
Do you believe it is not possible to wake up one morning and discover your bank account is empty or your credit cards maxed out? Rethink your thoughts, as the risk of becoming the next victim of identity theft is real, and hundreds, if not thousands, of people face this reality every day, often discovering it too late.
Identity theft is like a digital shadow that can literally steal and ruin your life. It occurs when cybercriminals hijack your personal information, such as your name, Social Security number, credit card details, or even medical records—with the main purpose of gaining financial benefits.
These hackers can open new accounts using your sensitive information, make unauthorized purchases, file fraudulent tax returns, or even engage in loan fraud by taking loans for thousands of dollars in your name. The consequences? Financial ruin, emotional distress, and a credit repair process that can take years!
Over the past decade, identity theft attacks have tripled, fueled by the rise of data breaches and phishing scams. What is even more concerning is the fact that the fallout is not just financial; it is personal. Victims of such attacks often feel violated, struggling to reclaim their sense of security, leaving them with emotional damage for life.
What is the good news? Well, we are here to help, to educate you on how to fight back. By understanding how identity theft works and leveraging identity theft protection services, you can position yourself one step ahead of the cybercriminals and their mean attacks.
In this article, we will explore:
- The evolving landscape of digital identity security
- Why protecting your personal data is more critical than ever
- How Advanced Identity Protector (AIP) works to keep you safe
- Key features to look for in the best identity protection tools
- Practical steps to secure your digital identity in 2025
Understanding digital identity and online threats
Your digital identity encompasses far more than just your passwords and usernames—it is your entire online footprint, including sensitive data that forms a comprehensive digital representation of who you are.
If years ago we were worried about losing our ID documents or credit cards, now the situation is entirely different. Today, we all have emails and social media accounts storing too much personal information about who we are, what our interests are, where we live, what we love, and much more. It’s almost as if our lives are stored in the cloud.
Add to this the fact that online shopping has become an integral part of our daily routine, where we provide financial information and credit card details to complete every single order. Together, these elements create a perfect storm—a recipe for potential disaster if we don’t take the necessary steps to secure our digital lives.
What is even more concerning is the fact that cybercriminals employ a variety of sophisticated methods to target our personal information, through exploiting the intersection of human psychology and technical weaknesses.
Being aware of and understanding these tactics is the first step to preventing online identity theft effectively. Nowadays, hackers leverage AI-generated content and approaches to create convincing impersonations of legitimate services, while sophisticated malware strains silently harvest our credentials and financial data.
Furthermore, data breaches have become particularly harmful and dangerous, as threat actors exploit software vulnerabilities to extract massive amounts of personal information, which, of course, they sell on the dark web for personal financial benefits.
Now, ask yourself, are you prepared well enough to prevent such catastrophic scenarios? Identity theft victims often face catastrophic consequences that extend beyond immediate financial losses. They are threatened to experience significant credit damage that can take years to repair, struggle with compromised medical records that affect healthcare access, and face complex legal challenges requiring extensive documentation to resolve.
The question is not whether you will face cyber threats—it is how well prepared you will be when they arrive. Today, proactive security measures and robust identity protection are not optional anymore—they are essential for survival. Are you ready to take control of your digital security?
Why you need advanced identity protector?
Identity Protection’s main goal is to protect your personal information and prevent identity theft. At its core, this technology continuously monitors your sensitive personal data, including names, addresses, social security numbers, and financial details, to detect and prevent identity theft attempts.
Being equipped with such protection nowadays is of utmost importance because, according to the FTC Data Book 2023, there were 1.4 million identity theft cases reported this year alone, and these numbers continue to skyrocket. Remember that it is your personal responsibility to secure your digital identity in order to avoid falling victim to the cybercriminals.
Acronis True Image implements this critical protection through an advanced, multi-layered security system. As the FBI reported $10.3 billion lost to digital crime in 2022, Acronis’s solution can adequately respond to the evolving threat landscape, where hackers lately leverage AI for improving their phishing attacks and identity theft schemes and make them even more convincing and trustworthy with the main purpose of easily tricking their victims to provide their sensitive information.
