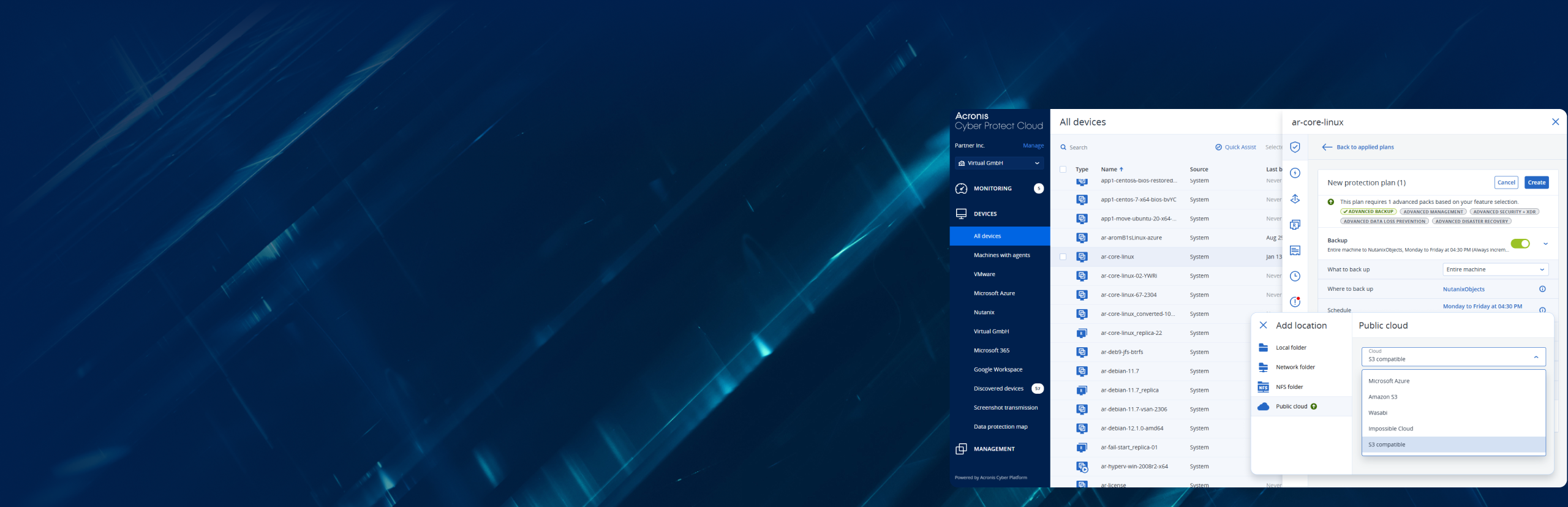
- Increase automation and productivityDeliver near-zero RPOs and downtime with cloud backup enhancements – like continuous data protection. Save time while preventing client data loss.
- The most secure managed cloud backupAcronis delivers a unique approach by combining cloud backup with cyber protection features, such as anti-malware and antivirus – helping you keep clients’ data secure.
- Protect more workload typesProtect more than 20 workload types from a single console, including Microsoft Exchange, Microsoft SQL Server, MariaDB, MySQL, Oracle DBMS Real Application clusters, and SAP HANA.
Benefit from backup capabilities enhanced with cyber protection – with more than 20 workload types, you can protect your clients’ data confidently. Discover what backup and data protection capabilities you gain with Acronis Cyber Protect Cloud. Harness the power of one solution, one agent, and one console to deliver the comprehensive cyber protection your clients seek.
