Stop data leaks at the source with complete endpoint data loss prevention (DLP)
- Minimize insider threatsPrevent data leakage due to employee negligence or malicious insiders by blocking any unauthorized attempt to access or transfer sensitive data.
- Gain visibility into data protectionReduce the complexity of data protection and cut reporting times with a single DLP solution for thorough visibility over data flows and user behavior.
- Enforce process complianceReduce information security risks and comply with IT security standards and regulations by enforcing data use and handling policies that users can’t avoid following.
- Supported solutionsMicrosoft RDS, Citrix XenDesktop, Citrix XenApp, VMware Horizon View, VMware Workstation, VMware Workstation Player, Oracle VM VirtualBox, Windows Virtual PC
- Supported controlsContext-aware and content-aware controls, logging, data shadowing and alerting for thorough DLP security over virtualized sessions
- No leakage of corporate dataIT retains complete control over virtual corporate environments on employees’ personal devices
- Private data independencyEmployees maintain full control over the device platform, personal applications, and their private data
Comprehensive data loss prevention capabilities
- Unique
Centralized management and deployment
Ease the resource-consuming processes of deploying and managing an enterprise DLP solution. Acronis DeviceLock DLP offers a set of central management consoles based on an organization’s IT environment, along with the ability to manage and deploy natively through Group Policy. Log collection
Automatically collect audit and shadow logs and deliver them to the secure central repository to ease security investigations and auditing, thanks to Acronis DeviceLock DLP agents. Traffic shaping and data compression for log delivery and load-balancing help reduce network impact.Alerting
Shorten reaction times with real-time SMTP, SNMP, and SYSLOG alerts based on unauthorized actions delivered directly to SIEM systems and administrators.Tamper protection
Prevent tampering with DLP policy settings locally on protected endpoints, even by local sysadmins. When enabled, only designated Acronis DeviceLock DLP administrators using the central management console can uninstall, upgrade the agent, or modify DLP security policies.Allowlisting
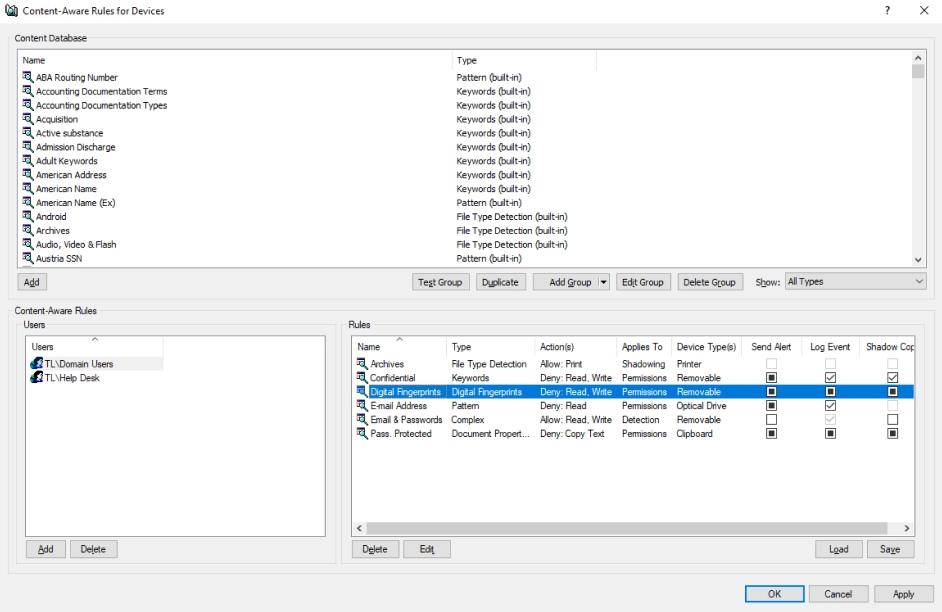
Authorize the use of specific USB devices or provide a temporary access code for offline work purposes. Allowlist media storage devices and users that can access them. Specify allowlist-oriented controls over network communications based on protocol and network application properties.Reporting
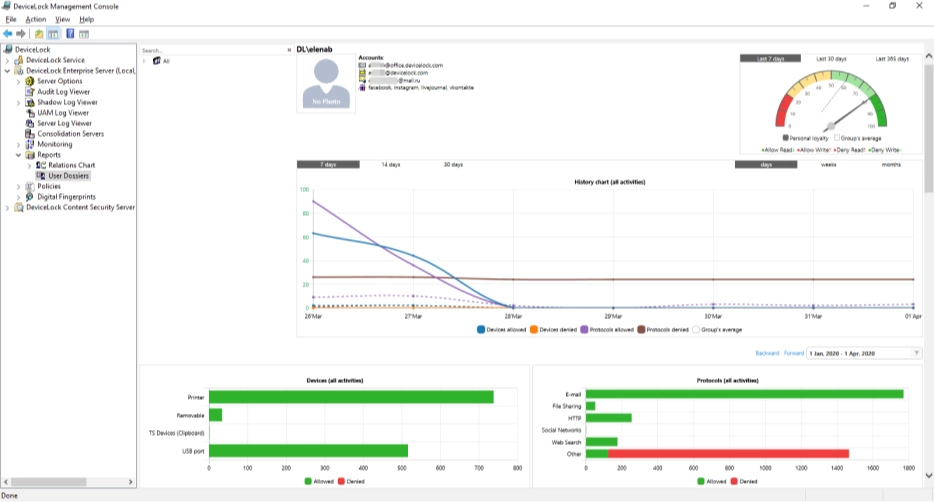
Gain visibility over data flows, data protection, and user activities related to them with powerful built-in compliance-related reports based on audit and shadow logs, permissions and settings, connected plug-and-play devices, and user activities.
