Data can be lost for a variety of reasons and the cost of data loss varies depending on the event type, the industry, and the location
For example:
- A data center outage costs U.S. businesses an average of $7,900 per minute.
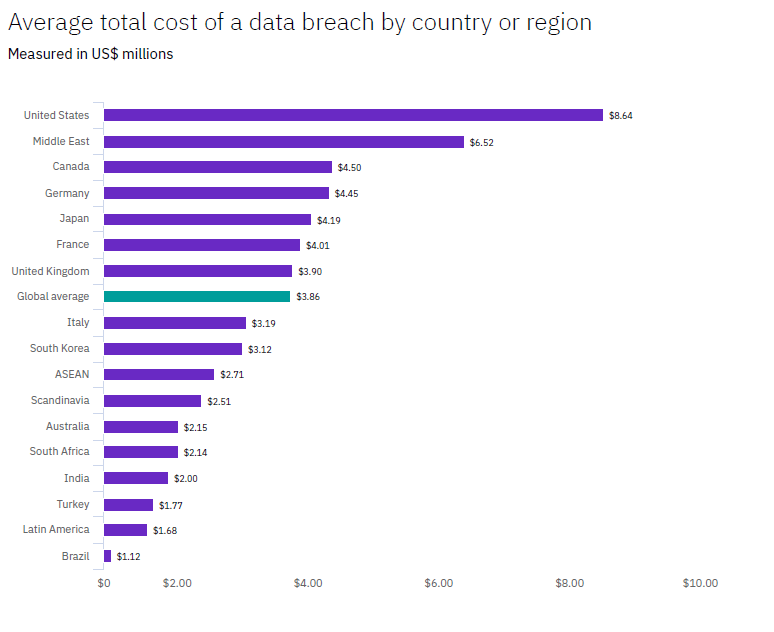
- The global average cost of a breach in 2020 was$3.86 million or $141.00 per data record. See Figure 1.
- The average cost of a breach in the U.S. in 2020 was $8.64 million. See Figure 1.
- The average cost per minute of unplanned downtime is $7,900.
- Small instances of data loss (approximately 100 lost or compromised records) can cost a business an average of $18,120 to $35,730, depending upon the size of the company and the value of the data.
The cost of data loss includes many different elements, includes the cost to replace records, compliance costs, revenue loss, productivity loss, and brand damage. If the loss is the result of a breach, you can also add the costs for investigative/forensic activities and the expenses associated with notifying customers and regulatory agencies.
Causes for data loss
You can lose data in a variety of ways, many of which are beyond the control of the user. Here are some of the most prominent ways data loss can happen and suggestions on how to avoid data loss events or recover if an unforeseen event happens.
System failure/ hardware malfunction
Most data losses occur because of a hard drive failure. Every week in the U.S. alone, 140,000 hard drives fail. Of these crashes, 60% are due to mechanical issues – such as a head crash, overheated drive, or power surge – and 40% are the result of human misuse or mishandling. While you may be able to recover the files from your hard drive if it crashes, there are no guarantees. If your system fails or hardware malfunctions, the best solution to protect your data is by performing regular cloud backups.
Human Error
Humans, both business users and IT professionals, can make mistakes especially if they are new to the organization and/or are not trained. We have all heard the stories of the new IT administrator who accidentally deleted one of the company’s critical databases. But there are other ways humans can corrupt or delete data, including accidentally reformatting hard drives, liquid spills, hardware damage (e.g., dropping a laptop), and so on. Humans can make mistakes, but human error can have even more serious consequences if a disgruntled or departing employee decides to delete or corrupt your systems and data.
Human error is one of the top two reasons for data loss, so you do not want to underestimate the importance of training both your business users and your IT staff. It is also important to immediately exit a disgruntled employee from the office and/or immediately remove all IT privileges so that the employee cannot access the system and cause damage.
Proper training is vital to ensuring your data and systems are safe. Be sure your employees understand important IT practices and policies, including your organization’s backup policies, what to do if they corrupt or delete a file, when to contact an IT expert, etc. Automation and workflow will help in reducing manual errors as well since it takes the decision-making process away from the employee.
Software Corruption
Software can get corrupted when a problem – such as a power surge or power loss – happens when a user is working with or saves a document. An uneducated user can also corrupt their software by not properly shutting down their computer or deleting/changing registry keys or system partition files, etc. To minimize software corruption, each user should:
- Follow procedures for properly shutting down the applications before powering down.
- Regularly save documents as you work on them.
- Always use a surge protector.
- Never change or delete application codes and files.
If your software and/or data is corrupted, your best bet for quick recovery is an image-based backup, which preserves a full copy of a PC or laptop’s operating system, applications, and data.
Malware or virus infection
There are countless ways that your systems can be infected with malware or a virus. Without the proper training, your employees can accidently click on links from spam and phishing emails and Business Email Compromise (BEC), spoofing, ransomware, and zero-day attacks. Once infected, an attacker can not only infect one target (e.g., endpoint device) but can gain access to your corporate network and spread the malware to other endpoints. If your organization is a victim of a ransomware attack, you can lose critical data.
The only way to detect and stop a cyberattack – especially zero-day attacks – is with modern cybersecurity software that incorporates next-generation, AI-based antimalware.
Legal consequence of data loss
One of the major consequences of a data loss or breach are compliance fines, penalties, and lawsuit settlements. Since 2013, there have been over 20 breaches, costing big brand companies between $1 million and $575 million. Here are some examples of organizations that had to pay big time.
How to prevent data loss with a single platform software?
Acronis Cyber Protect Cloud is a one-of-a-kind solution that delivers complete cyber protection for modern threats, bringing together backup and data protection; next-generation, AI-based antimalware; and protection management into a single, integrated solution. Key features include:
Next-generation anti-malware with AI-based static and behaviour detection combined with exploit prevention and URL filtering to counter known and unknown threats, including zero-day malware and ransomware
Image-based backups let you recover to any environment, providing flexible recovery options to better support disaster recovery
Cloud Disaster recovery is provided by Acronis Cyber Protect Cloud Advanced Disaster Recovery, which provides complete data and infrastructure protection and recovery for any environment, allowing you to quickly failover and run your systems in the Acronis Cloud.
Remote work protection to keep remote workers productive and protected with secure remote access to machines, remote wipe, prioritized patching, and protection against exploits for collaboration tools, etc.
Vulnerability assessments and cloud patch management functions to help you identify vulnerabilities before patching and prioritize patch management based on criticality
Protection for all key files with Acronis’ comprehensive Data Protection Map, which provides detailed information about stored data on your machines, detects whether the data is protected or not, and provides you with remediation options
Real-time protection of important documents with Continuous Data Protection, which immediately saves all changes to critical files, even between backups, for near-zero RPOs
Post-malware-attack recovery with integrated anti-malware scans and patch updates of backups
Auto-response to emerging threats based on real-time alerts from Acronis Cyber Protection Operation Centers
If you are concerned about data loss and looking to minimize your organization’s exposure to cybersecurity attacks – even zero-day attacks – Acronis Cyber Protect Cloud is the best choice available on the market to protect your systems, applications, and data no matter what happens.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