| File-level, disk-level, image and application backups | | |
| Backup popular workloads like Mac, Windows, Linux, Microsoft 365, Google Workspace, Hyper-V, VMware, and much more | | |
| Hybrid storage options – Acronis-hosted storage, public clouds such as Microsoft Azure, or MSP local storage | | |
| Flexible recovery options from full systems to granular files | | |
| Cloud-Physical-Virtual migrations | | |
| Archive encryption | | |
| Incremental and differential backups | | |
| Group management for Microsoft 365 and Google Workspace: Create static or dynamic groups based on your Azure AD data and simplify protection management for multiple seats by eliminating the need to configure protection for each individual seat | | |
| Adjustable backup frequency for Microsoft 365 and Google Workspace: Reduce RPO and improve business continuity by backing up your seats data up to 6 times per day | | |
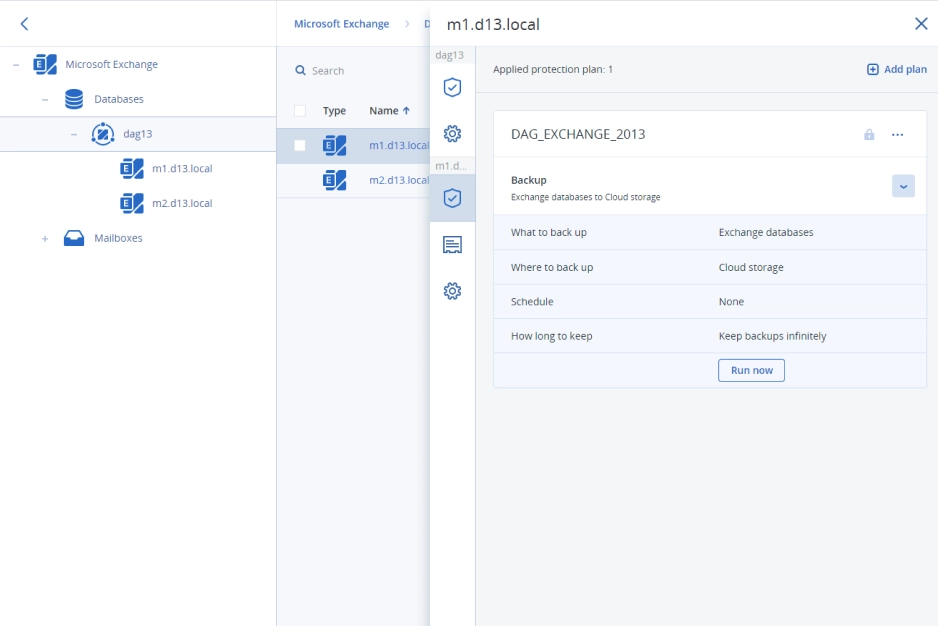
| Extended backup support: Covers Microsoft SQL clusters, Microsoft Exchange clusters, MariaDB, MySQL, Oracle DB, and SAP HANA | | |
