Maze ransomware has been seen executing targeted attacks since at least May 2019 and was supposedly responsible for the attack on Canon on July 30, 2020 resulting in the outage of the image canon cloud storage service. Moreover, the Maze ransomware operator claimed they stole 10 TB of private data as part of the attack on Canon. The Maze operators already published data from Xerox and LG that was stolen during a successful attack in June 2020, as the companies refused to pay a raonsom.
Summary
• Maze ransomware not only encrypts data but it also steals it to publish later if a ransom is not paid. • Canon, Xerox, and LG are among the biggest victims of Maze. • Employs anti-disassembly and anti-debugging techniques. • Does not encrypt systems with a Russian default locale. • wmic.exe call to delete shadow copies is obfuscated. • Sends an HTTP check-in request to C&C server located in ‘91.218.114.0’ network in Moscow, Russia • Uses Mimikatz, Procdump, and Cobalt Strike hacking tools for proliferation.
Delivery and proliferation
Maze ransomware is typically delivered as a result of a targeted attack against organizations that starts with a spear-phishing email that gains access via compromised RDP or VDI (the credentials are usually bought on the Dark Web), and exploits vulnerabilities in VPNs. Once the Maze operator obtains access to the internal network of the organization, it runs Mimikatz and Procdump to harvest passwords stored in the memory and switch to reconnaissance using the Cobalt Strike red-teaming tool.
Self-defense
Maze uses anti-disassembly techniques to harden the code analysis in the disassembler.
The obfuscation techniques include:
- Conditional jumps which redirect to the same location, replacing absolute jump.
- Calls are followed by pushing the return address to the stack and jumping to the caller address.
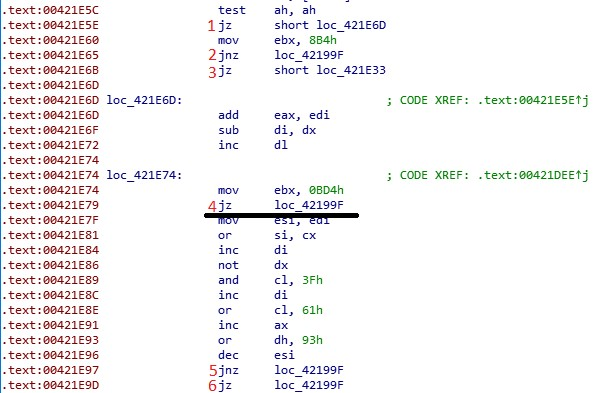
Let's take a look at the first anti-disassembly technique.
The result of this piece of code is jumping to the 42199F location. Here's how it works:
- If the first jump is taken, execution goes to the 421E6D location, where the fourth jump is taken as ZF flag was not changed and execution goes to the 42199F location and code under the jump is unreachable.
- If the first jump is passed, the second jump is taken, because it is opposite to the previous one and code goes to the 42199F location and the third jump is unreachable.
The fifth and sixth jumps can be seen as absolute jumps.
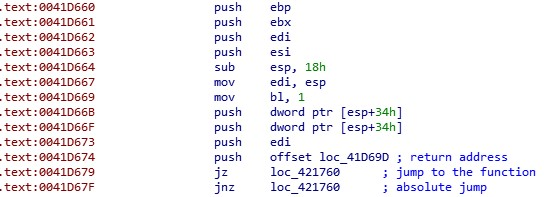
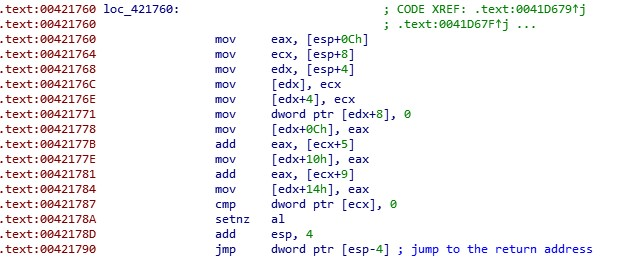
As for the second anti-disassembly technique, Maze pushes the function return address to the stack and then jumps to the function itself. After executing the function it cleans up the stack and retrieves the return address from the stack to leave the function.
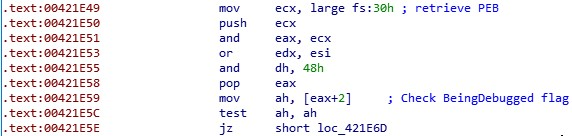
In addition, Maze can detect if its code is being debugged. It checks the flag ‘BeingDebugged’ in its PEB structure, if the process is run under debugger. If so, the code goes into an infinite loop and does no encryption.
Also, Maze kills the processes of the malware analysis tools and office tools by the hashes of the process names.
