On Tuesday, October 24, 2017, a new ransomware sample called Bad Rabbit hit Russia, Ukraine, Türkiye, Germany, Bulgaria, USA, and Japan. Russia and Ukraine were hit the most as the infection started through some hacked Russian news websites. Russian media agencies Interfax and Fontanka, as well as transportation organizations in Ukraine including the Odessa airport, Kiev's subway and the country's Ministry of Infrastructure were among the first to catch the infection.
Bad Rabbit is based on NonPetya or exPetr code but is heavily reworked, although the behavior and actual result of infection is pretty much the same. At the same time, we noted that it also contains parts of other ransomware, for example, approaches used in HDDCryptor. But guys behind the Bad Rabbit fixed bugs here and there and combined it all into one, which is quite unique. They also signed the code with a fake Symantec security certificate. Another feature of this malicious software is the ability to collect user passwords on the infected computers and download additional malicious modules.
The ransomware doesn’t use any new tricks, quite on contrary, it relies on a very old malware approach of tricking users into installing a fake Adobe Flash update. Surprisingly, this approach still works, which indicates that cybersecurity awareness is still very low among businesses and consumers. There is still a lot of education needs to be done to make such attacks less effective. Until then, without proper security and data protection measures in place, the risk of falling victim to ransomware remains high.
Bad Rabbit key facts
- Uses pieces of code from NonPetya/ExPetr
- Distributed as fake Flash update requiring manual installation by a user
- Uses system driver for encryption
- Tries to distribute itself via local network in a primitive way
- Replaces MBR and makes PC unusable
- Crashed on Windows 10
- Mainly affected Windows corporate users
Infection scheme and technical details
To launch the attack, cybercriminals hacked some popular media websites and posted a link to a fake Adobe Flash installer, asking users to run the update when they visited the website. Many users fell for the trick, even though security companies for years have been warning people against installing software updates from untrusted sources. It’s also recommended to check all updates with an anti-malware solution before installing, to be sure that they are not hacked or injected with malicious code. Similar fake Adobe software updates were very popular infection schemes years ago and as we see, unfortunately, it continues to be effective now.
The ransomware dropper is distributed from hxxp://1dnscontrol[.]com/flash_install.php. After that, the user downloads install_flash_player.exe file, which needs administrative privileges in the system. Funny enough, it attempts to obtain these using the standard UAC prompt. If started, the dropper extracts a file-level encryption module infpub.dat (which is a dll actually) and a disk level encryption module dispci.exe and kernel mode driver cscc.dat (which is actually legal dcrypt.sys file).
After the user voluntarily infects the machine, Bad Rabbit attempts to spread itself over the local network using a known mimikatz tool which lets you extract Windows credentials from Local Security Authority in open form, as well as an embedded credential list containing some of the worst password examples. Bad guys know that “12345” or “password” have been at the top of the password lists for years and these passwords continue to be effective.
As we already hinted, Bad Rabbit uses two types of encryption – file and disk level. It doesn’t imitate chkdsk.exe like NonPetya did to hide encryption, nor does it use any vulnerability in Microsoft file server srv.sys. Firstly, Bad Rabbit launches file level encryption (infpub.dat via rundll32), if it finds enough files to encrypt. After that, it creates tasks in the Scheduler for launching the dispci.exe to encrypt drives and then forces a system restart. After the first restart, dispci.exe writes an extended loader at the end of the disk, which will get all the control via the malicious MBR later. Finally, the whole disk is encrypted with a legitimate driver, MBR is rewritten and the PC restarts again to display a ransom message demanding 0.05 bitcoin (which is roughly $275).
An interesting point is that under Windows 10 the driver module used for encryption is often causing a BSOD (Blue Screen Of Death) because of the compatibility issues. Another thing is that when it encrypts the file, the file extension stays the same, which can trick the heuristics used by some antiviruses, which react on file extension changes. Bad Rabbit can work offline and this potentially means that the sample can infect other machines when stored and distributed on a flash drive.
The main target for Bad Rabbit are companies and business and as of now, we see that the infection levels are already subsiding. The malicious server is no longer alive and most of the infected sites that hosted the script that dangerous Flash update are currently down or cleaned up. That doesn’t mean, however, that you as a business or individual should relax because a new attack can happen anytime.
Acronis Active Protection detects and blocks Bad Rabbit from day 0
Acronis data protection solutions come with built-in active protection against ransomware — Acronis Active Protection. If you’re using Acronis True Image, Acronis Backup 12.5, or Acronis Backup Cloud, make sure it’s enabled. It will detect the threat, block the attack, and restore the affected data.
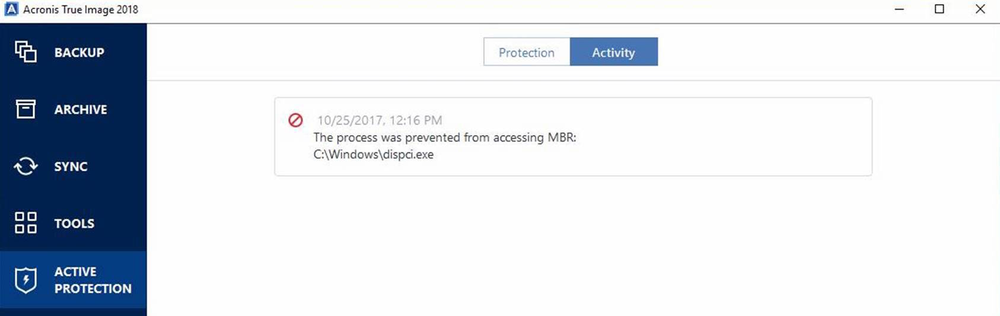
Acronis Active Protection protects the Master Boot Record (MBR).
