Avaddon is a new Maze-like ransomware that not only encrypts the user’s data but also steals it and threatens to make it public. To do that, the Avaddon operator recently launched their own data leak site, where they have already published data from Liberty Linehaul and U.S. Auto Parts Network, Inc. What makes this ransomware unique is the way it tries to delete backups. In addition to traditional removal of shadow copies of the user’s files, Avaddon also deletes system backups, disables automatic repair and recovery, and cleans the bin. To do that, it escalates privileges with UAC bypassing through CMSTPLUA COM interface exploitation.

Summary
- Attacks both regular users and organizations.
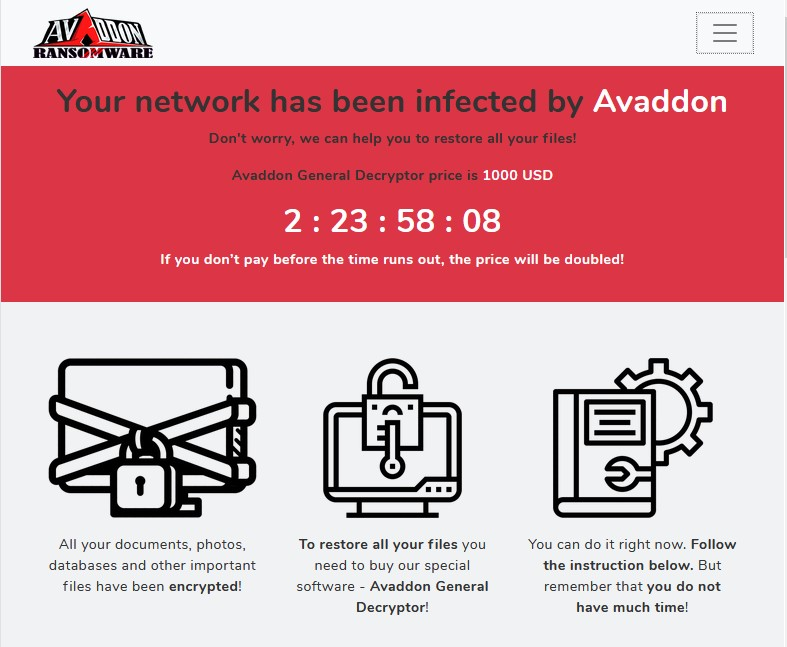
- The ransom payment is $1,000, which is doubled if not paid in time.
- The ransomware not only encrypts but also steals data to publish it later if the ransom is not paid.
- Deletes not only shadow copies but system backups and files from the bin, before disabling automatic system restoration.
- Does not encrypt files on the systems with a Russian default locale.
- Exploits CMSTPLUA COM interface to bypass UAC.
Ransomware delivery
Avaddon ransomware is typically delivered through phishing emails that contain malicious attachments in the form of a zip archive with malicious JavaScript inside.
Language check
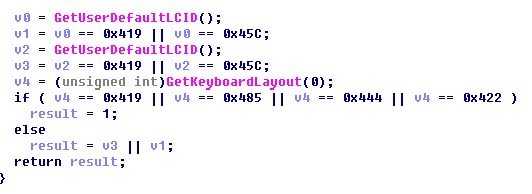
It’s common for malware to check the user’s locale before infecting the victim’s systems. Avaddon first checks the user’s default locale using the GetUserDefaultLCID() function. If it is Russian (ru-RU) or Cherokee (chr-Cher-US), it leaves the system without encrypting anything. Previously, Avaddon checked for a Ukrainian custom locale (uk-UA) instead of Cherokee – which seems to be a developer’s mistake. At the second step, the malware checks the input locale identifier using GetKeyboardLayout().
If it is Russian(ru-RU), Ukranian(uk-UA), Tatar(tt-RU), or Yakut(sah-RU), it does not encrypt the user’s files.