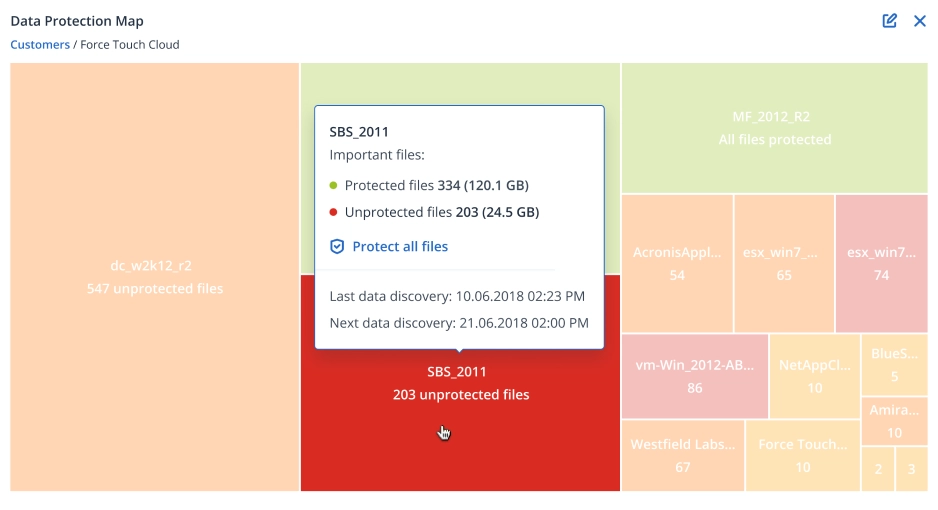
| Data protection map and compliance reporting: Scan clients’ environments to ensure their workloads, files, applications, and users are protected | | |
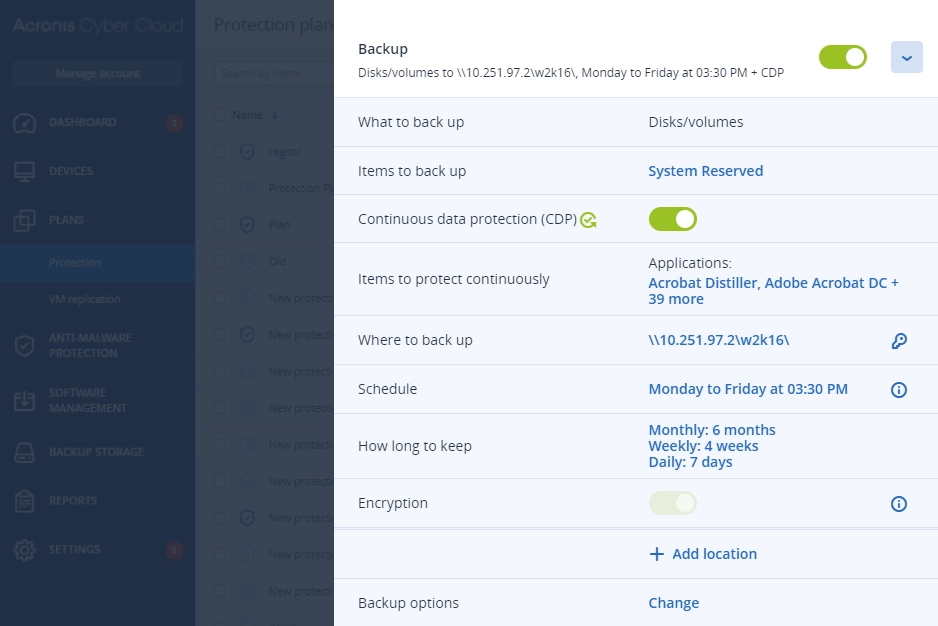
| Continuous data protection (CDP): Acronis’ agent monitors and backs up changes in real time with near-zero RPOs, ensuring no data is lost | | |
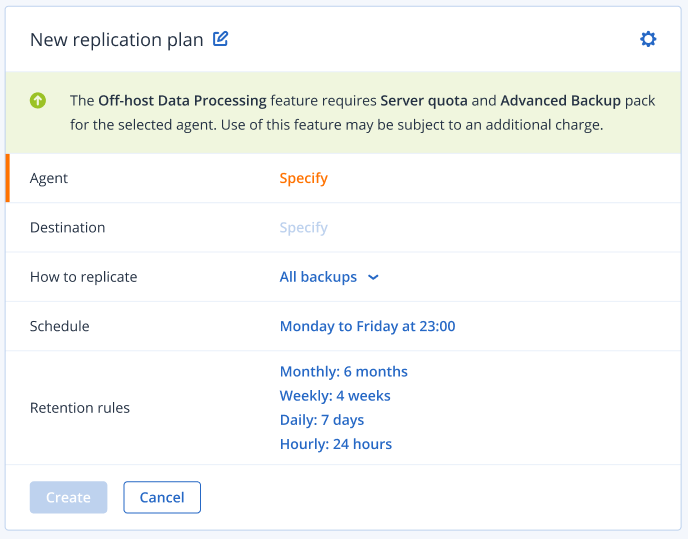
| Off-host data processing: Reduce the CPU/RAM consumption and achieve near-zero RTO of a protected workload | | |
| Direct backup to Azure Storage, Amazon S3 or any (private and public) S3-compatible storage without any additional gateways | | |
| Blockchain-based notarization of backups: immutable, verifiable proof of data integrity protecting your business from tampering, ensuring compliance, and enhancing trust | | |
Safeguard client data, even between scheduled backups. Extend backup capabilities to SAP HANA, Oracle DB, MariaDB, MySQL, and application clusters. You’ll also have greater visibility into the protection status of all data across your clients’ infrastructure.