What our customers say about Acronis DeviceLock DLP
Acronis DeviceLock DLP
72% of employees share sensitive information. Prevent any data leaks headed your way.
Acronis DeviceLock DLP
Capture new market opportunities in the data loss prevention market with a trusted partner.
Looking for help?
Frequently asked questions
Can Acronis DeviceLock DLP function without internet connection?
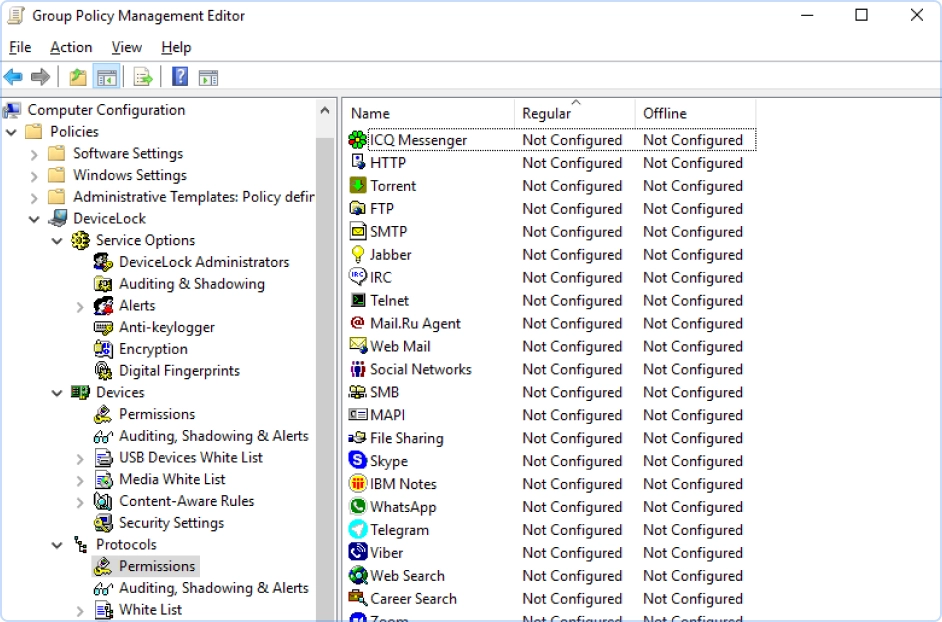
There are two different sets of DLP policies, Regular and Offline, which are automatically applied to a controlled endpoint by Acronis DeviceLock DLP agents depending on its network status. The Offline policy can be triggered by the laptop using either cached or confirmed Windows credential authentication, whether it can connect to any of its known Acronis DeviceLock Enterprise Servers, or if in a wired vs. unwired state.
Is Acronis DeviceLock DLP capable of “passive mode” functioning, i.e. not restricting data transfer, but logging and shadow copying?
Yes, Acronis DeviceLock DLP is capable of functioning in any administrator set mode. We also call this “observation mode”.
In cases where access to ports, devices, or network protocols is not blocked or content-filtered by policy, logging and data shadowing policy can be actively logging and keeping records in audit and shadow logs in “passive mode”.
If there is a restrictive access policy active, Acronis’ DLP solution blocks the transfer and prevents data leakage on a controlled endpoint in real time.
Is there an option to configure various access control policies for laptops in- and out of the corporate network?
Yes, there is. Acronis DeviceLock DLP supports various on- and off-corporate-line security policies. This way you can have one policy when the laptop is behind the firewall or DMZ and a totally different policy when the laptop is out in the wild, strengthening DLP security.
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.