The Rapid ransomware variant began attacking victims at the end of December 2017, according to the ID ransomware service Malwarehunterteam. This ransomware strain is interesting and unique because it keeps running even after encryption is completed, and continues encrypting files once they are created. Our team analyzed a new sample that was compiled a week ago.
Static Analysis
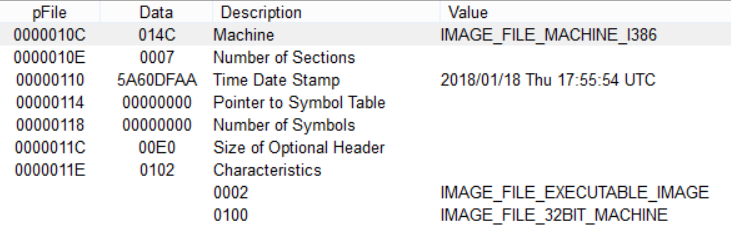
The version under analysis is a Windows PE file and was compiled on January 18, 2018 (MD5: 46f5092fcedc2fee4bfbd572dd2a8f6f).
Installation
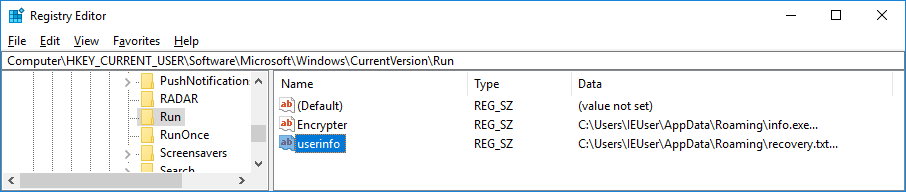
Rapid adds a reference to itself and a ransom note to the Autorun key:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run]
‘Encrypter’ = ‘C:\Users\IEUser\AppData\Roaming\info.exe’
‘userinfo’ = ‘C:\Users\IEUser\AppData\Roaming\recovery.txt’
Key generation
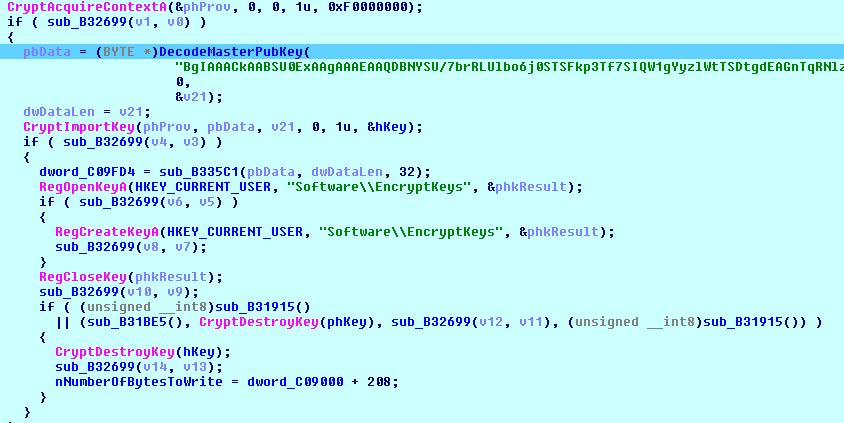
First, the Rapid variant imports the encoded master public RSA 2048-bit key, decodes it, and stores it in the Windows System Registry.