Acronis True Image is able to protect your identity effectively and minimize the chance of becoming cybercriminals’ next victim. The platform’s identity protection service operates through these fundamental mechanisms:
Monitoring and Portal
Acronis True Image safeguards your personal information and prevents identity theft, while the easy-to-use portal warns you of suspicious activity through email or text messages.
Resolution Services
Receiving 24/7 support is as important as the protection itself, and Acronis True Image delivers this essential option, helping you restore your identity or financial losses in case of a data breach or identity theft anytime you need.
Cyber Insurance
With Acronis’s Identity Protection, you have up to $1 million in identity fraud insurance.
What sets Acronis True Image apart is its integrated approach to digital security that has been developed and improved on a daily basis. Beyond identity protection, you will be equipped with advanced active ransomware protection that constantly monitors for unauthorized attempts for data modification and intercepts the attack at its early stage before things escalate.
Secure backup capabilities complement this, utilizing strong encryption and secure data centers to create a reliable and efficient protection against various cyber threats.
Acronis True Image has proven its efficiency in delivering outstanding identity theft protection, safeguarding your sensitive information against sophisticated identity theft variants, including:
- Tax identity theft through fraudulent return filings
- Medical identity theft affecting healthcare access
- Employment identity theft impacts background checks and employment verification.
With 47% of Americans having their personal information exposed (CISA, 2022), Acronis True Image delivers essential protection during everyday online activities like e-commerce transactions and travel bookings, ensuring your digital identity remains secure in an increasingly vulnerable online environment.
How does identity protection work?
At its core, these services start collecting your sensitive and private data—things like your Social Security number, details of your credit accounts, bank account information, and other personal identifiers.
After collecting that information, the best identity and credit protection solutions apply real-time monitoring for your credit reports and other financial activities. Through millions of scans of data points across the internet and dark web, these services work 24/7 to detect if and when your sensitive information appears in suspicious places without your knowledge.
For example, if someone tries to open a new credit card using your Social Security number, you will instantly receive app notifications allowing you to verify whether you authorized this activity.
To improve their protection capabilities even more, identity protectors provide regular credit report monitoring from major credit bureaus, with the main purpose of tracking any changes that might indicate fraud activity. These credit protection features work alongside other tools to ensure comprehensive security. If the worst happens and somehow you become a victim of identity theft, the protection service activates its recovery protocols instantly.
These include connecting you with dedicated fraud experts who will help you dispute unauthorized transactions, assisting with creditor notifications, providing identity theft insurance coverage, and guiding you through the entire recovery process.
On top of that, reliable and efficient identity theft protectors offer cybersecurity tools like a secure password manager, a VPN, and encrypted storage for sensitive documents in order to create a secure environment for your digital identity that minimizes the chance of this information being accessed by unauthorized users.
Through this multi-layered approach of monitoring, alerting, and recovery assistance, identity protection services aim to detect and stop identity theft before it causes significant damage to your financial and personal life, which might take you years to recover from.
What features should I look for in the best advanced identity protector?
When choosing the best advanced identity protector, look for the following features:
1. Identity theft monitoring service
Real-time monitoring and active protection is an essential part of effective identity protection because it is literally the first defense line against identity theft. Advanced solutions combine multiple monitoring layers to detect unauthorized activity and alert you to potential threats before they escalate into serious security incidents.
2. Credit monitoring
Credit monitoring serves as a vital protection mechanism for your financial well-being, delivering comprehensive credit monitoring across all major credit bureaus. This critical feature continuously analyzes your credit card accounts, alerts you to suspicious credit inquiries, and helps maintain your credit score integrity through instant notifications of any changes in your credit reports.
While consumers now have permanent access to free weekly credit reports from major credit agencies (Equifax, Experian, and TransUnion) through AnnualCreditReport.com, Acronis True Image provides the best credit protection through comprehensive automated monitoring and instant alerts that go beyond basic report access. This proactive approach ensures you don't have to manually check your reports to catch potential identity theft attempts.