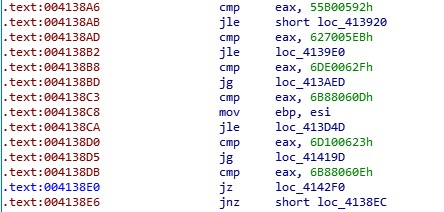
For example, x32dbg has a hash value of ‘5062053B’.

The reconstructed list of the processes is as follows:
- dumpcap.exe
- excel.exe
- fiddler.exe
- msaccess.exe
- mysqld-nt.exe
- outlook.exe
- pipanel.exe
- procexp64.exe
- procexp.exe
- procmon64.exe
- procmon.exe
- python.exe
- taskkill.exe
- visio.exe
- winword.exe
- x32dbg.exe
- X64dbg.exe
Maze also gets information about the antivirus products installed using WMI.
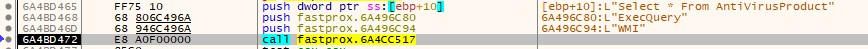
If antivirus software is found, it does not run the payload.
Operation modes
The Maze ransomware can be launched with additional parameters:
- --logging enables the console output to log the ransomware’s activity
- --nomutex allows it to run many copies of Maze ransomware
- --noshares disables encryption for network shares
- --path indicates a directory that will be encrypted
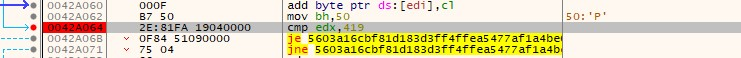
Maze ransomware does not encrypt files on systems with Russian localization. It checks for the ‘419’ value when it retrieves system language from the registry using GetUserDefaultUILanguage.
The ransomware also creates Mutex with a unique ID created for the current user to check if a second instance of the Maze ransomware is running.
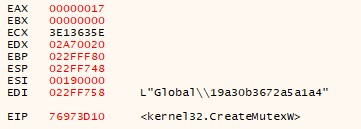
Network connections
Once executed, Maze sends a check-in request to the C&C servers. The list of hardcoded strings that Maze uses to construct network requests is below.
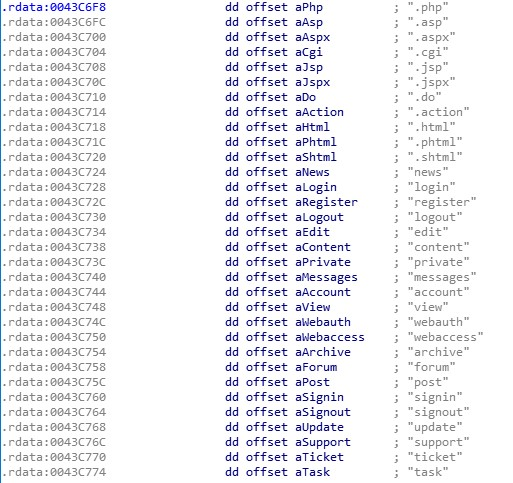
For example: hxxp://91.218.114.4/withdrawal/rrvv.html?q=4s5835 hxxp://91.218.114.4/account/messages/ajaobn.do?t=33mp0 hxxp://91.218.114.11/qoblhdilts.php?xsl=6ohl&gcg=uj8h4g0kp&acg=6d3712ts&fpq=n1w
The IP addresses are located in Moscow, Russian Federation. The subnet 91.218.114.0 is often used by the Maze cartel.
Data stealing
Maze ransomware – similar to the recent ransomware attacks from WastedLocker, Netwalker, and Revil – both encrypts and steals data. It uses the 7zip utility to pack collected data and exfiltrate archives to the attacker’s FTP server using a WinSCP client. In some incidents, it was reported that the exfiltrated data was also Base64 encoded.
Backup deletion
Maze deletes Windows file backups using the following obfuscated command line: "C:\iwq\kuhk\..\..\Windows\f\rtr\..\..\system32\gtnd\q\..\..\wbem\qnyy\k\dejg\..\..\..\wmic.exe" shadowcopy delete
Encryption
The encryption scheme has three layers that use file, session, and master keys. 1. File encryption with ChaCha symmetric crypto algorithm. 2. File keys and IV are encrypted with the Session RSA public key and added to the encrypted files. 3. Encryption of the Session RSA private key with the Master RSA public key. The encrypted Session RSA private key is then stored in the ransom note.
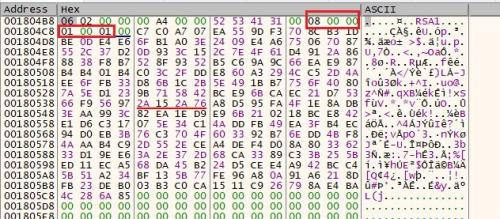
Maze imports the Master RSA-2048 public key hardcoded in the binary.
Maze adds random extensions to the encrypted files.