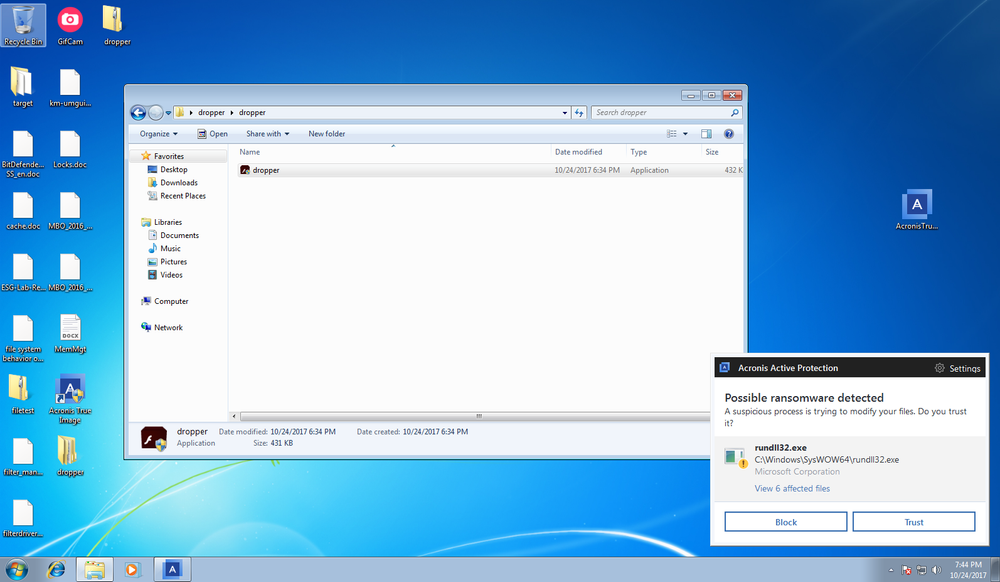
Acronis Active Protection detects and blocks Bad Rabbit ransomware.
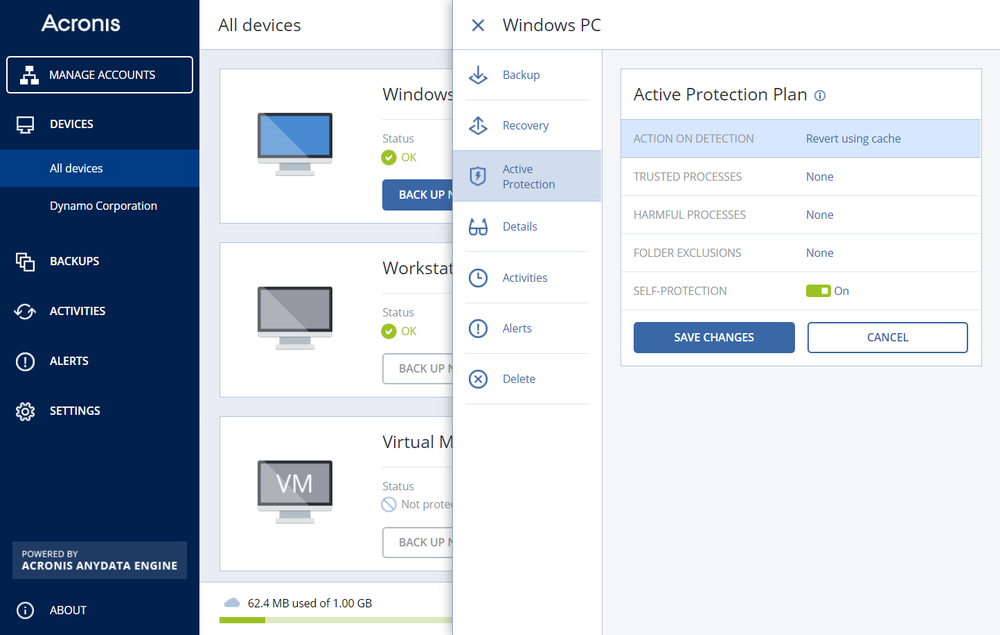
Active Protection settings in the Acronis Backup Cloud management console.
We recommend that you use the following simple security rules:
- Protect your data with a secure backup technology such as Acronis True Image, Acronis Backup 12.5, or Acronis Backup Cloud. These products come with Acronis Active Protection which protects data (and backup files) from ransomware in real time.
- Install a reliable anti-malware solution and enable auto-updates.
- Install regular software updates from trusted websites or through Windows update. Many 3rd party software vendors like Adobe actually update software automatically, so you should not see any requests for updates, especially when reading your favorite news websites. Even better – you can remove Flash at all if you don’t need it.
To find out more about Acronis Active Protection, visit https://www.acronis.com/en-us/ransomware-protection/
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.




