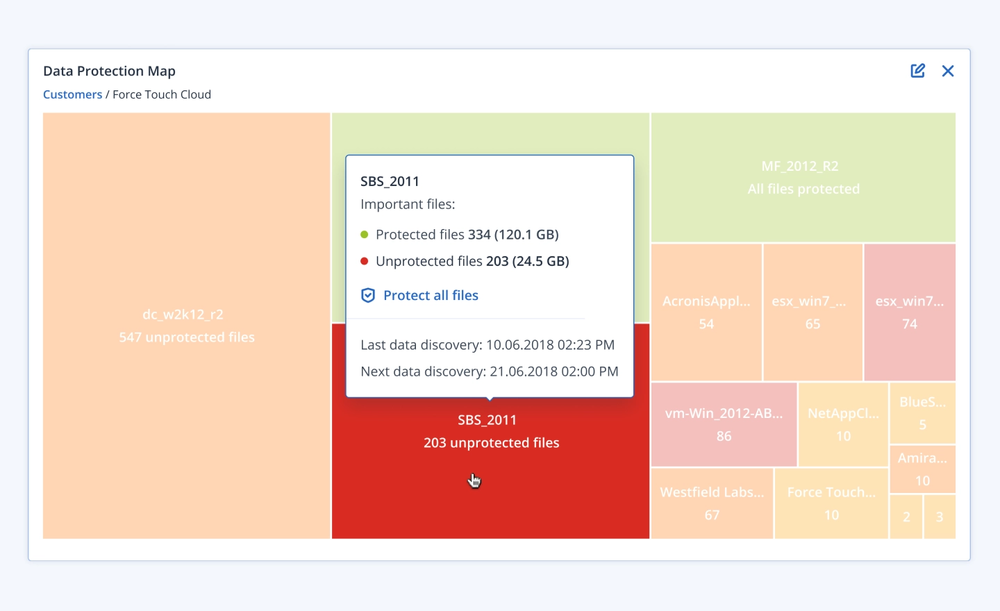
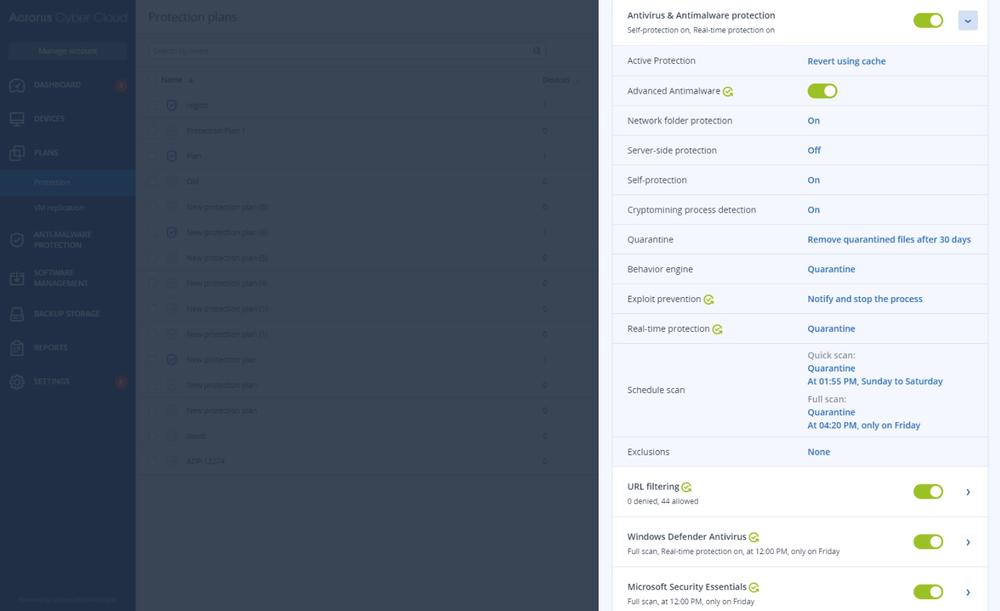
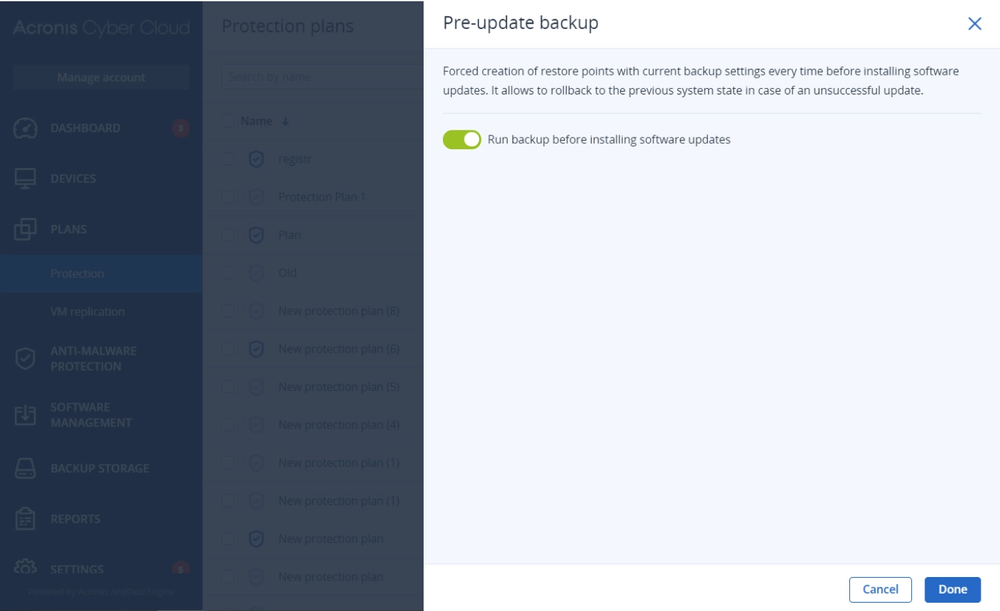
