Remote access to business environments has become a vital part of everyday work during the COVID-19 pandemic. One of the common ways an employee like a tech support staffer can connect to a remote employee’s work computer is the Remote Desktop service, which has some well-known security vulnerabilities.
One widely-used remote desktop service, Microsoft’s Remote Desktop Protocol (RDP), is susceptible to DLL Side Loading attacks, in which hackers exploit the lack of an integrity check to replace a legitimate Windows dynamic-link library (DLL) with a malicious copy under the same name that is then loaded by the importing process.
Hacking Microsoft’s RDP service
Microsoft’s RDP service is enabled via the Microsoft Terminal Services Client (MSTSC) that then explicitly loads the “mstscax” DLL from the “C:\Windows\System32” folder without providing mandatory validation. As a result, attackers can replace this DLL with a malicious one if they have the necessary Windows system administrator privileges.
Another way to execute the attack is to drop the legitimate executable “mstsc.exe” in another user’s folder along with a malicious “mstscax” DLL. The executable does not use the full path to load the dynamic library, so a DLL placed in the same folder with the dependent executable will be loaded first in accordance with the Windows search order mechanism. This technique is similar to DLL Side Loading and is known as DLL Search Order Hijacking.
The DLL Side Loading attack was used, for example, in a nation-state cyberattack against Pakistan in 2013, when Google Updater (a Google utility for downloading and updating Google Pack, a bundle of Google and third-party applications and utilities) was used to load a malicious version of the “goopdate” DLL in the same folder. Once executed by Google Updater, the rogue “goopdate” DLL decrypted and executed the Win32/Darkshell.D backdoor on the victim’s computer.
In both examples, the executable loaders (mstsc.exe, GoogleTool.exe) were digitally signed by Microsoft and Google, thus helping attackers to bypass antivirus defenses.
The DLL Side Loading technique is known to be used by several malicious state-sponsored hacking groups to mount advanced persistent threat (APT) attacks, including APT3 (attributed to China's Ministry of State Security), APT19 (a Chinese-based threat group), APT32 (the Vietnam-based OceanLotus Group), and APT41 (another Chinese state-sponsored espionage group) as well as in the popular PlugX remote-access Trojan used for criminal cyberattacks.
Coronavirus increases Zoom attacks
With the advent of the COVID-19 pandemic, the Zoom virtual conferencing platform has attracted unwanted attention for several potential security risks associated with known vulnerabilities. Vice.com reported that two zero-day vulnerabilities – security holes that vendors were not aware of and thus had no patches for – were available on the Dark Web market: one for Windows and another for macOS. The Windows RCE (Remote Code Execution) exploit is currently for sale for $500,000.
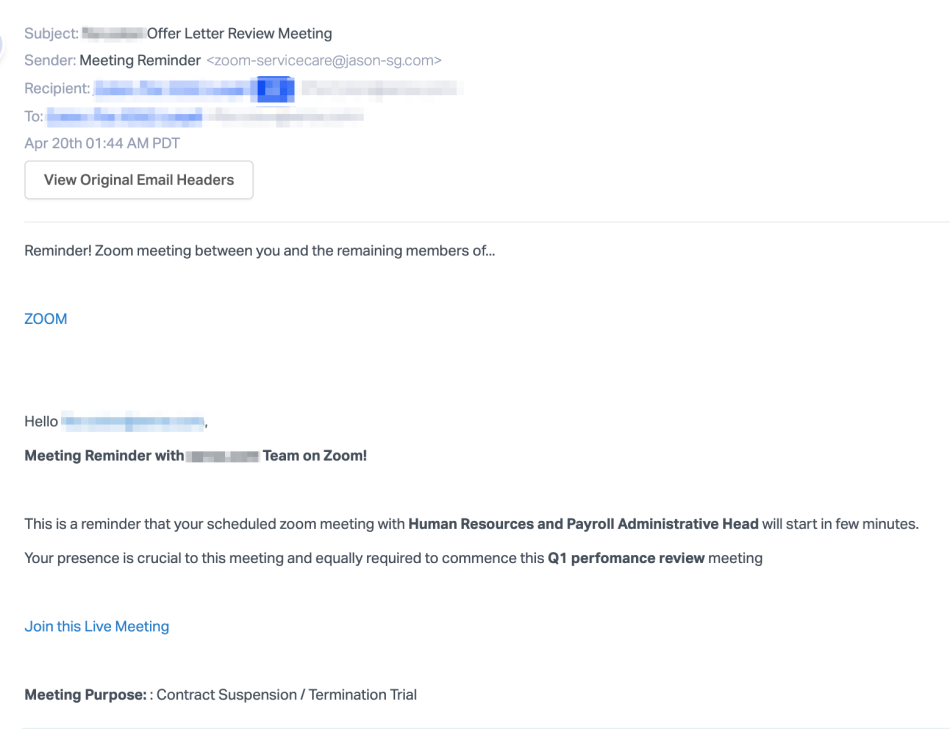
Zoom also became a target of a recent phishing campaign aimed at stealing service credentials. Phishing emails were delivered to more than fifty thousand mailboxes, targeting Microsoft 365 users with a fake email invitation to an upcoming Zoom call with the human resources department to discuss a performance review (a topic designed to induce anxiety in the victim that might crowd out their normal wariness of clicking on an email link).