Privilege escalation
Once the language check is passed, Avaddon uses a well-known technique of bypassing UAC via a COM interface. The vulnerability is in executing elevated COM objects without UAC prompting to run processes with escalated privileges.
The code of the exploit is available on github: https://gist.github.com/api0cradle/d4aaef39db0d845627d819b2b6b30512
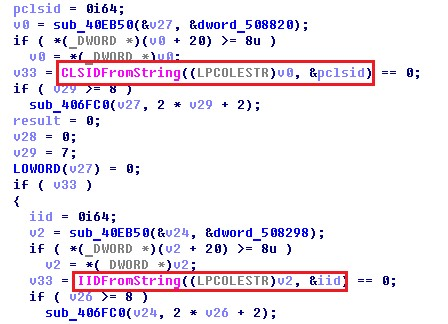
Avaddon contains the registry keys to find CMSTPLUA and ICMLuaUtil class identifiers to exploit this vulnerability.
Elevation:Administrator!new: CMSTPLUA {3E5FC7F9-9A51-4367-9063-A120244FBEC7} ICMLuaUtil {6EDD6D74-C007-4E75-B76A-E5740995E24C}
The ransomware seems to borrow the exploit’s code from the public Github repository.
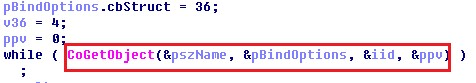
As a result of exploitation, the process ‘dllhost.exe’ responsible for running COM objects has been launched with elevated privileges. Moreover, it starts Avaddon’s code with admin rights.
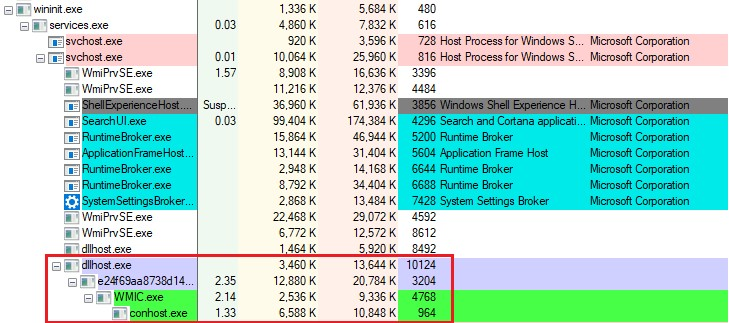
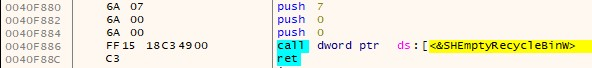
Once executed, the ransomware deletes backups and shadow copies and disables automatic repair and recovery to prevent the restoration of original files on the infected system.
wmic.exe SHADOWCOPY /nointeractive wbadmin DELETE SYSTEMSTATEBACKUP wbadmin DELETE SYSTEMSTATEBACKUP -deleteOldest bcdedit.exe /set {default} recoveryenabled No bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures vssadmin.exe Delete Shadows /All /Quiet
Avaddon also cleans up the recycle bin.
Obfuscation
All the versions of Avaddon ransomware contain obfuscated strings. The obfuscation algorithm hasn't been changed, except for its keys. Avaddon uses XOR and Base64 decoding to decrypt the encrypted strings.
