At the start of the “Borrow or Rob” episode from the popular show “Blindspot” screened by NBC, a group of students break into a university server to change their grades. They do it by hacking the backup, and then destroying the primary server:
— “Are you seeing this? There is a boot logger. They’re gonna know we were here.” — “That’s why I am changing the grades on the backup server.” — “And that helps us how?” —“Once I zero out the local drives, they’ll have no choice but to restore them from the backups. Yada, yada, yada, new grades in place. No sign we were here. You’re welcome”
In fact, as many companies manage costs by tiering their security measures, backups often end up being less protected than the primary infrastructure. This makes backups a potential backdoor for hackers.
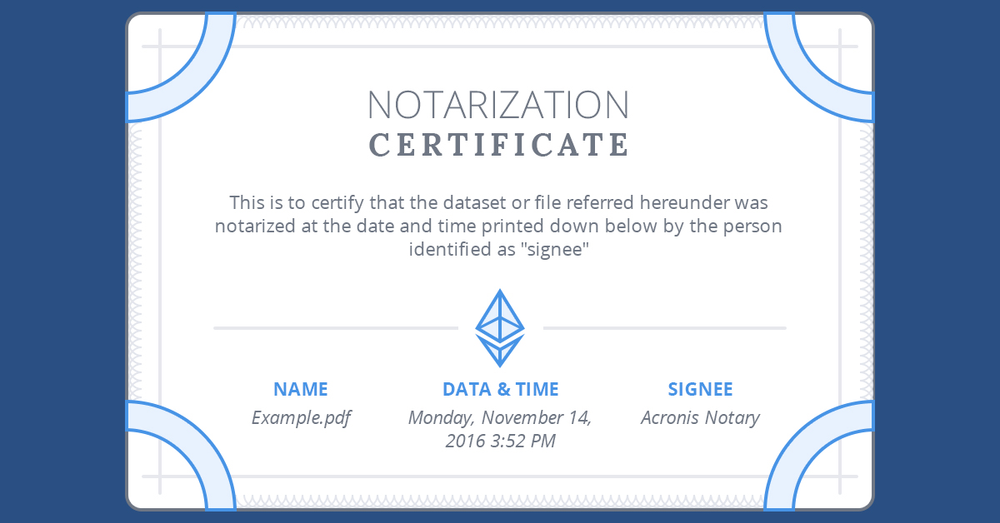
Fortunately, Acronis has the answer – Acronis Notary™, which creates digital certificates, based on checksums of your files, and then stores these certificates in the blockchain database, Ethereum, to ensure they can never be modified.
This means that you can certify what you have backed up, and verify if you are restoring the same file. Here’s how it works:
1. Notarize Your Backups
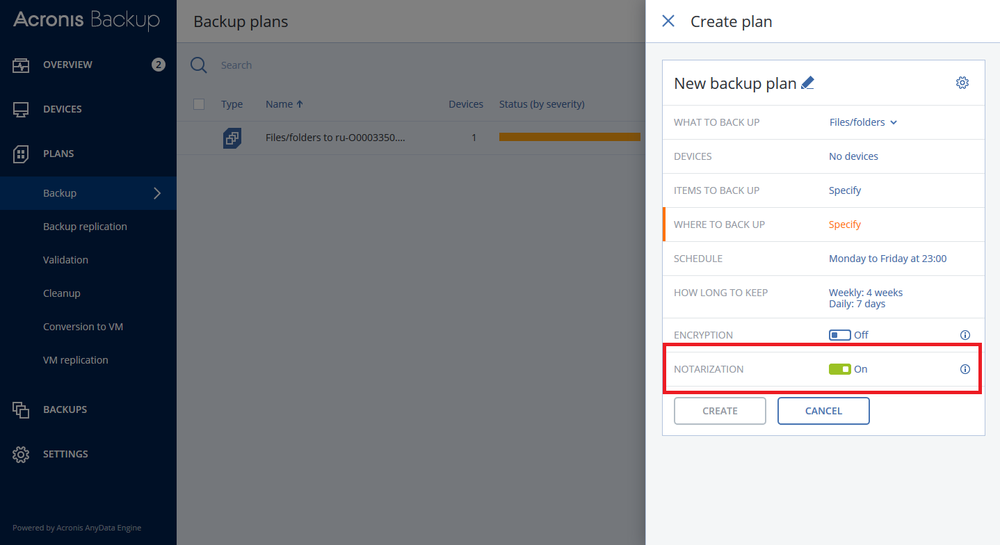
During a backup, the agent calculates the hash codes of the backed-up files, builds a hash tree (based on the folder structure), saves the tree in the backup, and then sends the hash tree root to the Ethereum blockchain database to ensure that these values do not change.