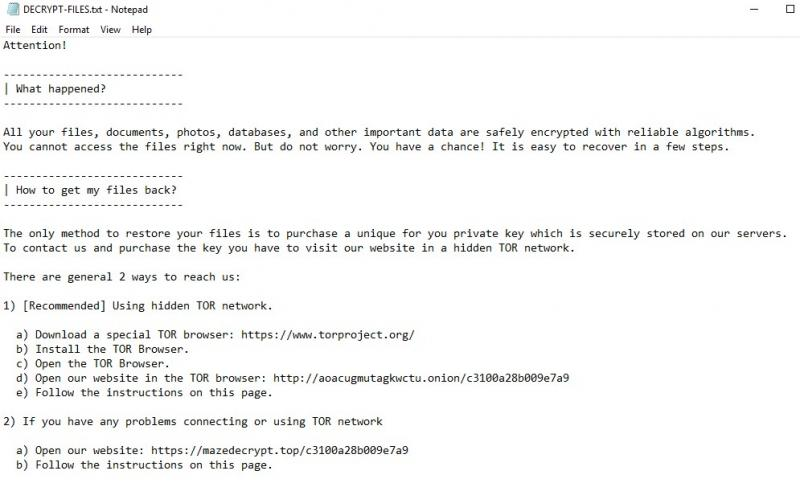
Ransom note
After encryption, the ransomware leaves a ransom note including a unique Maze key created per user.

The successful ransomware’s actions end by setting up a wallpaper with the demand for a ransom.
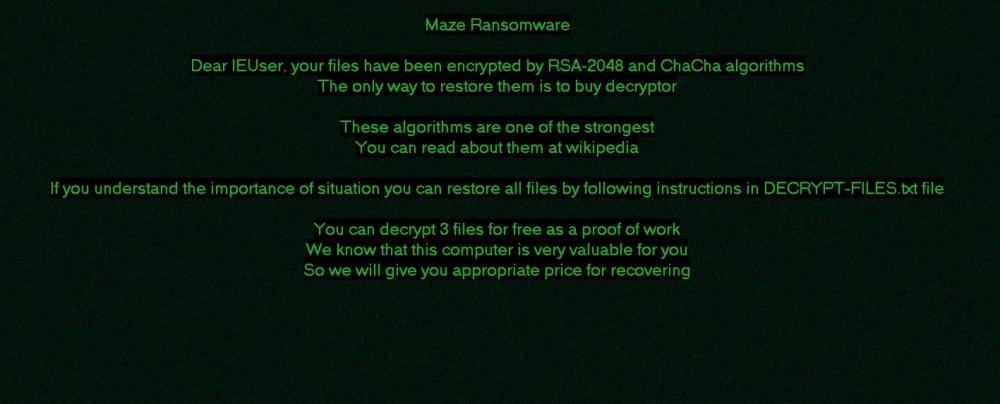
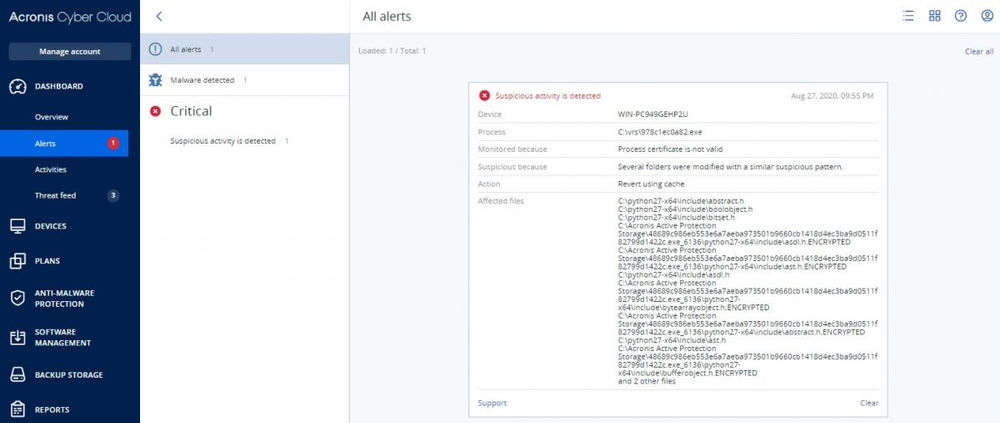
Detection by Acronis Cyber Protect Cloud
Acronis Cyber Protect Cloud has successfully stopped this version of Maze and restored the encrypted files with Acronis Active Protection.
IoCs
SHA256: 1AD0C1D95C38E7C3DE26D8A89CCFA38ED1DBEEC2B93567DFDE593BDA9EE616D2 91.218.114.4 91.218.114.11 hxxp://91.218.114.4/withdrawal/rrvv.html?q=4s5835 hxxp://91.218.114.4/account/messages/ajaobn.do?t=33mp0 hxxp://91.218.114.11/qoblhdilts.php?xsl=6ohl&gcg=uj8h4g0kp&acg=6d3712ts&fpq=n1w
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