Acronis Geo-redundant Storage is designed to enhance your backup strategies by adding an extra layer of protection. Back up your data to an Acronis data center and have it automatically replicated to another remote Acronis location in the background.
- Enhanced Data ProtectionIf one data center faces an outage, your data remains accessible from another location, guaranteeing uninterrupted access.
- Compliance and SecurityGeo-redundant storage helps meet regulatory requirements by ensuring that data is securely stored across diverse geographic locations.
- Cost-EfficiencyLeveraging geo-redundant storage reduces the risk and associated costs of data loss, ensuring that your valuable data is always safe and accessible.
Upcoming events
Powered by industry-recognized, award-winning endpoint protection














Acronis Cyber Protect Cloud
Modernize your clients' security and backup with integrated cyber protection
Acronis Professional Services
If your organization has a complex IT infrastructure or limited IT resources, Acronis Professional Services can assist you with the design, integration, implementation and on-going operation of your Acronis solution.
Consulting services
Leverage Acronis’ experience and shorten the time it takes to gain value from your Acronis investment.- Exclusive
Deployment services
With Acronis Deployment Services, you can be the first to market with data protection, infrastructure migration, and disaster recovery services. Audit services
Decrease maintenance costs and enjoy peace of mind knowing your customers’ data is protected in accordance with industry and Acronis best practices.Educational services
Enable your personnel to drive data protection, migration, and disaster recovery services enablement, effectively support your customers.
- UniqueData protection map and compliance reportingGuarantee that critical data is protected for compliance reporting, with the data protection map. Use the automatic data classification to track the protection status of important files, folders, and workstations. If they are not protected, an alert is created so you can protect your clients’ critical data.
- UniqueApplication cluster backup and restoreEase the IT administrative burden with built-in capabilities to easily backup and restore Microsoft Exchange, Microsoft SQL Server, and Oracle DBMS Real Application clusters. This easy to preform backup for service providers helps you quickly and easily protect multiple workload with one solution.
- SAP HANA backupStrengthen SAP HANA database protection with consistent, script-based, disk-level backups that simplify management and do not require any SAP HANA expertise. If a recovery is needed, you can perform image-based backup for your clients’ SAP HANA database and all the data associated with it, including application configurations.
Expand your services with advanced protection
Add other powerful components to strengthen your services even further with advanced protection and unique cyber protection capabilities. Control your costs by paying only for the functionalities your clients need.
- Security + XDRInstead of counting on a costly and complex stack of point solutions, Acronis XDR introduces natively integrated, highly efficient protection built for MSPs:
- Natively integrated cybersecurity, data protection and endpoint management
- Highly efficient security designed to protect the most vulnerable attack surfaces with AI-guided incident analysis and single-click response
- Built for MSPs, including a single agent and console for all services
- Security + EDRInstead of counting on a costly & complex stack of point solutions, Acronis enables MSPs via integration of EDR, endpoint management, and backup & recovery to:
- Easily launch a complete security solution, including rapid recovery
- Protect against modern threats and readily comply with cyber insurance requirements
- Maximize efficiency through a single security platform
- Acronis RMMAchieve peak MSP performance with a natively integrated, secure, AI-powered RMM. Enhance client satisfaction by delivering superior IT administration and monitoring services while improving security posture for both endpoints and Microsoft 365. Boost technician performance with seamless automation of IT management.
- Automated patch management
- System and hardware monitoring
- AI-assisted scripting and more
- Acronis PSASimplify success with an easy-to-deploy, adopt and use PSA tailored for modern recurring and cloud MSP business models. With Acronis PSA, you take the shortest path to increased profits and streamlined business operations.
- Service desk
- Billing and invoicing
- KPI reports and more
- Advanced BackupDefend clients’ data, even between scheduled backups. Extend backup capabilities to SAP HANA, Oracle DB, MariaDB, MySQL, and application clusters. You can also gain visibility into data-protection statuses across your clients’ infrastructure.