Encryption
The encryption process has six steps:
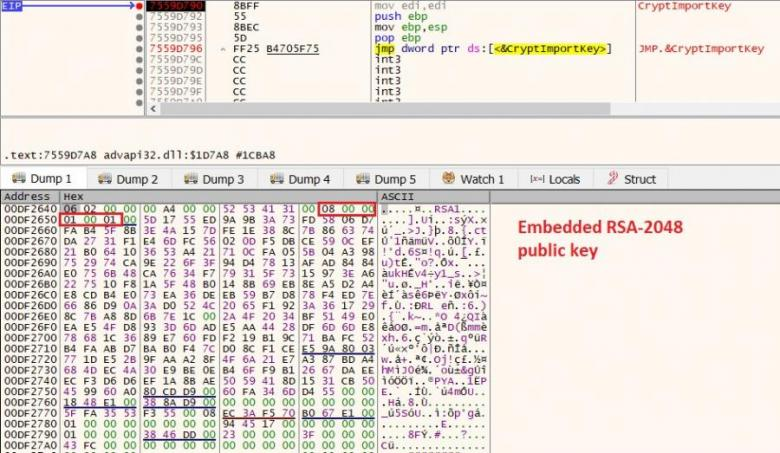
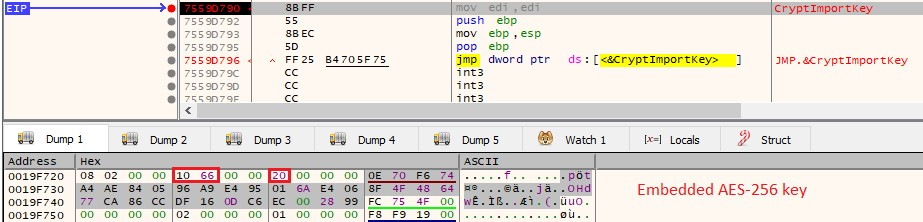
- Imports hardcoded master public RSA-2048 and master AES-CBC-256 keys.
- Generates a session AES-CBC-256 key.
- Adds IV to the master AES-CBC-256 key.
- Uses the master AES-CBC-256 key to encrypt the data about the user with Base64 encoding and adds to the ransom note.
- Encrypts the user’s files with the generated session AES-CBC-256 key.
- Adds the session AES-CBC-256 key encrypted with RSA-2048 key to the end of every encrypted file.
The public master RSA-2048 and AES-CBC-256 keys are hardcoded.
Avaddon ignores some important Windows folders during the encryption process:
C:\Perflogs System volume information C:\Users\Public C:\Users\{User}\AppData\Local\Temp C:\Program Files (x86) C:\Users\{User}\AppData C:\ProgramData C:\Windows
However, the ransomware is determined to encrypt Exchange and SQL servers, so it doesn’t skip the next paths:
C:\Program Files\Microsoft\Exchange Server C:\Program Files (x86)\Microsoft\Exchange Server C:\Program Files\Microsoft SQL Server C:\Program Files (x86)\Microsoft SQL Server
Avaddon also skips files with the following extensions: exe bin sys ini dll dat drv rdp prf swp lnk
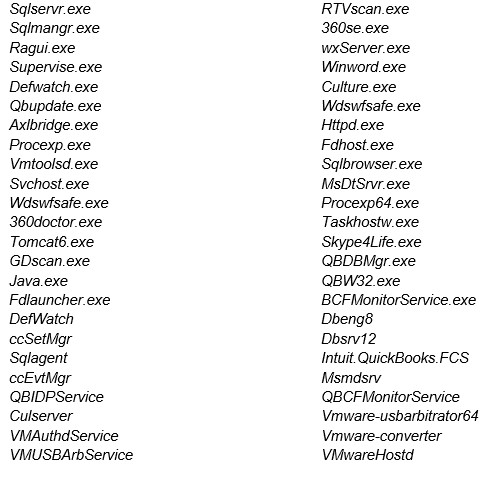
And terminates processes and services that could be related to VMware, malware analysis tools, and cybersecurity products:
After successful encryption, the folder looks like this:
Network connections
Avaddon connects to api.myip.com to identify the victim’s IP address.
