One of the most popular and effective tactics for breaching a business is exploiting software vulnerabilities, either in operating systems or in third-party applications. To cast the widest net, cybercriminals target widely used applications, and they do so relentlessly.
The state of security vulnerabilities
According to the Acronis Cyberthreats Report, H2 2024, the Acronis Threat Research Unit found that from July 2024 to December 2024, Microsoft reported 600 vulnerabilities, with 30 being critical RCEs (remote code execution flaws).
In the same time frame, Adobe reported 247 vulnerabilities across 16 popular products, including Adobe Acrobat and Reader. For context: Adobe Acrobat has 100 million users who open an average of 300 billion PDFs each year.
Google, which accounts for more than 66% of web browser market share globally — or three billion users — experienced its own share of vulnerabilities, including four critical vulnerabilities in December 2024 that resulted in a $75,000 bounty payout for security researchers.
The importance — and challenges — of patching
Eliminating vulnerabilities requires the urgent, if not immediate, application of software patches — updates released by software vendors to close security loopholes, add functionality or improve performance. Despite the best efforts from software companies to find and release patches for vulnerabilities, there is always a time lapse, both between the time it takes the vendor to release the patch and the time it takes users or organizations to apply it.
Often, this is because they're understaffed and can't keep up with the volume. In other cases, they have custom (or slightly customized) or old, infrequently updated apps that they need to test for compatibility with the patched release of the OS, as patches will sometimes break an app or make it lose some functionality. In some cases, organizations are simply negligent.
In 2017, Equifax disclosed that a data breach resulting from exploitation of a critical and known vulnerability in Apache Struts software affected 147 million people. Despite being alerted by the U.S. Department of Homeland Security on March 8, 2017, Equifax failed to fully patch its systems, allowing 76 days for cybercriminals to breach its database. In 2024, Equifax was still sending out compensation payments to those affected.
The Equifax breach and the resulting consequences reveals that even large companies with extensive IT resources available to secure applications and systems can be lax in their patching practices.
How to ensure immediate discovery and patching of vulnerabilities
Applying patches as soon as a vulnerability is announced is critical, but in some cases it’s unrealistic, especially when patches aren’t pushed by the vendor but must be applied manually by a user. With dozens of vulnerabilities being announced daily and IT staff being buried under the weight of these and other issues, patches can go ignored for weeks and months. Whatever the case, customers, clients and courts of law will not consider this a mitigating factor, as Equifax learned.
Automating patch management is key to ensuring immediate discovery and patching of software vulnerabilities. With vulnerability assessments and patch management, Acronis Cyber Protect identifies systems and applications that are vulnerable to known threats — either on-demand or via scheduled reports. Vulnerabilities are classified according to a severity scale and required updates — fetched automatically — can be either rolled out automatically or manually. Acronis monitors hundreds of popular third-party applications for software vulnerabilities, providing a real-time glance at known threats from around the world and push-button simplicity for applying patches.
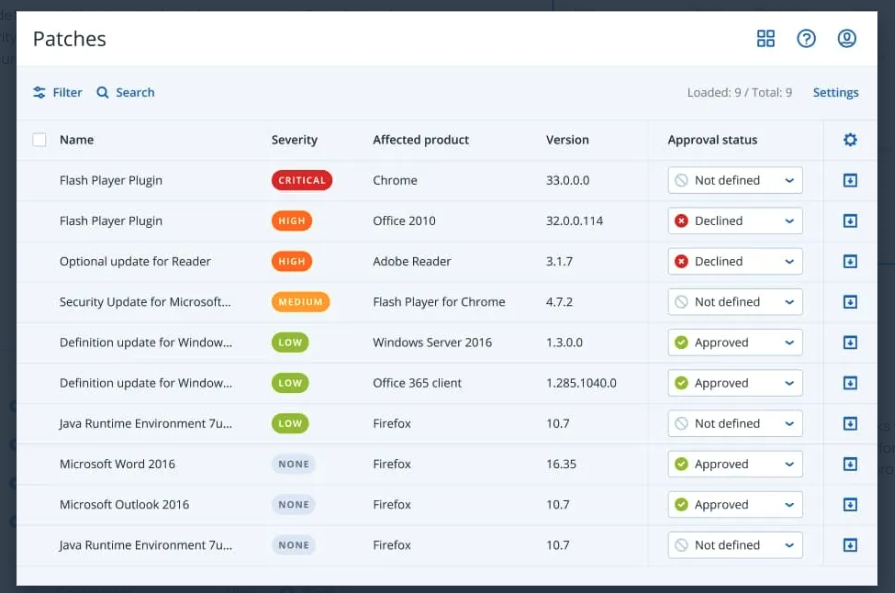
Note that patches are sometimes imperfect and bad patches can cause critical issues, including data loss and / or corruption, system instability or downtime, and even new software vulnerabilities. When either of these is the case, you will need to roll back to a working state. With fail-safe patching, Acronis Cyber Protect creates a backup before patching to ensure the system can be quickly recovered if the patch fails or causes instability. Additionally, Acronis Cyber Protect scans backups for malware to ensure that threats are not reintroduced to the environment on rollback.
Acronis distributes patches from its cloud servers around the world, but it also uses peer-to-peer patch distribution technology to prevent slowdowns during patch rollouts for non-Windows systems and third-party apps. By using delivery optimization, Acronis enables reduction in bandwidth consumption by sharing the work of downloading these packages among multiple devices.
Acronis supports not only Windows-based networks but also Linux networks. Its patch management capability includes a set of client management tools that automate a wide range of IT administration functions, saving time and resources. Additionally, it can patch endpoints located both inside and outside the corporate network, a capability that is frequently demanded by customers with remote and mobile users.
Patching doesn’t have to be a painful — or delayed — process. Acronis Cyber Protect provides the most secure backup and rapid recovery with natively integrated security and endpoint management to secure your business from both known and unknown threats.
To experience these capabilities of Acronis Cyber Protect for SMBs, you can try it free for 30 days. If you are an enterprise organization, schedule a call with an Acronis expert for a tour of Acronis Cyber Protect for Enterprise.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