The encoded master RSA public 2048-bit key:
BgIAAACkAABSU0ExAAgAAAEAAQDBNYSU/7brRLUlbo6j0STSFkp3Tf7SIQW1gYyzlWtTSDtgdEAGnTqRNlzbPipl7pbGAZ5vdqOpek+5lIU589lvJZ36aLNBwqFRuigw14tA08Hy2R9zZwUnk1v5JRhOMddAPogx0yIVCOdxJDl4CVyuV4RPWHT1XamwUY+0uwwNvaDHOKviWfKXmK6HIxSiCunwvC2lBOJmXD1OOI0tjLFAc7/hO02GqigI6EerM98febzovQQ0VsWRu4CoJ1kbcMecyPA/HQoWYg92O0orjh+t4tKesHw0e1qiunxrsMaPGizHpUIWpGKR1Pe+ioXD/qL/pRbMrpYEvWmAdSc/tCLP
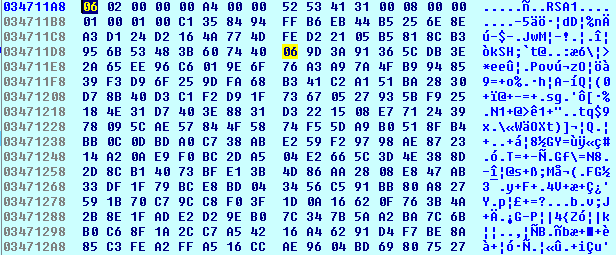
The decoded key in the PUBLICKEYBLOB format is ready to be imported to the Microsoft Cryptographic Provider:
Then, Rapid checks if the ‘local_public_key’ value is available in the System Registry. If not, it generates an exportable RSA 1024-bit key with the following flags:
RSA1024BIT_KEY | CRYPT_EXPORTABLE
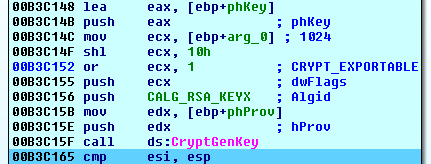
After that, the cryptolocker exports the generated local RSA key pair.
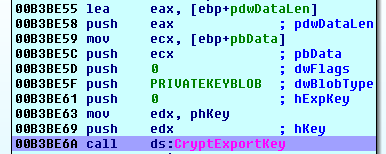
Then, it encrypts the PRIVATEKEYBLOB with the master public RSA key imported earlier.
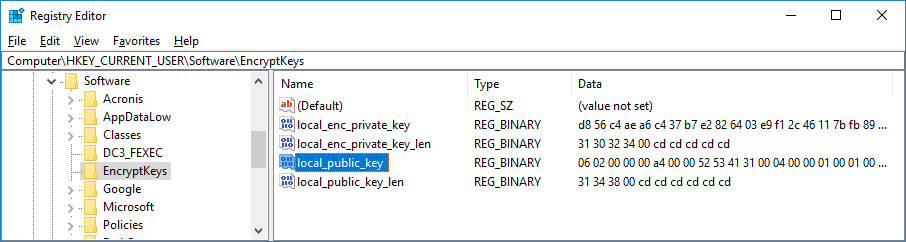
The encrypted local RSA key pair is stored in the following registry key as ‘local_enc_private_key’:
[HKEY_CURRENT_USER\Software\EncryptKeys]
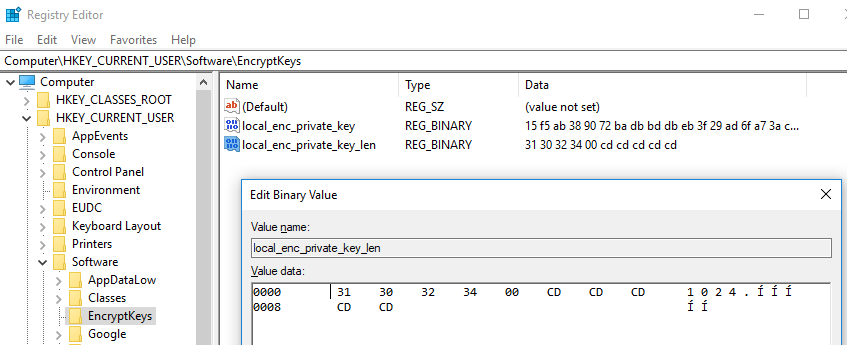
The ‘local_enc_private_key_len’ contains the key length - 1024 bits.
Then, Rapid exports only the public part of the local RSA key pair and stores it to the same registry key.
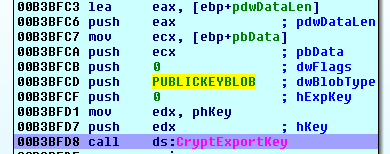
The cryptolocker then reads the local RSA public key from the System Registry and imports it to the cryptographic provider.
