There are dark and dreadful things that lurk in the shadows of the digital world, ready to bleed your company of data and dollars. This year alone, these ghoulish attacks have cost organizations like yours billions of dollars, weeks of paralyzing downtime, and a frightening loss of reputation.
If you can’t scare up a way to fight back against these monsters, it may not be long before your business becomes their next victim.
We dove into the deepest and darkest parts of the ransomware world to drag the worst we found into the light – including some mysterious attacks that remain unidentified. Uncover some of the most monstrous ransomware strains that creeped and crawled their way into the news this year and then make sure you’re safe from them all with Acronis Cyber Backup.
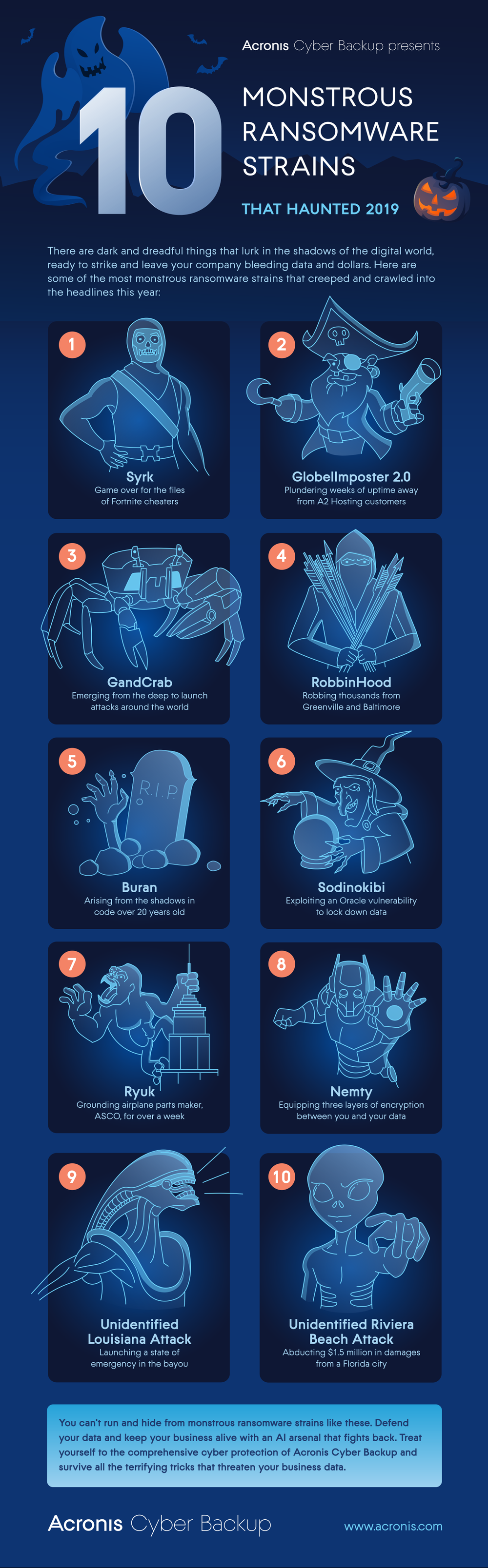
Meet the Monsters from our Infographic
The mad computer scientists at Acronis braved the depths of these cyberattacks to learn how they strike and how to defeat them – so you can live to tell the tale if they come knocking at your door some dark and dreary night.
Explore them all here and share our infographic to protect your colleagues from a haunting ransomware attack of their own.
1.Syrk
Syrk ransomware is aimed at Fortnite cheaters, masquerading as a utility for hacking the game. However, instead of getting the desired aimbot, players download malware that immediately starts encrypting files, adding the ‘.Syrk’ extension to them. It’s an insidious type of threat that anti-malware software is usually bad at dealing with.
2.GlobalImposter 2.0
In April, A2 Hosting reported that a ransomware attack had infected and encrypted some of their Windows hosting servers. To stop this spread, A2 shut down Windows and virtual private servers, but not before the ransomware strain compromised the company’s RDP connection and primary data center. Weeks later, the company and all their customers were still trying to rise from the grave.
3.GandCrab
Launching millions of infections around the world and raking in millions of dollars each week, GandCrab brought terror to the digital world this year. As a pioneer in the world of ransomware as a service (RaaS), this cyberthreat spawned countless others before its developers went into retirement. That retirement was temporary, however – these monsters are already back with new malware attacks.
4.RobbinHood
Unlike many virulent ransomware strains, RobbinHood doesn’t spread via normal worm capabilities. It carefully targets individual machines, shuts down 200 different Windows services, and demands tens of thousands of dollars to unlock them. For maximum impact, RobbinHood has brought down IT systems and public services in major cities: Greenville, NC and Baltimore, MD, so far.
5.Buran
Buran is a new version of ransomware that speaks a nearly dead programming language. It’s code was written in Object Pascal in Delphi IDE, a language that was popular 20 years ago in Latin America and the former Soviet Union. Evolving to avoid detection and analysis, the strain now uses the RIG Exploit Kit to deliver its payload before locking down systems behind three layers of encryption.
6.Sodinokibi
Sodinokibi ransomware exploits an Oracle WebLogic vulnerability (CVE-2019-2725) to gain access to machines. Once it’s gained entry, the malware executes itself with elevated user rights to eliminate any restriction to files or connected resources – making complete encryption and further infection highly likely. While encrypting the victim’s systems it wipes out all backup folders to further encourage payment.
7.Ryuk
Production at ASCO, the giant Belgian airplane parts maker, was halted for weeks due to a pervasive ransomware attack believed to be the Ryuk strain. Nearly 1,000 employees were sent home on paid leave while the company struggled to restore the critical systems that were frozen by the attack, an added expense on top of the lost productivity from manufacturing being down for so long.
8.Nemty
The latest strain of Nemty emerged from a fake PayPal website with indications that it shared DNA with both Buran and GandCrab ransomware strains. Given the overkill 8092-bit RSA key that secures its encryptions, there’s no way to decrypt the files it locks without paying the requested ransom yet. As a result, thousands of dollars have been claimed in the few months the strains been active.
9.Unidentified Louisiana Attack
A wave of ransomware on public schools in the state of Louisiana escalated to such a degree that the governor declared an official emergency to kick-start a response from state-level law-enforcement and technology agencies. While this plan enables the state to focus more on a resolution and less on a media response, it’s no replacement for cyber protection that detects and prevents attacks in the first place.
10.Unidentified Riviera Beach Attack
The city of Riviera Beach, FL paid approximately $600,000 in ransom to regain access to its IT systems this May. In addition, the city invested more than $900,000 into new hardware to try to seal the security gaps that allowed for the attack in the first place. In total, that’s $1.5 million in damage from one attack. What’s worse, by paying this ransom the attackers see evidence that their work is both worthwhile and lucrative.
Avoid the Horrors of Ransomware
Modern businesses need more than silver bullets and a wooden stake to lay these cyberthreats to rest. Cutting-edge cyber protection solutions like Acronis offer your organization the ability to spot the monsters lurking throughout the digital world and actively block them from sinking their teeth into your data and dollars.
Arm yourself against all the ransomware that goes bump in the night with Acronis Cyber Backup today.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