2. Verify Your Files
Simply browse your backup, locate a file you would like to check and click verify on the right.
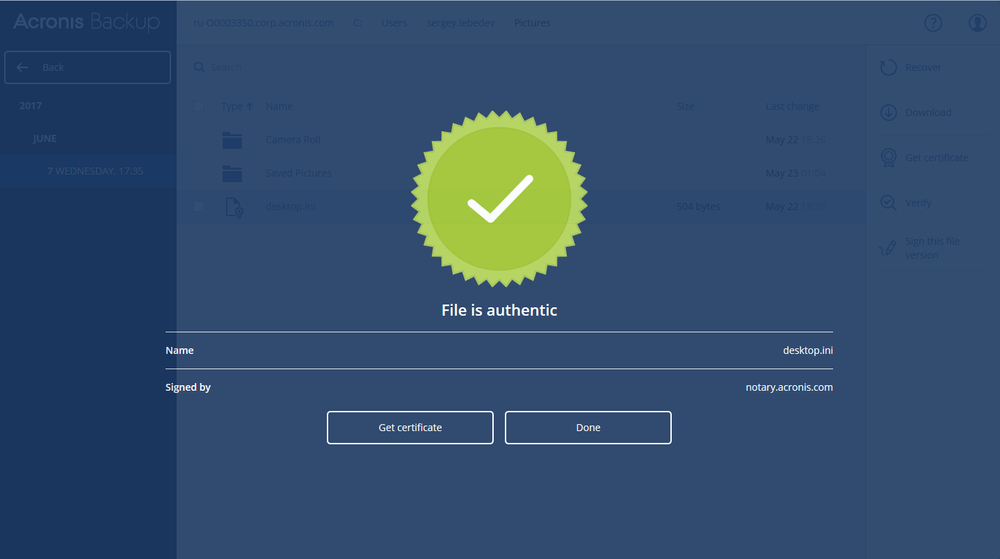
If the file is authentic and unchanged since the backup, you will see this:
You can even get a certificate, that you can print out or send, that proves that what you recover is what you have backed up:
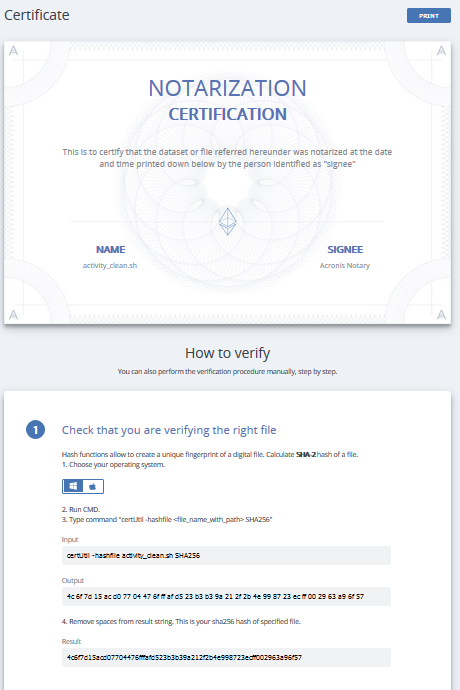
That’s it! This is how you can prove that there were no malicious modifications of your backed up data while it was stored. No more backdoors, no more phony grades for student-hackers.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



