
As we already covered, May 12 marked the start of the WannaCry ransomware worm attack (also known as WCry and WanaCrypt0r 2.0) that crippled more than 200,000 Windows machines around the globe. Initiated on Friday, just before the weekend, the attack hit victims on a massive scale, affecting a wide range of organizations, including telecoms, transport companies, government law enforcements and hospitals. The global zero-day ransomware epidemic WannaCry attacked systems in more than 150 countries, making it the first ransomware epidemic of its kind.
There are no reports of massive home computer infections yet. This is likely because the majority of home users are running Microsoft Windows 7 or Windows 10 operating systems with automatic updates turned on … and the patch to prevent this kind of infection was released by Microsoft in March.
Despite the great number of businesses (and however many home users) that were affected by WannaCry, the situation could have been much worse if not for Acronis. That’s because Acronis has developed a New Generation technology that proactively prevents zero-day infections, called Acronis Active Protection™, which protected many computers from this damaging ransomware.
Anyone who had Acronis Active Protection enabled in their backup was safe during the recent attack. Consumers have been able to get it since January through Acronis True Image 2017 New Generation personal backup, and for corporate users, the anti-ransomware technology is implemented in Acronis Backup 12.5, due to be released later on this month (beta available now).
Those companies that had full backups of their data were able to recover from ransomware without paying the ransom. Since WannaCry also has the capacity to encrypt backup files, Acronis is the only backup vendor that is able to defend all data – backups, backup agents running on Windows, and cloud copies with Acronis Active Protection.
What you should know about WannaCry
WannaCry is the first ransomware worm, which means it not only works as ransomware, but also tries to infect as many systems as possible, scanning the network and spreading itself. It is very difficult to detect with traditional security products because it exploits the recently revealed Microsoft operating system vulnerabilities and deploys stealthy methods of self-distribution. It encrypts all local storage devices and network shares, so its worm-like capabilities make it extremely dangerous to companies, organizations and home users. It also easily crosses organizational boundaries by using two vectors – the traditional e-mail attachment vector of infection and the new worm-like distribution.
As Acronis predicted, we are witnessing a new age of ransomware behavior: WannaCry targets local backup copies, directly attacking Microsoft Volume Shadow Copy Service (VSS) available in every copy of Microsoft Windows, and deletes whatever Shadow Copies it can find. It uses strong encryption algorithms, and the affected data cannot be decrypted by any third-party tool in a reasonable timeframe.
Currently, we observe the attack on Windows devices only, but similar exploits may exist in other operating systems. We predict that future attacks of the same scale, targeting other devices and operating systems, are only a matter of time.
Wide range of victims is not a random choice
Cybercriminals chose their victims wisely, targeting companies that can’t afford any downtime and will be forced to pay the ransom: telecoms, public transport companies, hospitals, schools and universities, and law enforcement services. We also see that this time the bad guys have lost their fear completely, attacking law enforcement services, including the Russian Ministry of Internal Affairs.
Here is just some of the affected companies and organizations:
- NHS (UK) turning away patients, unable to perform x-rays. (list of affected hospitals)
- Nissan (UK) http://www.chroniclelive.co.uk/news/north-east-news/cyber-attack-nhs-latest-news-13029913
- Telefonica (Spain) (https://twitter.com/SkyNews/status/863044193727389696)
- Power firm Iberdrola and Gas Natural (Spain)
- FedEx (US) (https://twitter.com/jeancreed1/status/863089728253505539)
- University of Waterloo (US)
- Russian Ministry of Internal Affairs & Megafon (telecom company) (Russia) https://twitter.com/dabazdyrev/status/863034199460261890/photo/1
- VTB (one of the biggest Russian bank) https://twitter.com/vassgatov/status/863175506790952962
- Russian Railroads (RZD) https://twitter.com/vassgatov/status/863175723846176768
- Portugal Telecom
- Sberbank Russia (biggest Russian bank)
More information can be found at https://en.wikipedia.org/wiki/WannaCry_cyber_attack#List_of_affected_organizations
How is WannaCry Ransomware distributed?
WannaCry infiltrates corporate or private/public networks through spam email campaigns with malicious attachments containing macros or the exploit link to the original dropper. The dropper starts the infection as soon as it’s executed. Currently, there are no artifacts of this sample, but all analysts, including Microsoft’s, agree on this method.
