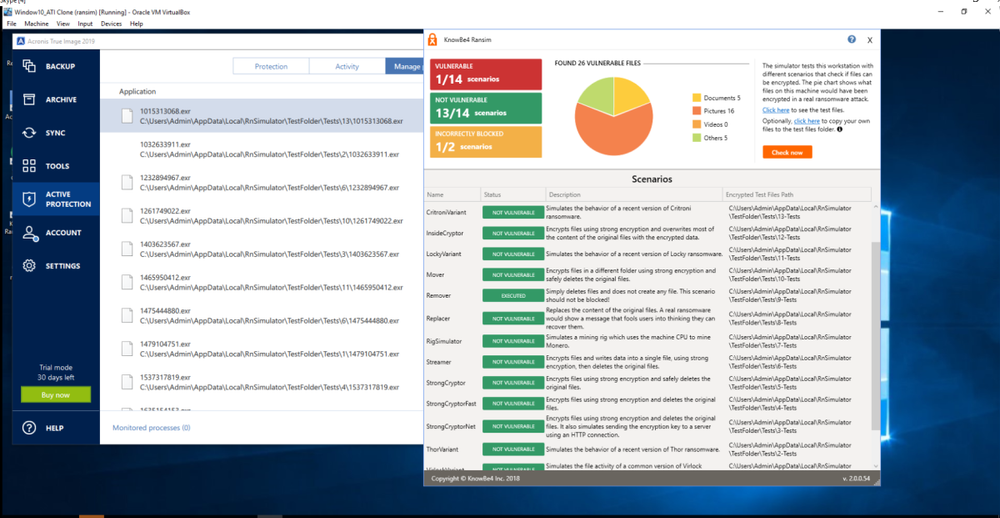
We tried the latest version of RanSim on a machine equipped with Acronis True Image 2019 Cyber Protection, which includes the latest version of our AI-based anti-ransomware technology, Acronis Active Protection. In addition to detecting and terminating ransomware attacks in real time, the heuristics behind this integrated defense were expanded to detect the following scenarios on a Windows system:
- Suspiciously high CPU loads. The definition of “excessive” can be adjusted in real time and can be instantly changed by Acronis’ security experts.
- Use of Event Tracing for Windows (ETW). Cryptojackers make network requests to connect to known mining pools; Active Protection can identify and filter out such requests.
- Windowless processes. In order to stay hidden, most cryptojackers will not create a window. Acronis Active Protection monitors for windowless operations.
- Launches with specific command line arguments. Some specific command line arguments are typical of cryptomining activities, so it watches for these as well.
Those four scenarios cover all the known threats from illicit mining, so detecting them allows Acronis to deliver the necessary protection.
Misinterpreting Paused Processes
One important thing to keep in mind. RanSim is designed to test traditional anti-malware solutions that often react to malware without user interaction.
When Acronis Active Protection detects potential ransomware or cryptojacking activity, however, it notifies the user and asks if the suspicious process should be blocked. Since RanSim usually grades automated responses, if you respond to the request immediately RanSim considers the process blocked. If the user does not act quickly enough, however, RanSim’s timeout logic will incorrectly determine the paused process as vulnerable.
While Acronis’ approach provides more flexibility and choice of action to the user, the test’s rating of blocked/not blocked can depend on the speed with which the user responds.
Similarly, if Acronis Active Protection is waiting for a user response after restoring a file following a ransomware attack, RanSim’s timeout logic may report a vulnerability – even though the suspicious process is already blocked and the user’s system and data are perfectly safe.
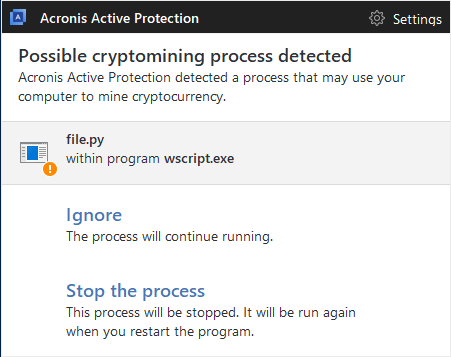
In the event of a real-life attack, Acronis True Image notifies the user that mining malware has been detected on their machine and asks whether it is a legitimate process (e.g., the user is knowingly running a cryptomining app) or malware (i.e., one that is secretly running without the user’s consent).
The Acronis True Image user is able to see the exact script that is performing the cryptomining activity
Final Thought
Illicit cryptomining malware is now one of the fastest growing threats – draining system resouces, degrading performance, and often injecting ransomware and other threats into your system. Having a proven solution that can ensure the safety of your data and prevent your computer resources from being stolen is now required for your digital well-being.
After being tested on RanSim’s enhanced threat test and used in the wild, the excellent results from the latest version of Acronis Active Protection means you can be confident that any of our backup solutions that include it will keep your Windows machine safe from ransomware and cryptojacking malware.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.