- Continuous data protection
- Data protection map
- Off-host data processing
- Disaster RecoveryGet clients back to business in mere minutes when disaster strikes by spinning up their systems in the Acronis Cloud and restoring them anywhere, ensuring immediate data availability. Make disaster recovery painless and increase efficiency with orchestration, runbooks, and automatic failover.
- Disaster recovery orchestration
- Production failover
- Site-to-site VPN
- Email SecurityBlock any email threat, including spam, phishing, business email compromise (BEC), account takeover (ATO), advanced persistent threats (APTs), and zero days in seconds before it reaches end users. Leverage Perception Point’s next-generation technology for lightning-fast detection and easy deployment, configuration, and management.
- Anti-phishing and anti-spoofing engines
- Anti-evasion and account takeover protection
- Next-generation dynamic detection against zero-days
- Data Loss Prevention (DLP)Prevent leakage of sensitive data from endpoints via more than 70 local and network channels and strengthen compliance with minimal effort and speed to value.
- Content-aware data loss prevention
- Automatic client-specific DLP policy creation and extension
- Pre-build data classifiers for common regulatory frameworks
- File Sync and ShareGet a full control over data location, management and privacy with a file sync and share service, including a transaction ledger to enable notarization and eSignature capabilities, across all platforms.
- File notarization
- Embedded eSignatures
- Independent file verification
Learn More, Earn More with Acronis Academy
Whether you and your team are seeking professional certifications or starting an MSP business, we're here to support you at every stage.

Start learning for Free
New! MSP Academy offers budding and seasoned MSP professionals vendor-neutral training covering the A-Z of managing a successful MSP business.
Train on-demand
Access our most popular sales and technical training courses designed for existing MSPs looking to enhance their cybersecurity skills and knowledge.
Login to Partner Portal
Available exclusively to Acronis Partners. Access our complete Acronis Academy training catalogue and earn your required certifications.
Looking for help?
Frequently Asked Questions
I signed up for a trial. Where can I download the backup agents?
You first need to create a customer and an account for them. Once that is done, you can either log in as that customer or, in the Account management console, select the customer to manage their backups. This will bring you to the Backup management console where you can download the backup agent.
How much system resource usage will it take to back up?
1. Resource usage is relative to the system specifications and a number of other factors, such as disk speed, disk size, available bandwidth, etc. By default, the Acronis backup process runs on low priority, with the operating system dynamically throttling its resources.
2. On modern servers and workstations, the CPU usage is typically around 3-4% and RAM consumption will be up to 500 MB with CPU spikes during the snapshot phase.
Can you integrate with my storage solution?
Acronis provides a hardware-independent software solution that can work with almost any hardware on industry-standard protocols like SMB and NFS. Acronis can also support any block-based storage, as long as it's supported by the operating system.
How can I set up a backup to a network drive?
In the backups section of the backup portal:
- Select Add Location
- Select a Network folder and enter the network path
We also have online documentation
How frequently can I back up (RPO)?
This will depend on the size and performance of the hard disk, the amount of data changed, and the available bandwidth. Testing needs to be done, but the minimum threshold is 10 minutes.
What are the best practices to back up Hyper-V?
We recommended you perform agentless backup for Hyper-V guest VMs, unless the VM needs to have ransomware protection and application-aware backups. Then, installing a Windows application agent is required.
Does Acronis support deduplication?
1. Acronis backup agents support deduplication, in archives, for a single machine. Any new duplicated files will be skipped and not backed up.
2. Acronis Cyber Protect Cloud does not use a centralized deduplication server as the client's data can be encrypted and containerized for security purposes.
What is the compression rate?
Compression rates vary depending on the type of data but generally, you can expect around 30-40% compression unless the data is exclusively media files.
Does Acronis support encryption?
Yes, Acronis Cyber Protect Cloud and its services use encryption on all levels.
How does ransomware protection work?