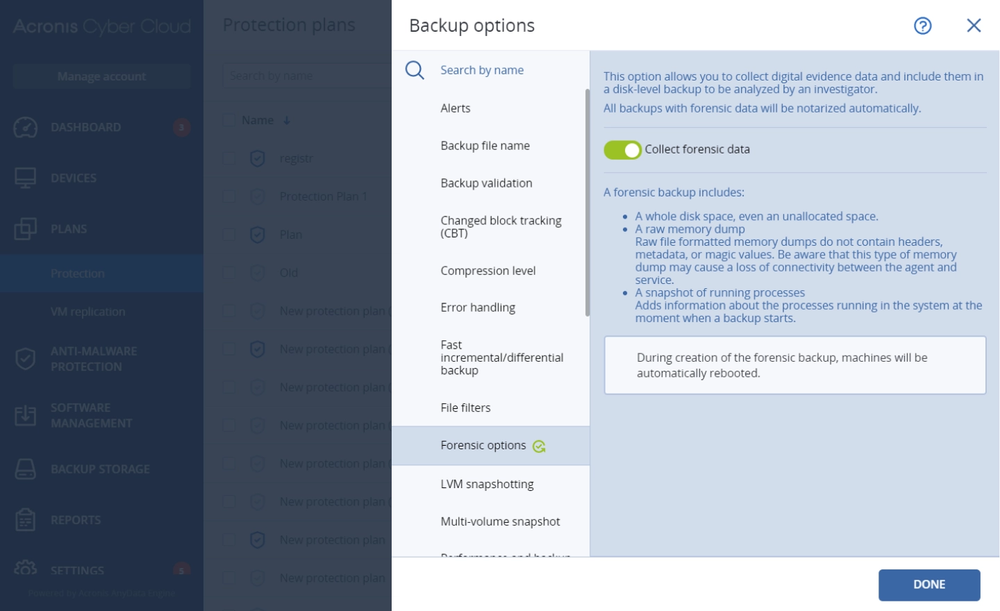
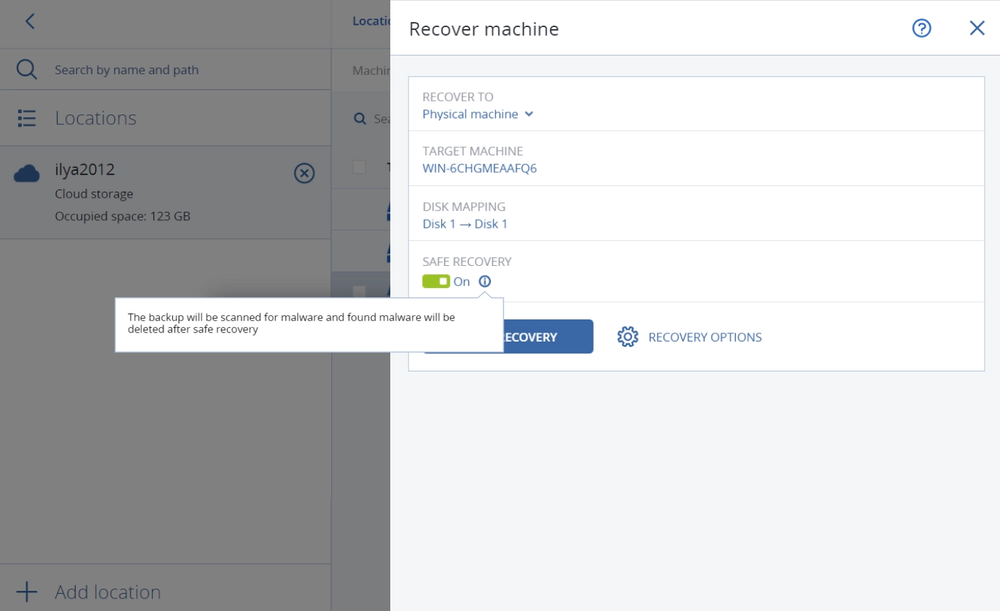
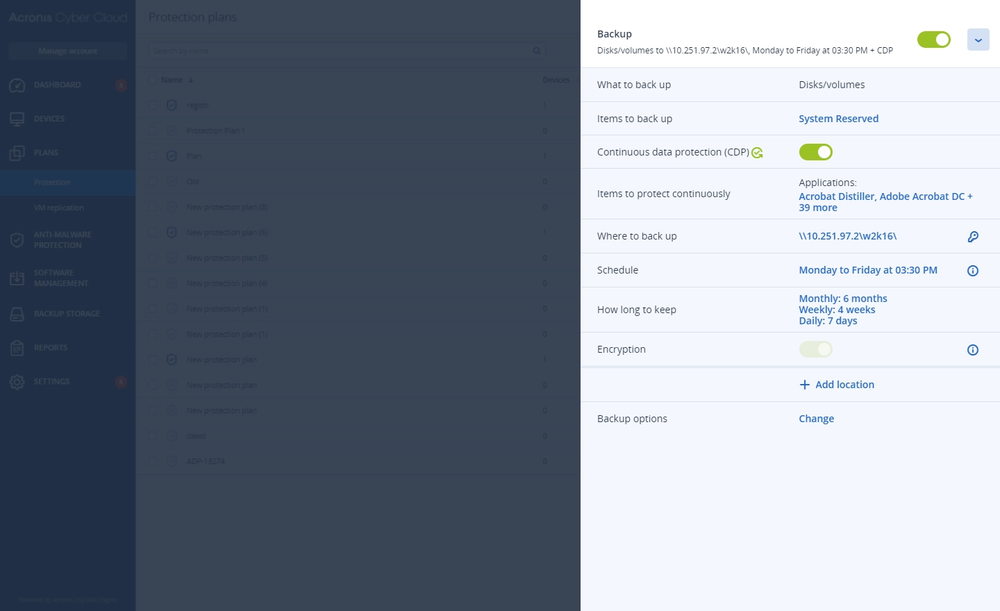