The functionality of WannaCry depends on two supposedly leaked cybersecurity scripts developed by a third-party organization: DOUBLEPULSAR backdoor and ETERNALBLUE exploit. ETERNALBLUE injects DOUBLEPULSAR in the system and DOUBLEPULSAR uses the kernel mode driver SRV.SYS (SMB File Server) vulnerability that allows the injection and execution of arbitrary DLLs in almost any process in the compromised system.
As soon as the deadly program is installed, it starts its worm-like activity, scanning the network, checking port 445 and looking for already installed DOUBLEPULSAR backdoors. Then it sends the malicious payload that does the same, spreading like the fire in the forest. If the attacked system does not contain the DOUBLEPULSAR backdoor, it injects it there first using the ETERNALBLUE exploit.
Under the hood of distribution mechanism
WannaCry checks for the presence of a special “killswitch” domain, if found, it exits (there was a temporary cure that mitigated the epidemic after someone registered the sinkhole domain). If the “killswitch” domain is not found, it starts loading its modules, registers the service, scans random IPs for 445 ports, checks for the presence of the DOUBLEPULSAR backdoor and prepares the packet for injection.
The packet construction is implemented in the following function, we named it initNetworkInjectingExecutables in pseudocode. initNetworkInjectingExecutables actually reads the loader DLL from the resource of the worm, constructs the packet for injection, appending the worm payload to the loader, and sends it to the compromised system port. There the loader will get control due to the present DOUBLEPULSAR and execute the payload. This will be repeated on the compromised system, setting the fire in the wild.
New variants
Two new samples already appeared after the initial attack. One (SHA256: 32f24601153be0885f11d62e0a8a2f0280a2034fc981d8184180c5d3b1b9e8cf) has another name for “killswitch” domain. In another one (SHA256: 07c44729e2c570b37db695323249474831f5861d45318bf49ccf5d2f5c8ea1cd) the “killswitch” is completely turned off but the archive is corrupted and only the worm functionality is working. What is interesting, the “killswitch” was simply patched with empty URL string keeping the rest of the code unchanged. But payload from tasksche.exe was partially changed:
It resulted in malfunctioning of the sample. Whether that was done by mistake or on purpose is still not clear.
Without proper backup, your files will be lost
The injected payload on the compromised system deletes all VSS shadow copies using all available methods:
It also disables the recovery console of the attacked system:
How WannaCry encrypts files