3. Social security number monitoring
Social Security number monitoring provides continuous surveillance of your most sensitive identifier, tracking its usage across financial institutions, credit applications, and public records. This sophisticated monitoring helps prevent unauthorized applications and fraudulent tax returns while offering robust fraud protection against financial identity theft attempts.
4. Public record monitoring
Public record monitoring employs advanced scanning algorithms to detect any misuse of your personal information across court records, address changes, and other public databases. This approach helps detect potential criminal identity theft and provides early warning of fraudulent activities that could impact your financial security.
5. Real-time alerts for suspicious activities
The best identity protectors deliver instantaneous notifications for:
- Unauthorized access attempts at your bank account
- Investment account monitoring alerts
- Potential exposure to credentials on dark web platforms (dark web monitoring)
- Unusual patterns in credit card fraud attempts
Types of alerts
- Credit inquiries: Immediate notifications of new credit applications or unauthorized credit checks
- Account changes: Real-time alerts for modifications to existing accounts, including address updates
- Public records: Instant notifications of changes in court records or address registrations
- Social Security number: Alerts for any activity involving your SSN, including new account applications
6. Customizable Alert Settings
Advanced identity protector solutions offer sophisticated alert customization options, allowing you to:
- Prioritize notifications based on threat severity.
- Adjust alert thresholds for different types of activities.
- Configure preferred notification methods
- Set specific monitoring parameters for different accounts.
This comprehensive protection framework, combined with generous insurance coverage, ensures robust defense against evolving identity theft threats that stalk us around the corner to strike at the most inappropriate moment.
Why you need an identity protection and how Acronis True Image saves you money
Identity theft incidents continue to surge, with 842,000 cases reported in the first three quarters of 2024 alone, putting them on track to exceed the 1,037,000 cases reported in 2023, according to the Federal Trade Commission (FTC). The financial losses are equally staggering—Javelin Strategy & Research reports that identity theft resulted in $23 billion losses in 2023, highlighting the devastating economic impact of this escalating cyber threat.
This statistic indicates that credit card fraud continues to be the primary concern, with 327,000 cases reported in the first three quarters of 2024, a 3% increase from the same period in 2023. New account fraud, where hackers use stolen personal information to open credit cards in the victims’ names, accounts for 90% of all credit card fraud.
Meanwhile, synthetic account fraud, which is a growing threat in the last years involving fabricated identities, has surged by 154% from late 2023 to early 2024, according to TransUnion.
The cost of recovering from identity theft can be measured in exact numbers, but the emotional stress, damaged credit scores, and hours spent resolving fraudulent activities cannot.
Invest in identity theft protection services like Acronis True Image, which offers advanced identity protection capabilities to help you stay in control of your personal data and prevent it from falling into the wrong hands of cybercriminals, to avoid identity theft and other cyberthreats.
This kind of protection helps prevent cybercriminals from exploiting your data for their personal financial benefits by opening new accounts, filing fraudulent tax returns, or committing insurance fraud.
Acronis True Image boasts a groundbreaking monitoring system that protects your personal information and alerts you to any suspicious activity. When combined with identity and credit protection, offering up to $1 million in identity fraud insurance and 24/7 resolution services for identity restoration in case you fall victim to identity theft is what you really need for protecting your sensitive information while ensuring your peace of mind.
Furthermore, Acronis True Image will not only provide you with efficient identity protection but also with advanced cybersecurity features that will safeguard your entire digital life. Its famous ransomware protection constantly monitors your data for unauthorized modification patterns, detects suspicious behavior, and safeguards against even unknown ransomware variants. On top of that, the secure backup capabilities ensure that your data is encrypted and securely stored, protecting it from the mean cybercriminals.
For families, Acronis True Image extends comprehensive device protection to all family members, ensuring a secure digital environment for the household. By integrating essential cybersecurity tools—including identity monitoring, ransomware defense, and secure backups—it delivers family protection through simple yet superior security measures that safeguard your entire family.