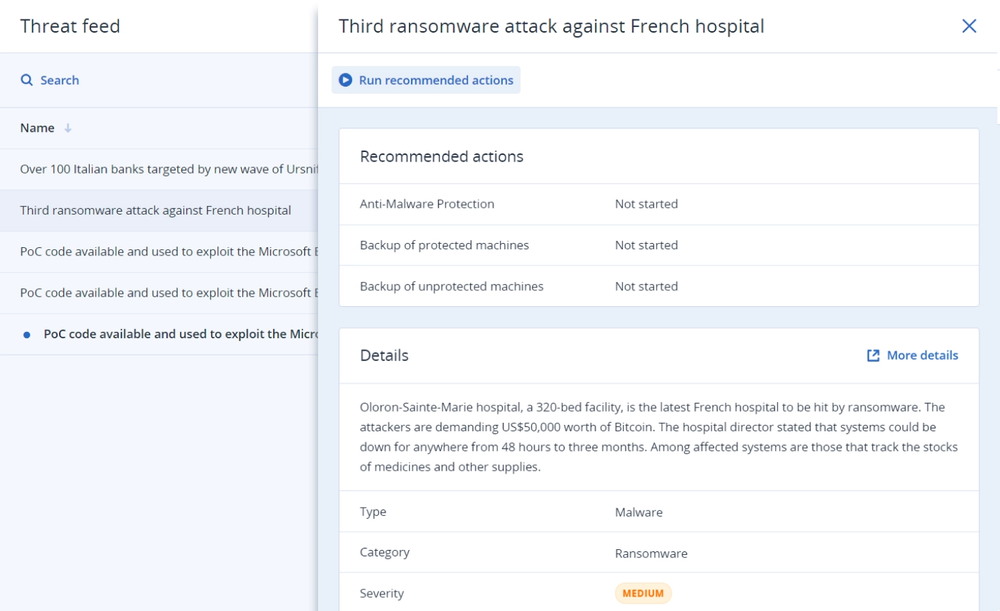
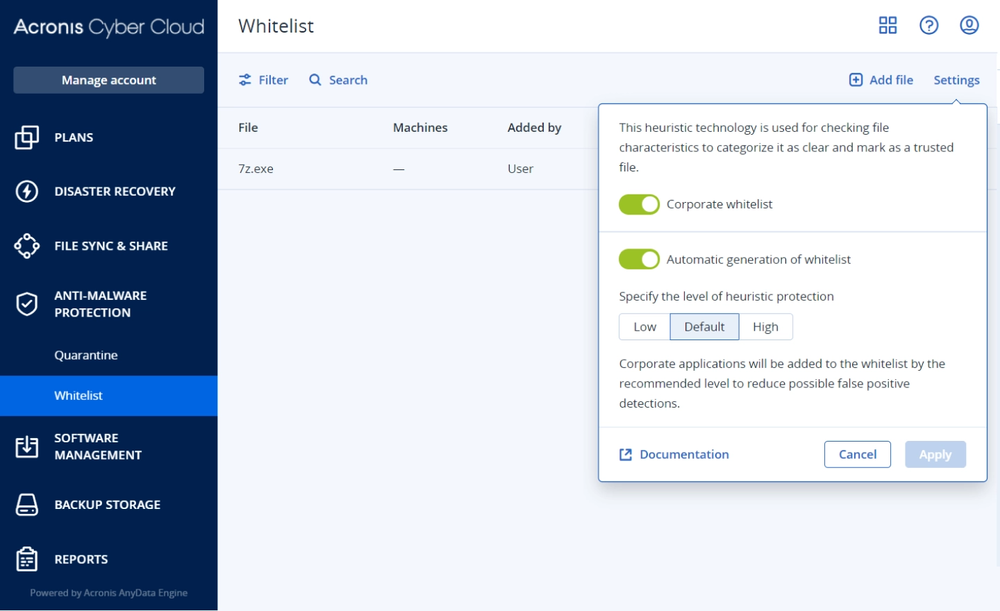
- Gain controlYou control what services you deliver for your customers: security, backup, disaster recovery, automation and management — all with the flick of a switch.