File encryption
Before encryption, Rapid ransomware terminates the following files to unlock the database files:
- sql.exe
- sqlite.exe
- oracle.com
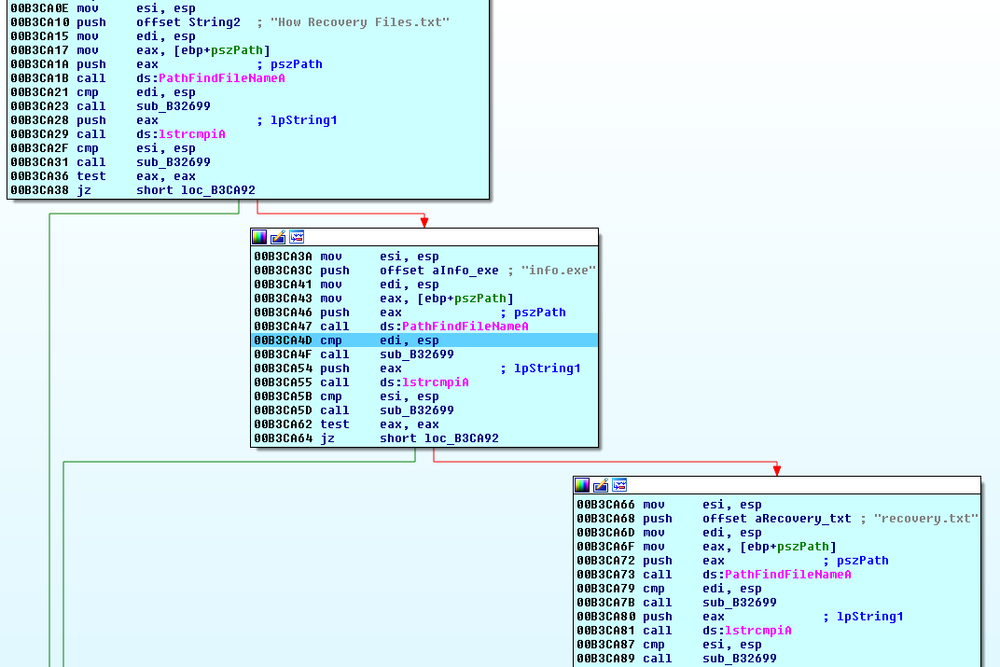
It starts multiple threads to encrypt all found files on fixed, removable, and network drives. When searching the files to encrypt, the cryptolocker checks for the following files that should not be encrypted:
- How Recovery Files.txt
- recovery.txt
- Info.exe
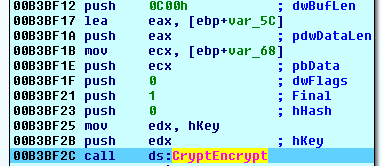
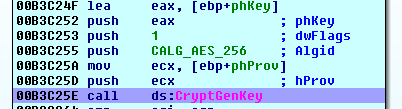
Rapid ransomware uses the AES crypto algorithm with a key length of 256 bits to encrypt the files.
First, it generates a unique AES 256-bit key for every file and exports it.

Then, the exported AES file key is encrypted with the local RSA public key.
Finally, the Rapid variant encrypts files with the AES file key and writes the encrypted content to the original file.
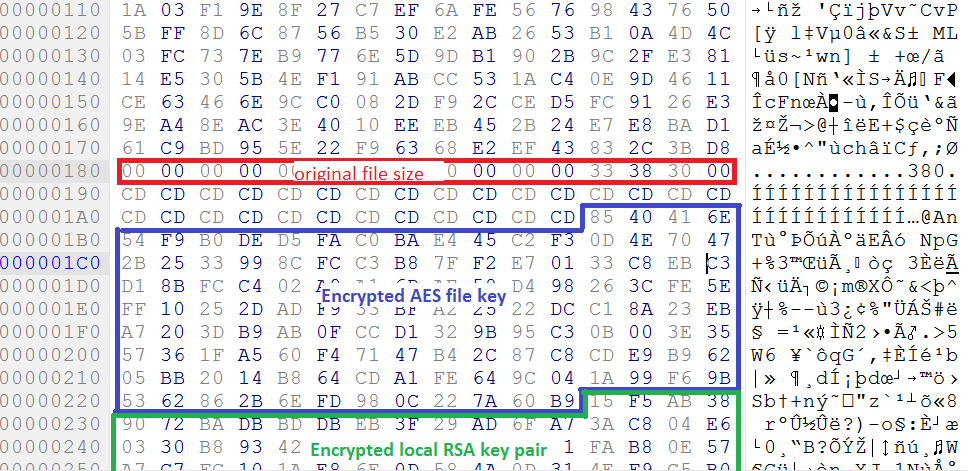
After that, the cryptolocker adds a footer to the end of the file that includes:
- original file size
- encrypted AES key
- encrypted local (session) RSA key pair
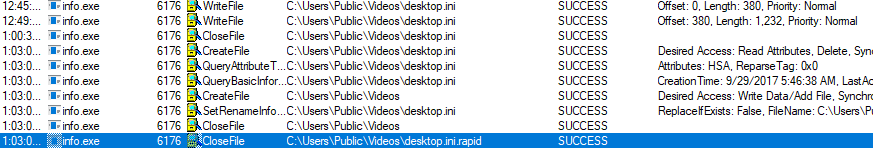
And adds the extension ‘.rapid’ to the original file name.