The payload schedules the encrypting program functionality: a cryptor is extracted from the resources of the payload, the filename is tasksche.exe. The cryptor scans all drives and shares on the system, looking for the files, matching its own table of extensions, and then encrypts them using the RSA 2048-bit encryption. It also creates a new file directory Tor/ where it stores tor.exe and associated files. There are also two files dropped: taskdl.exe and taskse.exe. The former does the cleanup work and the latter launches @wanadecryptor@.exe. The launched program shows the ransom demanding threat screen and performs communications via the Tor network.
More than 160 different file extensions are supported:
.doc, .docx, .xls, .xlsx, .ppt, .pptx, .pst, .ost, .msg, .eml, .vsd, .vsdx, .txt, .csv, .rtf, .123, .wks, .wk1, .pdf, .dwg, .onetoc2, .snt, .jpeg, .jpg, .docb, .docm, .dot, .dotm, .dotx, .xlsm, .xlsb, .xlw, .xlt, .xlm, .xlc, .xltx, .xltm, .pptm, .pot, .pps, .ppsm, .ppsx, .ppam, .potx, .potm, .edb, .hwp, .602, .sxi, .sti, .sldx, .sldm, .sldm, .vdi, .vmdk, .vmx, .gpg, .aes, .ARC, .PAQ, .bz2, .tbk, .bak, .tar, .tgz, .gz, .7z, .rar, .zip, .backup, .iso, .vcd, .bmp, .png, .gif, .raw, .cgm, .tif, .tiff, .nef, .psd, .ai, .svg, .djvu, .m4u, .m3u, .mid, .wma, .flv, .3g2, .mkv, .3gp, .mp4, .mov, .avi, .asf, .mpeg, .vob, .mpg, .wmv, .fla, .swf, .wav, .mp3, .sh, .class, .jar, .java, .rb, .asp, .php, .jsp, .brd, .sch, .dch, .dip, .pl, .vb, .vbs, .ps1, .bat, .cmd, .js, .asm, .h, .pas, .cpp, .c, .cs, .suo, .sln, .ldf, .mdf, .ibd, .myi, .myd, .frm, .odb, .dbf, .db, .mdb, .accdb, .sql, .sqlitedb, .sqlite3, .asc, .lay6, .lay, .mml, .sxm, .otg, .odg, .uop, .std, .sxd, .otp, .odp, .wb2, .slk, .dif, .stc, .sxc, .ots, .ods, .3dm, .max, .3ds, .uot, .stw, .sxw, .ott, .odt, .pem, .p12, .csr, .crt, .key, .pfx, .der
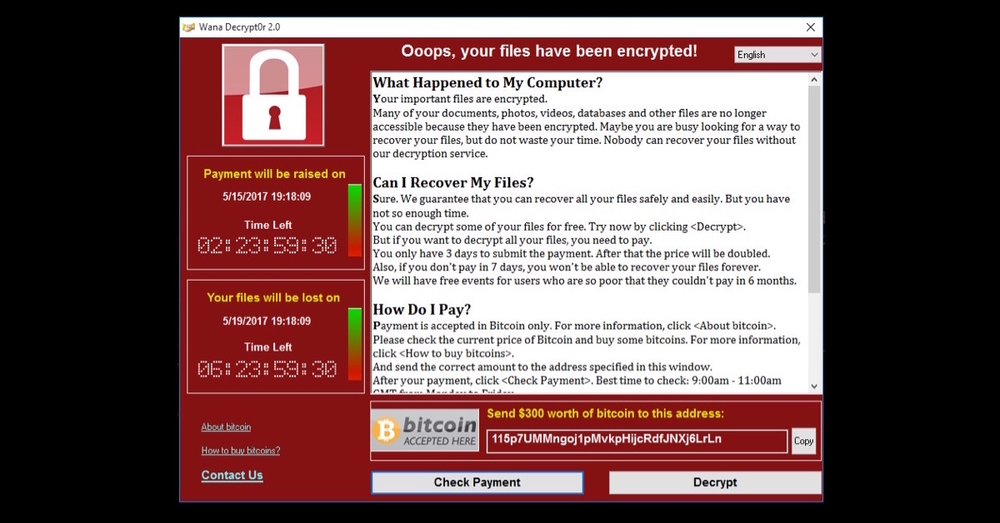
If the system is not protected, the user is presented with the following message:
The user has to either pay and hope that files will be decrypted, or simply lose the data if there is no backup.
How to protect your systems against WannaCry and other ransomware attacks
First of all, all users that updated their Windows operating systems with recent updates (starting from March this year), are protected.
- Have automatic Windows updates enabled. If you have not updated for long time or use an old operating system, check to see if an official Microsoft patch is available and install it as soon as possible. There are patches of XP and Windows 2003 already. Any home and office computer that does not have the most recent updates can be infected.
- Have your Windows machines protected by a modern anti-malware solution. It will help to reduce threat level and potentially stop ransomware.
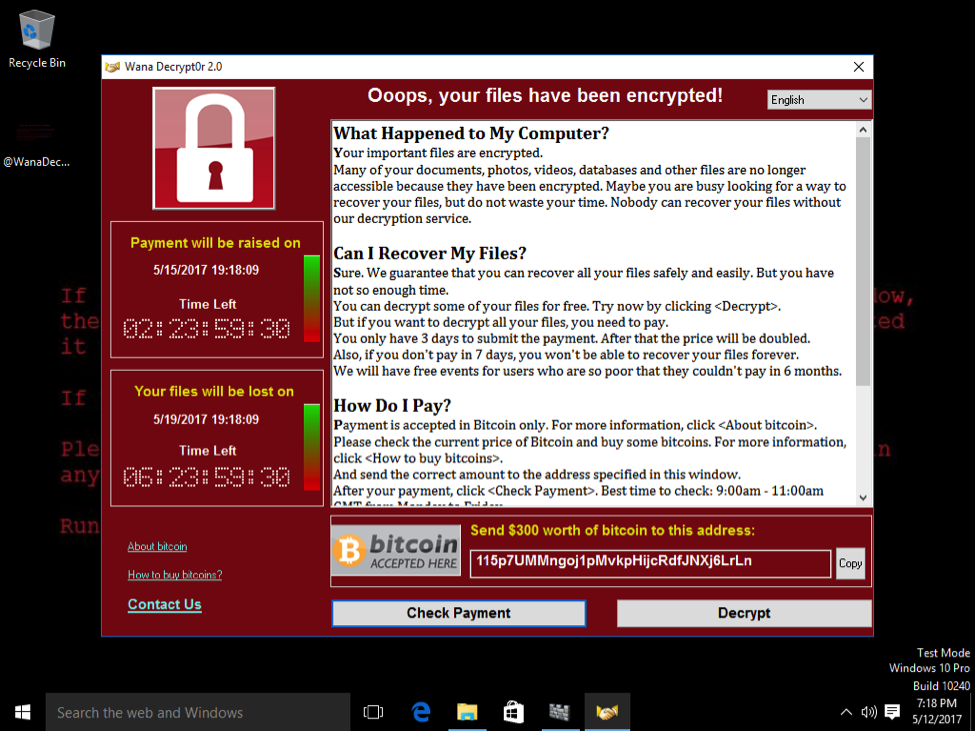
- It is highly recommended to use Acronis products for backup and protection with the Acronis Active Protection feature enabled. It uses advanced heuristics and instant backup/recovery mechanisms to defend data. You can see the screen below that shows the successful prevention of WannaCry by Acronis Active Protection. This works the same way on corporate Acronis product with the Active Protection plan enabled.