Don’t wait until it’s too late. The investment in Acronis True Image's identity theft protection represents not just security but essential financial risk management. This comprehensive solution costs less than 1% of potential identity theft losses while providing robust protection against the countless cyberthreats you may face on a daily basis.
How to set up and use Acronis identity protection software
If you have made the wise decision to equip yourself with Acronis Advanced Identity Protector (Acronis True Image), and you want to make sure that it will be configured properly to achieve the best results, then follow this step-by-step guide:
Step 1. In the left sidebar of Acronis True Image, navigate to "Protection."
Step 2. At the bottom right corner of your screen, click "Manage protection.". Then "Online Dashboard" opens in the browser.
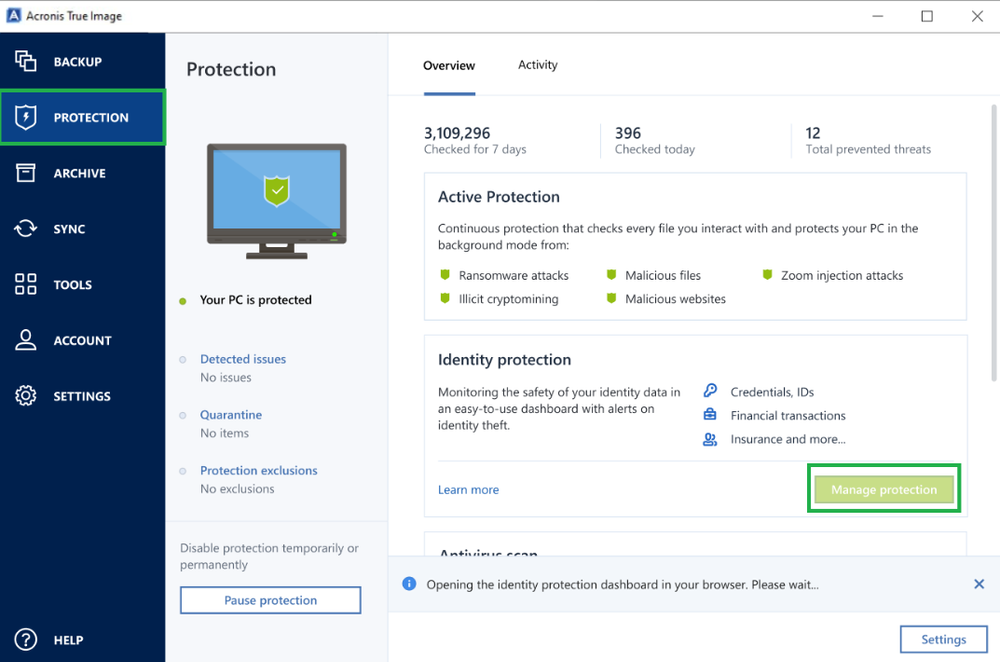
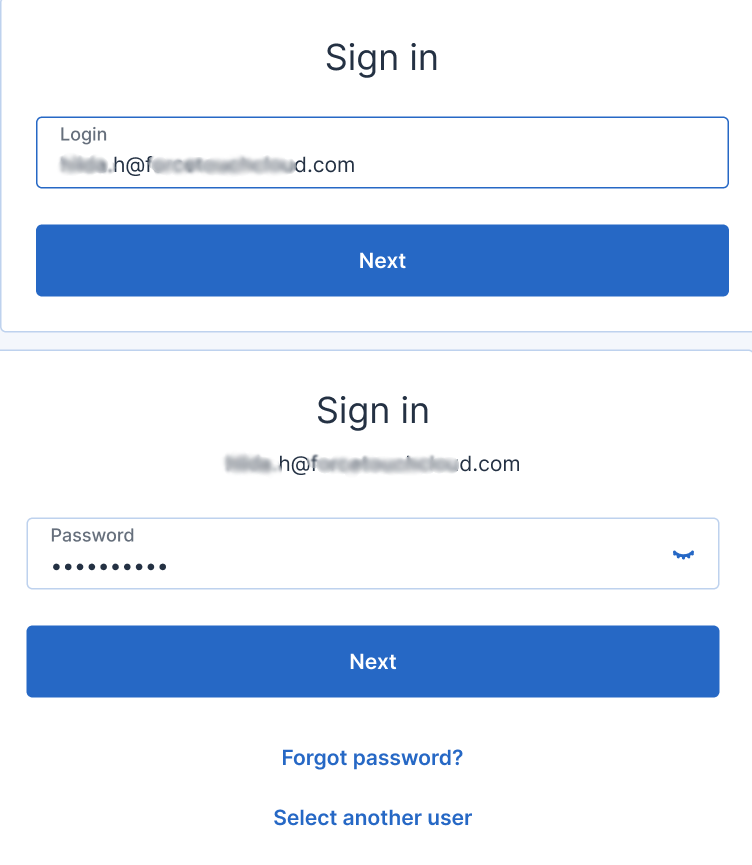
Step 3. Now you will need to sign in to the "Online Dashboard."
