At the moment, scammers are trying to cash in by sending out emails that promise pandemic relief money. The emails impersonate official entities such as the U.S. Federal Reserve or other official institutions.
Several countries have issued programs to help businesses and citizens to receive money from the government in order to overcome the problems created by the new coronavirus outbreak, which are giving criminals an easy way to get anxious people to hope emails. With subject lines like “Receive Payment” or “Relief Payment Form”, users are motivated to click on a link that redirects to a phishing website, which tries to steal personal information or online banking credentials. Other email variants use these stimulus bills as bait to deliver a password protected “COVID 19 Relief.doc” document that contains a financial trojan or ransomware.
In addition, we still see waves of classic COVID-19 themed malware threats making the rounds. One such threat example that we came across recently dropped a combination of ransomware and infostealer malware.
Infostealer and ransomware delivered at once
This infostealer threat has been distributed through fake websites that impersonates a legitimate Windows system utility tool: wisecleaner[.]best, for example. If the user clicks on a link to download any of the offered tools, they get served a downloader, which downloads further payloads from trynda[.]xyz, trynda1[.]xyz, trynda2[.]xyz. Depending on the configuration, the server will decide which payload to serve to the victim.
We have seen similar variants being distributed in the past on social media and through links to file share sites.
In the analyzed sample, a CoronaVirus ransomware and a variant of the KPOT infostealer was downloaded.
CoronaVirus ransomware
This small 44KB threat is a simple, but effective ransomware. It copies itself with a random name to %AppData%\Local\Temp\vprdh.exe and sets a registry key under \Windows\CurrentVersion\Run. Once the dropped file executes, the original file will be deleted.
Like most ransomware, the threat attempts to delete local backups and shadow files by issuing the following system commands:
C:\Windows\system32\VSSADMIN.EXE Delete Shadows /All /Quiet
C:\Windows\system32\wbadmin.exe delete systemstatebackup -keepVersions:0 -quiet
C:\Windows\system32\wbadmin.exe delete backup -keepVersions:0 -quiet
Next, it will start encrypting files. Each encrypted file will be prepended with the string coronaVi2022@protonmail.ch__ while leaving the extension.
In addition, it changes the name of the hard disk to CoronaVirus.
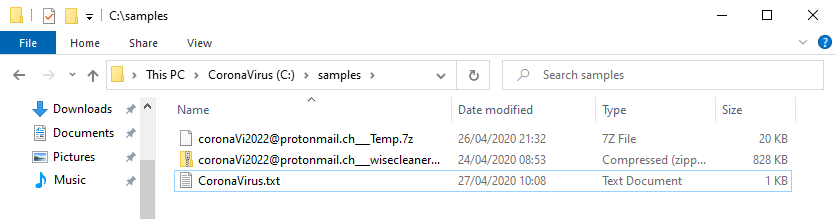
In each affected directory, a text file name CoronaVirus.txt is created with the payment instructions. The ransom demanded is 0.008 bitcoins, which is roughly $60 at the moment. This is unusually low for ransomware and could be an indication that the author's primary motivation is not about profits. On the other hand, it could be that they want to be cheap and affordable so their victims are more willing to pay quickly.
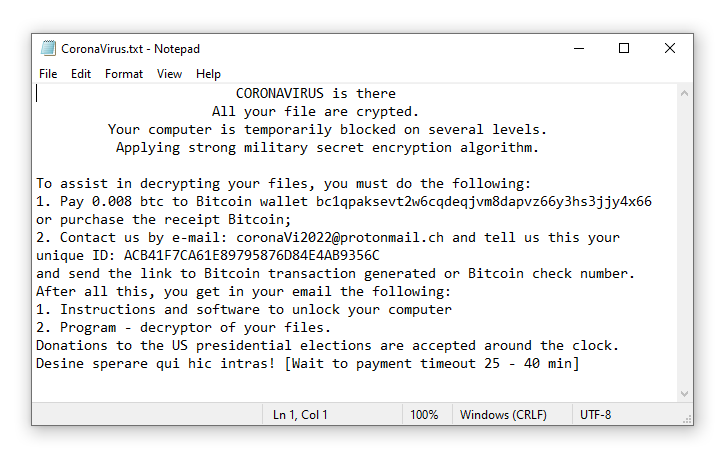
The ransomware also drops a small DOS executable into the temp folder and registers it under the BootExecute registry key in order to display the payment instruction message on the next computer reboot. Depending on the system configuration, this will not work, so no boot message being displayed. Nevertheless, once the ransomware has finished encrypting the files, the computer will automatically be restarted.
The KPOT infostealer
The second payload that was dropped is a password stealer called KPOT. The malware can steal cookies and stored passwords from different browsers, passwords from installed games (including Steam), communication software like Jabber and Skype, and FTP and VPN credentials. Once the malware is finished with its work, it deletes itself with the following command line.
cmd.exe /c ping 127.0.0.1 && del C:\temp\kpot.exe
Final thought
This coronavirus-themed attack clearly shows that ransomware has long ago evolved away from pure data encryption. High-profile, targeted ransomware groups such as Maze and DoppelPaymer have specialized in exfiltrating data and leaking it if the victim does not pay the ransom. This change in approach adds extra motivation to the criminals, especially if all data they would otherwise encrypt can be restored from backups.
This simple CoronaVirus example shows that cybercriminals other than those groups are trying to maximizing their profits as well. This is not a new strategy, a few years ago we saw ransomware attacks installing financial trojans and password stealers as well. The encryption attack could be a diversion, drawing attention away from the data leak, or it could be an attempt to increase the total profits. Either way, it is a good reminder that today’s threats require a comprehensive cyber protection strategy, going beyond standalone backup.
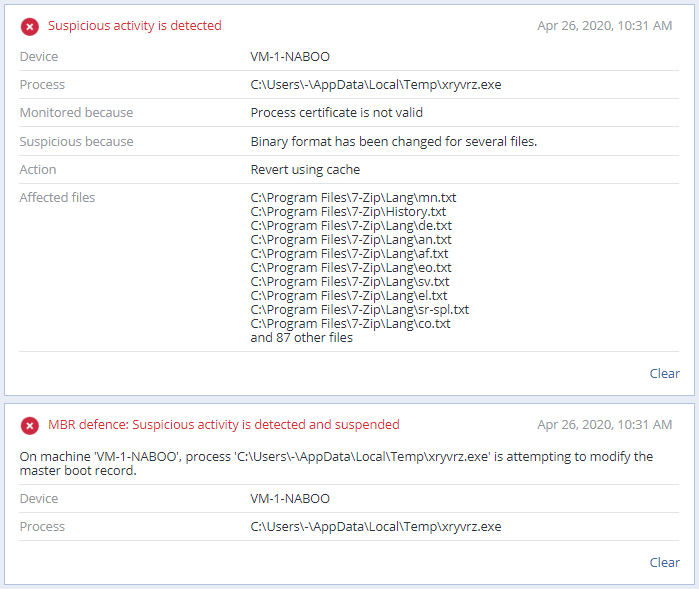
The good news is that Acronis Cyber Protect proactively blocks the CoronaVirus ransomware with its machine-learning-assisted heuristics and any files that were modified during the attack are immediately restored by the solution.
IoC file hashes
CoronaVirus Ransomware: 3299f07bc0711b3587fe8a1c6bf3ee6bcbc14cb775f64b28a61d72ebcb8968d3
Kpot infostealer: a08db3b44c713a96fe07e0bfc440ca9cf2e3d152a5d13a70d6102c15004c4240
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