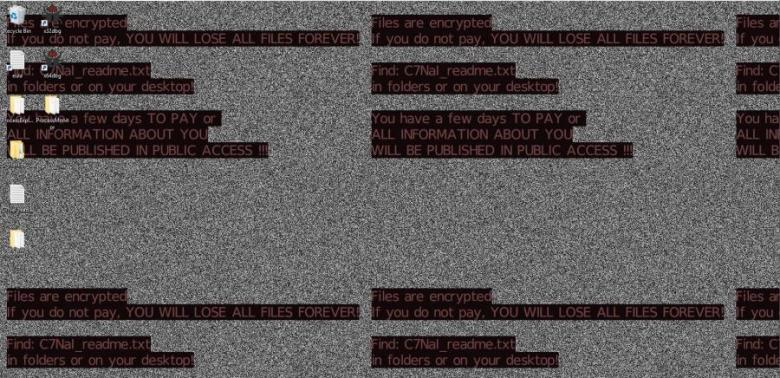
Ransom note
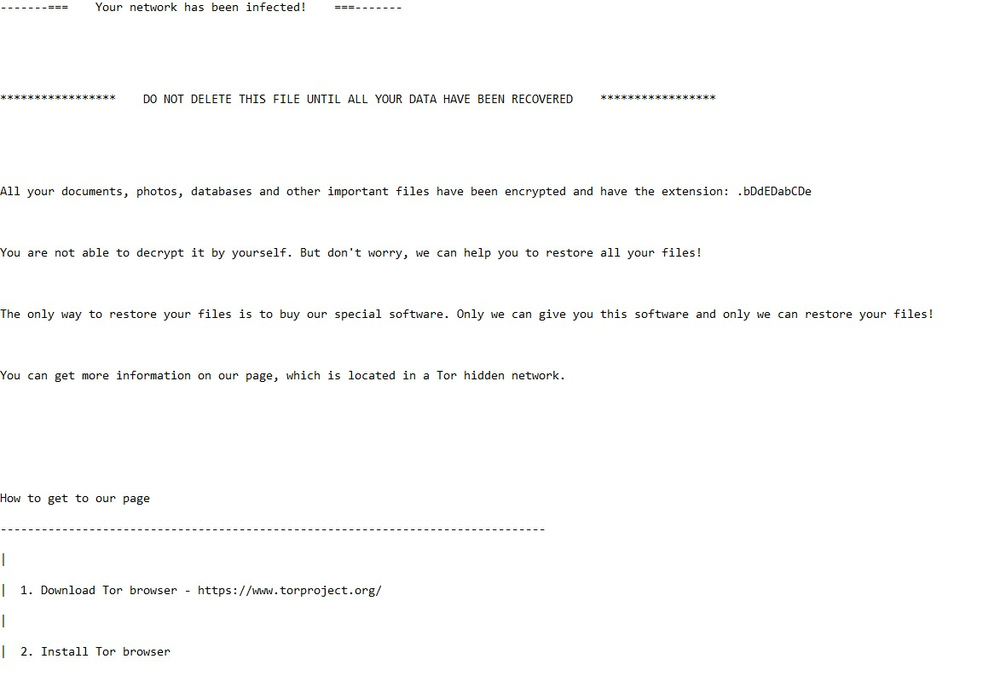
Once all the files have been encrypted, it sets up this wallpaper to notify the victim about the encryption, before putting the ransom note into every folder with encrypted files.
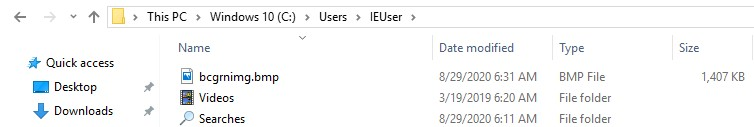
The wallpaper file is named ‘bcgmimg.bmp’ and can be found in the user’s folder.
The ransom note includes a unique extension randomly generated for each user, the Tor link to the decryption service, and the User ID which represents the collection of the encrypted data about the victim.