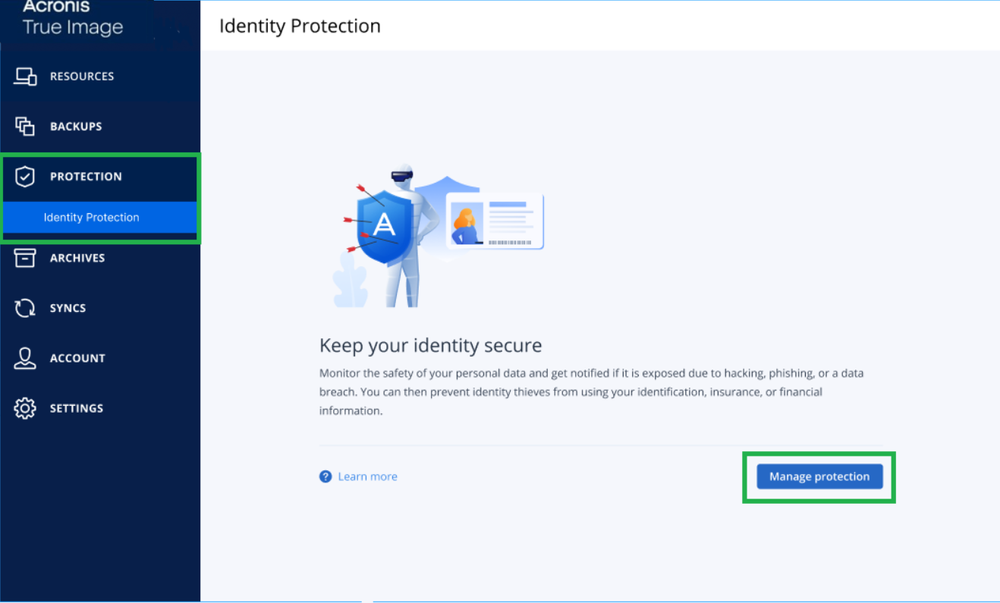
Step 4. Then, navigate to "Identity Protection," and then click on "Manage Protection."
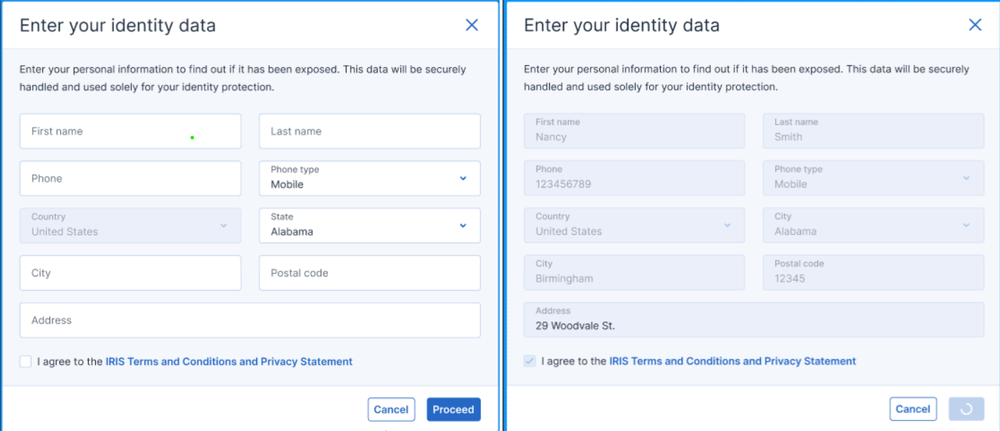
Step 5. Fill in all required fields. Once ready, Acronis True Image initiates automatic security verification checks.