Rapid does not terminate the process and restarts the encryption threads to search for newly created files.
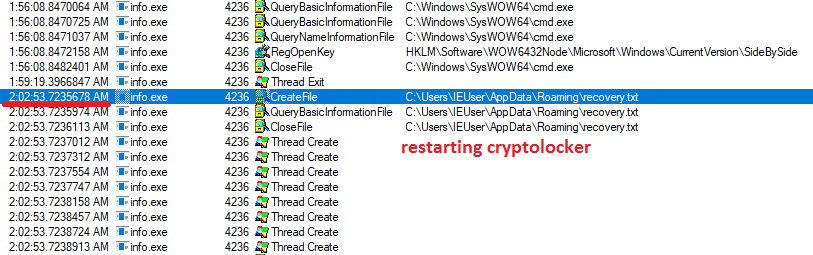
Communication
Not available.
Backup removal
To remove shadow copies of files and disable automatic Windows recovery, Rapid ransomware executes the following commands:
vssadmin.exe Delete Shadow /All /Quiet cmd.exe /C bcdedit /set {default} recoveryenabled No cmd.exe /C bcdedit /set {default} bootstatuspolicy ignoreallfailures
Ransom note
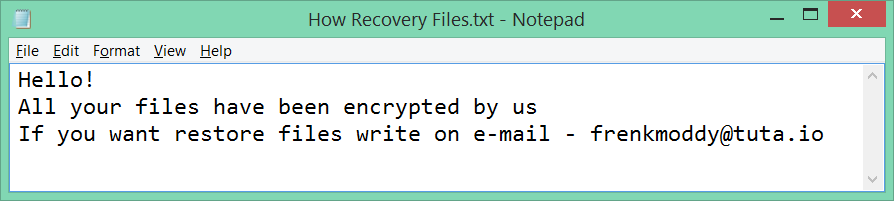
The ransomware creates the text file with the recovery note:
C:\Users\<USER>\AppData\Roaming\recovery.txt
It also leaves ‘How Recovery Files.txt’ files in the folders with encrypted files.
Decryption service
Once a user contacts the cybercriminals by email, the ransomware master will suggest sending up to three files with non-sensitive information, together with ID, to this email address to test the decryption service. The file size should be less than 1 MB in size. One of the files will be decrypted as evidence that decryption is possible. The ransom value will be set in bitcoin and may vary.
Conclusion
The Rapid ransomware strain implements a conventional ransomware encryption model, leaving no chance of decrypting files without knowing the master private key. In addition, the ransomware process keeps running in the memory and continues encrypting new files created by the user. Following the trend, it deletes Windows backup files leaving no chance for unprotected user to recover.
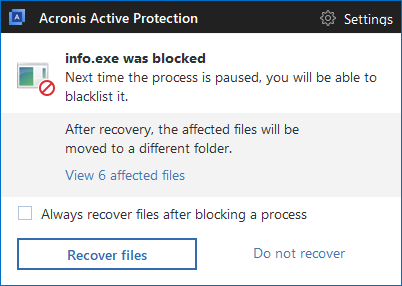
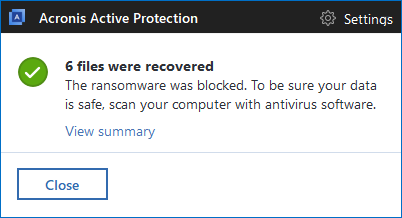
The only way to protect yourself against ransomware is to make backups of your files and have technology like Acronis Active Protection running. Using Acronis True Image 2018 or any of our other products with Acronis Active Protection enabled will detect and stop Rapid ransomware, while giving you the ability to restore any affected files in matter of seconds.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