- Consolidate vendorsManaging multiple vendors leads to increased costs, increased risk and added operational overhead. By consolidating vendors, you can perform as efficiently as possible to best deliver services to your clients.
- Reduce training timeWith a single console to manage all of your services, your training time for new technicians is reduced up to 50%.
- World class supportThe Acronis Partner Portal has everything you need to deliver exceptional services to your customers. Pre-packaged marketing campaigns, training and other resources.
Start earning money today — get the full production account of Acronis Cyber Protect Cloud and become an Acronis service provider partner
Acronis Cyber Protect Cloud
Deliver all the cyber protection services your clients seek via one platform and one pane of glass
Our MSP cloud solution easily integrates with common RMM and PSA tools
Acronis Cyber Cloud works with the other systems you already have in place, with native integration with Kaseya, Autotask, ConnectWise Automate, ConnectWise Manage, cPanel, Atera, CloudBlue, Wasabi, HostBill, Odin, Plesk, RackNap, and WHMCS. You can also further integrate and automate with the Acronis Cyber Platform’s RESTful APIs and SDKs.
Why do MSPs choose Acronis Cyber Protect Cloud over other solutions? It’s an all-in-one data protection and cybersecurity platform that enables MSPs to offer more client services at less cost.
Upcoming events
Global data center presence
Help your clients meet their unique needs by storing their data where they choose. With multiple data centers worldwide, Acronis enables you to meet the compliance, data sovereignty, and performance requirements of all your clients.
Discover the platform trusted by thousands of service providers worldwide
- 21,000+service providers
- 150+countries
- 26languages
- 50data centers
- STEP 2
Dive deep into Acronis
- STEP 3
Connect with an expert
Learn More, Earn More with Acronis Academy
Whether you and your team are seeking professional certifications or starting an MSP business, we're here to support you at every stage.

Start learning for Free
New! MSP Academy offers budding and seasoned MSP professionals vendor-neutral training covering the A-Z of managing a successful MSP business.
Train on-demand
Access our most popular sales and technical training courses designed for existing MSPs looking to enhance their cybersecurity skills and knowledge.
Login to Partner Portal
Available exclusively to Acronis Partners. Access our complete Acronis Academy training catalogue and earn your required certifications.
Frequently asked questions
What are the types of cloud services for managed service providers?
Managed service providers (MSPs) deliver a variety of services to their clients. Everything ranging from break-fix services for printers to IT infrastructure (telecom, network, Wi Fi, firewalls) to security services like data backup, disaster recovery and endpoint security.Why are cloud solutions important to MSPs?
Cloud solutions are important to MSPs for several reasons. By leveraging cloud technology, MSPs are able to deliver fast response and ensure end user services are available at any time and any location. In the past, MSPs would often have to physically travel to clients’ offices to deliver services. Now, they leverage the availability of the cloud to ensure their clientscu are always operational and secure.What are the most used cloud services for MSPs?
One of the cloud services most often used by MSPs is data backup and recovery. Having data readily available as needed is only possible through advanced cloud services, where data resides protected, secure and ready to be accessed when needed. In addition to data backup and recovery, MSPs leverage the cloud to deliver security services that protect endpoints from a variety of threats, including ransomware, phishing and credential compromises.What cloud services does Acronis Cyber Protect Cloud offer to MSPs?
Acronis offers basic and advanced functionality for data backup, disaster recovery, endpoint security, automation and management. All of these services are available in a single agent and can be used either individually or in combination.
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.