Step 6. Once you provide the necessary information, the "Identity Protection" dashboard will automatically open in your browser.
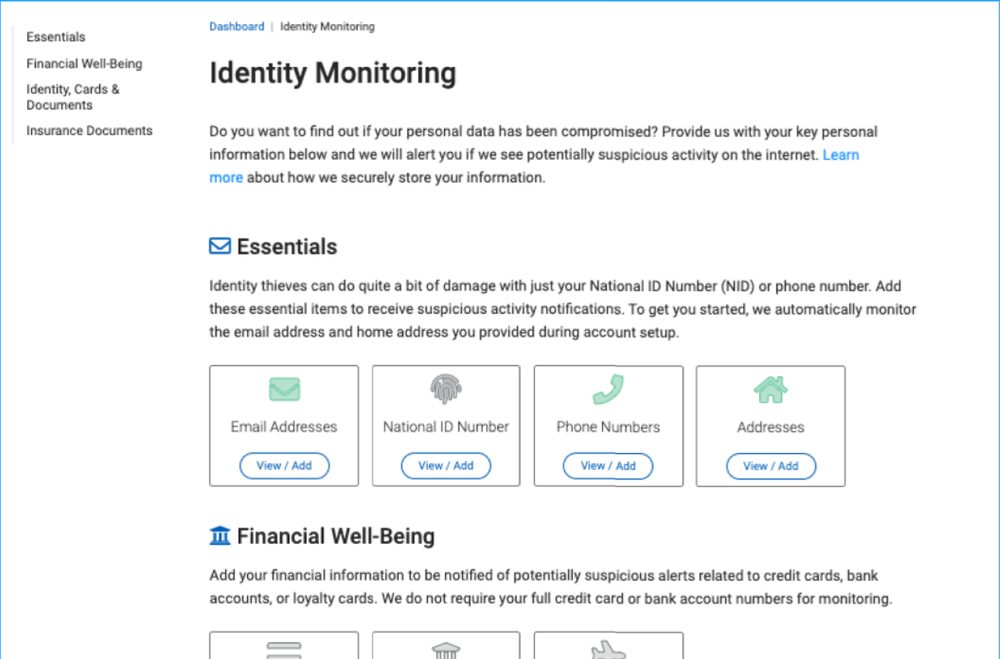
Best Practices for Maximizing Identity Protection
Using an advanced and reliable identity protector is only the first step to minimize, as much as possible, the chance of experiencing the unpleasant feeling of becoming a victim of identity theft. There are many other actions you must take to keep cybercriminals away. We have outlined some of our top tips that will help you with that mission.
Implement proactive identity threat monitoring
One of the most critical steps is establishing regular identity threat scanning—this extends beyond monitoring credit score changes to actively identifying any signs of suspicious activity that could result in stolen funds from your bank accounts.
Implementing automated alerts for high-risk transactions becomes essential, along with careful review of your financial statements, particularly when conducting first-time transactions with new online merchants. This proactive monitoring approach helps prevent unauthorized access and protects against sophisticated theft attempts targeting your financial assets.
Encrypt your personal data
It is your responsibility to keep your sensitive information, including financial documents, encrypted in a secure digital environment. This guarantees that even if cybercriminals somehow breach one layer of your security protection, they won't be able to easily access your files. Encrypting your personal information has proven to be one of the most effective methods to stop hackers.