WannaCry ransomware is detected on a computer running Acronis True Image 2017 New Generation with Acronis Active Protection enabled.
- As a rule, DO NOT open any suspicious attachments or links in your emails, DO NOT open/click any suspicious links in web browsers, DO NOT visit any websites you don’t know explicitly! Always hover the mouse over the links to make sure they are not fake.
- Pay attention to whether the email that is sent actually has your email address in To or CC field, otherwise DO NOT open it, especially if it contains attachments or links!
- Pay attention to the sender’s email address. Sometimes it may contain a name you may know but the full address might be totally different – which means the address has been spoofed.
- Always have a backup of your system and your important files. We know that WannaCry demanded around 300 USD as a ransom. Yet a backup solution like Acronis True Image 2017 New Generation or Acronis Backup are much cheaper and guarantee the safety of your data. Acronis Active Protection also automatically restores all affected files as you can see on the following screenshot.
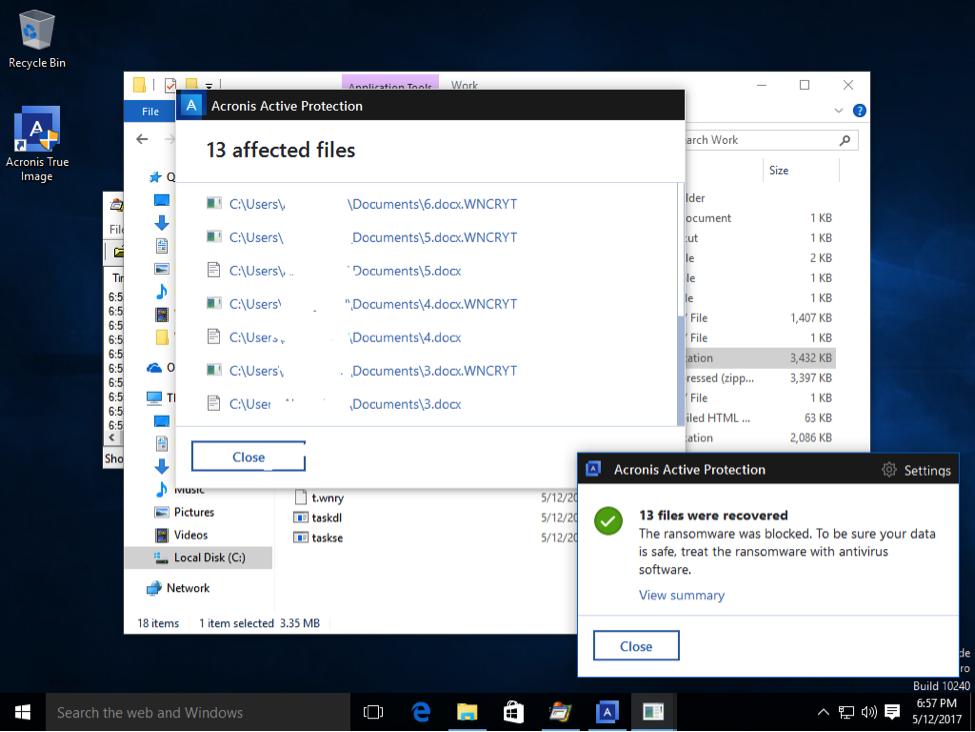
All files are Instantly Restored to their original state by Acronis Active Protection without any ransom paid.
READ MORE: WannaCry Ransomware Just Became a Global Pandemic. Only Acronis Has the Vaccine
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 20,000 service providers to protect over 750,000 businesses.