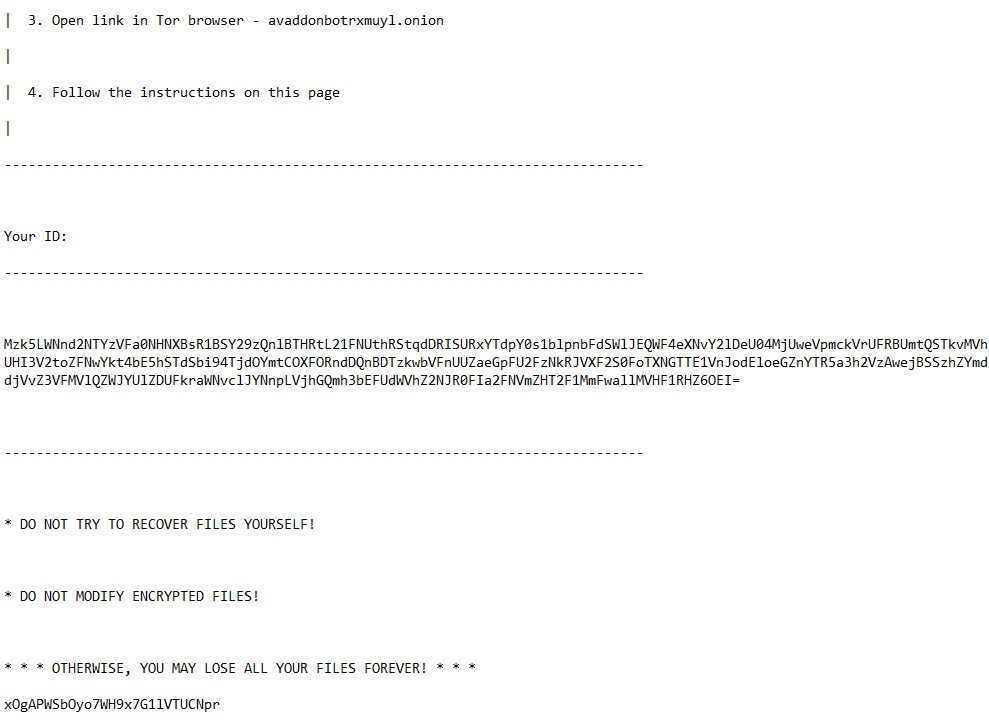
The collected user’s information looks as follows. It is encrypted by the master AES-CBC-256 and Base64 encoded.
Decryption service
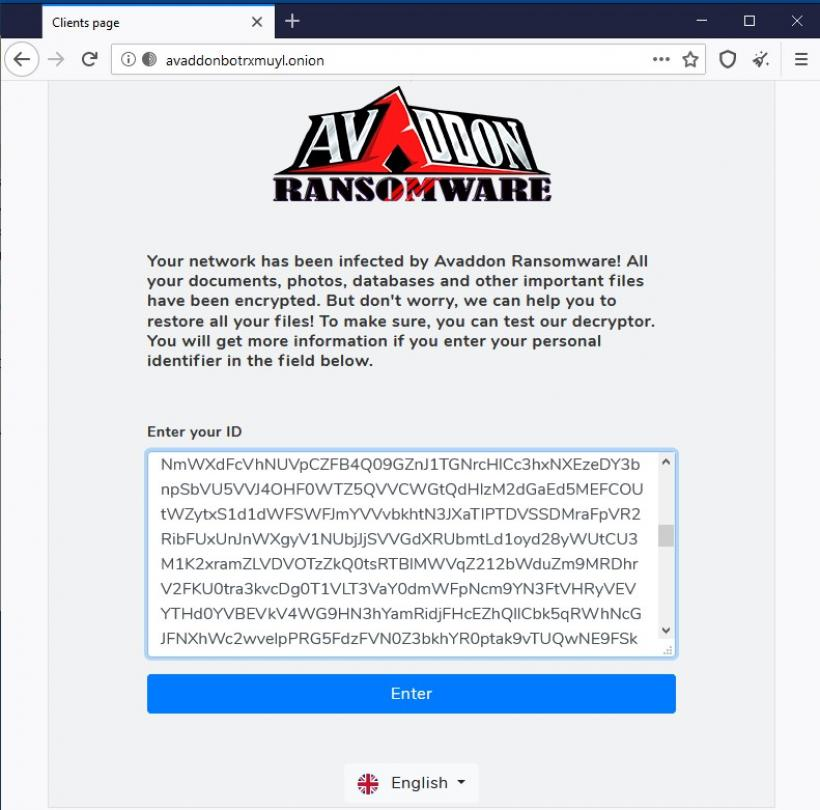
On the avaddonbotrxmuyl.onion page, the victim is asked to enter the User ID from the ransom note.