Enable multi-factor authentication
Two-factor or multi-factor authentication options on websites and apps significantly reduce the risk of unauthorized access. Consider this security parallel: just as a car's immobilizer prevents theft even if someone breaks in, multi-factor authentication blocks unauthorized access even when credentials are compromised. Even if cybercriminals obtain your password, they cannot access your accounts without the secondary authentication factor.
Create strong and unique passwords
Do not be a person who uses weak passwords; create strong, unique passwords for each platform, mixing uppercase, lowercase, numbers, and symbols. Consider each password a unique key to a different part of your digital life—would you use the same key for your house, car, and office? Probably not.
Stay alert to phishing attempts
Vigilance against phishing attempts and suspicious links is critical as cybercriminals become increasingly sophisticated in their approaches. Before clicking any link or downloading attachments, verify the sender's authenticity and look for subtle signs of fraud, such as slight misspellings in email addresses or unusual urgency in requests.
Be careful what you share online
Be careful when sharing content on social media platforms; oversharing is not a good idea; keep things tight.
The role of AI and machine learning in identity protection
Artificial intelligence and machine learning have already become an essential component of cybersecurity, and they will continue to evolve and improve faster than you can imagine in order to help us in the battle against cyber threats. But how do these technologies enhance security, and what makes them so effective? Let’s break it down.
How AI Enhances Security Threat Detection
Nowadays, AI has a massive impact on threat detection by deeply analyzing enormous amounts of data in real-time with the main purpose of identifying cyber threat patterns that humans or traditional cybersecurity systems might miss. For example, AI can flag unusual login attempts, block suspicious transactions, or detect subtle changes in user behavior. Today, AI is capable of detecting a fraudulent credit card application or data-stealing malware before it causes any harm, resulting in devastating consequences for every person.
Imagine what this technology will be capable of soon, undoubtedly, in the near future, we will witness fully autonomous cybersecurity protection capable of thwarting every cyber attack before it even reaches our devices.
Machine Learning Algorithms in Identity Theft Prevention
Machine learning algorithms are the backbone of modern identity protection. These systems continuously learn and improve in their ability to predict and prevent cyber attacks at their early stage. Techniques like anomaly detection, natural language processing, and predictive analytics help identify threats before things escalate and get out of control.
For instance, when a hacker tries to gain access to your online accounts, machine learning can spot this and spring into action immediately. Likewise, AI and ML will take cybersecurity to a whole new level.
Future Advancements in AI-Driven Security Solutions
The future of AI-driven security is incredibly promising, with transformative potential for identity protection. Advances in deep learning and neural networks will enable even faster, more accurate threat detection through sophisticated pattern recognition and behavioral analysis. We are witnessing the emergence of AI-powered tools that automate breach responses with unprecedented speed and precision, dramatically reducing damage scope and recovery time.
Could this technological evolution herald an era where stolen identities and data-stealing malware become rare exceptions rather than persistent threats? The next few years will reveal how these innovations reshape the cybersecurity landscape.
Final Thoughts and Recommendations
Identity theft cases have surged to unprecedented levels, so protecting your digital identity is not an option anymore—it is a necessity. The risk of falling victim to identity theft is real, and the consequences become devastating without proper security measures in place. The truth is that in one day you can lose more than you think, and we are not talking about the financial part; the stress, nightmares, anxiety, and constant regrets are the most severe consequences.
On the other hand, if you want to prepare yourself for the unexpected, then don’t hesitate even for a second and choose Acronis True Image, which stands out as a comprehensive solution that addresses multiple facets of digital security. Acronis True Image's remarkable combination of identity protection, real-time monitoring, AI-powered threat detection, and robust backup capabilities equips you with all the necessary tools to ensure financial and mental stability no matter what happens.
One strategic and wise decision can prevent the emotional trauma, financial devastation, and time-consuming recovery process of identity theft. Do not wait for a disaster to happen and then regret why you have not taken actions to secure your digital identity. Take control of your digital security today; invest in your bright future by equipping yourself with Acronis True Image—because when it comes to protecting your identity, prevention is not just better than cure; it is the only reliable strategy. Your digital identity is priceless; protect it like one.
Never worry about identity theft again, with Acronis!
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.