Source: abnormalsecurity.com
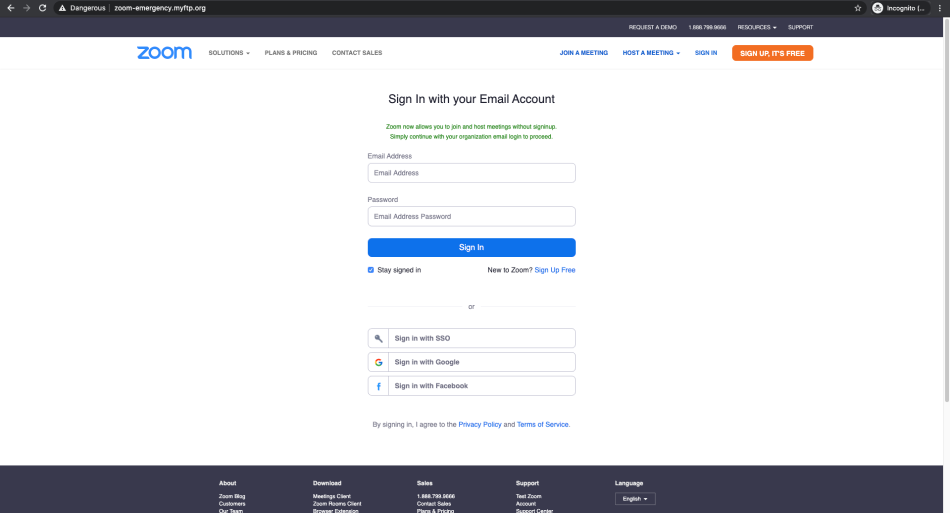
The meeting hyperlink hides the URL “https://zoom-emergency.myftp.org/?email=< target email >” and brings the victim to a bogus Zoom login page that harvests their logon credentials.
Source: abnormalsecurity.com
Source: Virustotal.com
Attacks that steal user credentials for re-use in phishing attacks like this one are widespread. A 2019 report by the Internet Society’s Online Trust Alliance notes that over 2.2B stolen credentials are available in the wild. These can also be used in credential stuffing attacks, in which attackers attempt to use stolen user names and passwords on wide variety of targets, counting on users to commit the common security lapse of re-using passwords across multiple accounts. That can be financially disastrous if one of those sites is the victim’s online banking account, and a different, equally serious problem if their work account includes IT admin privileges.
Final thought
To sum up, the COVID-19 pandemic has significantly changed the threat landscape, highlighting numerous security and privacy risks associated with remote work operations, including remote access to internal company servers and virtual conferencing. Therefore, business and IT leaders must act with urgency to implement cybersecurity measures that protect remote workers and their sensitive data against cybercriminals and malicious state-actors.
These include installing behavioral anti-malware measures that can detect and terminate zero-day attacks, enabling multi-factor authentication, and enforcing online meeting access controls so that only authorized users can join video and audio conferences. Given that a larger remote workforce seems likely to survive into the inevitable post-pandemic world, immediate investments in these defenses will continue to reap long-term cybersecurity dividends.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