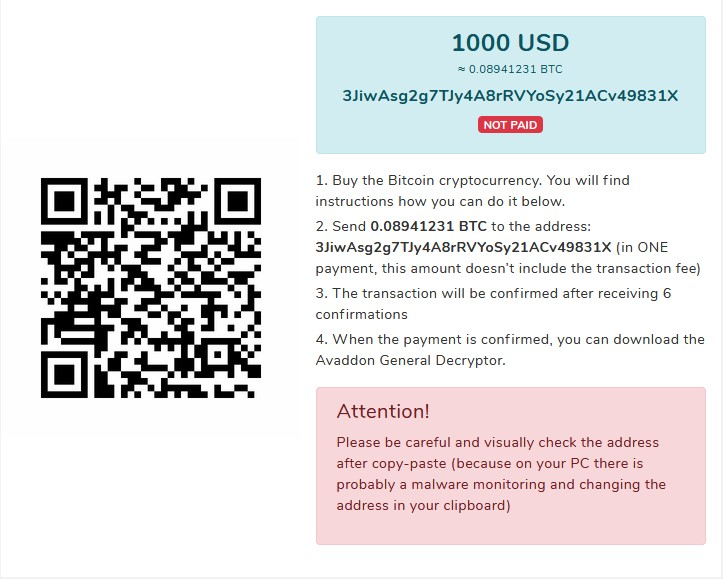
After that, Avaddon notifies a victim about the decryption price, time left to pay with the starting price, and how to pay the ransom to BTC wallet: 3JiwAsg2g7TJy4A8rRVYoSy21ACv49831X.
Conclusion
Avaddon follows the current ransomware trend by having its own data leak site. It changed its extension from .AVDN to the random sequence of characters. The encryption scheme has two hardcoded master keys (AES and RSA), which suggests that the creator of Avaddon is not experienced in ransomware development. The ransomware gets equipped with the privilege escalation technique and can be considered as a serious threat to target organizations.
Detection by Acronis
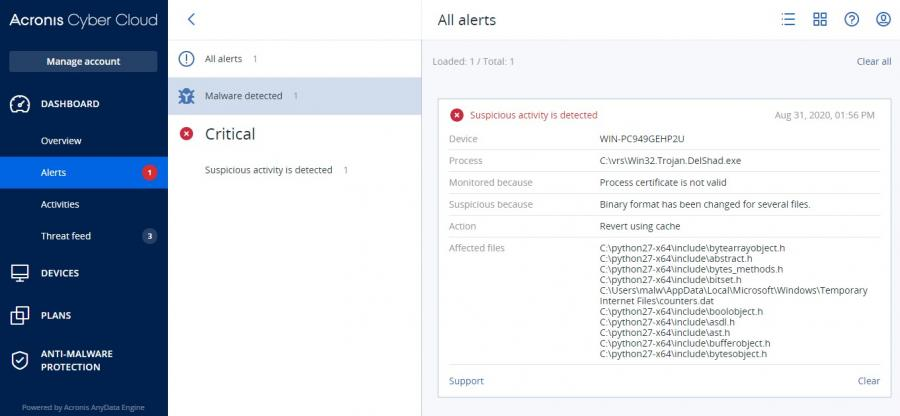
IoCs SHA256: E24F69AA8738D14B85AD76A1783D51120B8B6BA467190FE7D8F96AD2969C8FDF api.myip.com 104.31.66.68 Acronis Active Protection has successfully stopped the attack and restored the encrypted files.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