Acronis Active Protection is an advanced anti-ransomware technology. Completely compatible with the most common anti-malware solutions, our artificial-intelligence-based technology actively protects all of the data on your systems, including documents, media files, programs, Acronis Cyber Protect Cloud files, and more. It can detect and deflect attacks, and restore impacted data. For more information, review this guide in the Knowledge Base.
How granular is Exchange/Microsoft 365 recovery?
Granular recovery can restore individual items from the mailbox: a single email, contact, or calendar item.
How do I do a bare metal restore?
Bare metal restores can be done by booting the target machine using bootable media, point to the backup repository for the image file. (Refer to: https://www.acronis.com/en-us/support/documentation/BackupService/index.html#42056.html).
How can I restore a VM to Azure/Google/Amazon?
The destination VM needs to have an OS pre-installed with the Acronis agent. The restoration will then be done using either P2V or V2V. It's not possible to use bootable media in Azure/Google/Amazon.
Can I restore from a smaller disk to a larger disk and vice versa?
Yes. It’s possible to restore a disk image to a smaller drive if the smaller drive has enough space to accommodate the occupied space of the larger disk (e.g. if you have a 200 GB disk with 100 GB of space used, you can transfer an image of this disk to a 150 GB drive, but not to an 80 GB disk).
My customer has low bandwidth. How can I upload the initial backup?
This process is done in two stages:
- Creation of the initial backup on external media, please refer to the online documentation.
- Sending the data, which can be done through physical shipment, also described in this Knowledge Base article, or upload via WAN from an alternative location using a special tool.
What is an MSP backup solution?
MSP backup solutions enable managed service providers to deliver backup services to their clients.
Is Acronis Advanced Backup pack for MSPs?
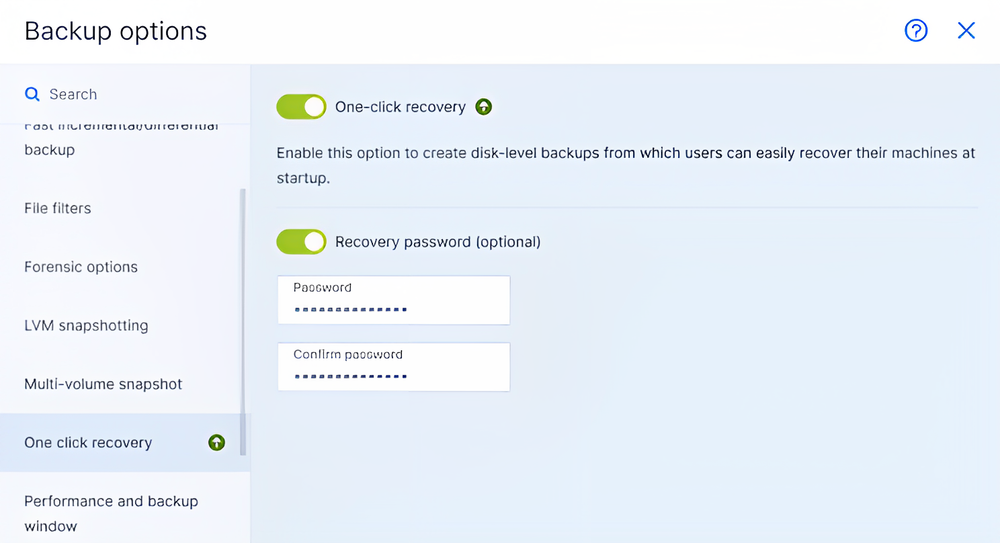
Yes, the Advanced Backup pack is available to managed service partners using Acronis Cyber Protect Cloud. The Advanced Backup pack enables service providers to extend the cloud backup capabilities their clients need to proactively protect their data, including continuous data protection, extended backup support, one-click recovery, and more.
Why are cloud backup services important for MSPs?
Cloud storage is the most flexible and cost-effective way to back up critical files and programs. Cloud backup solutions help isolate data from local device failures, malware attacks or natural disasters. However, experts recommend that you follow the 3-2-1 rule: make three copies of every piece of important data; store that data in two different formats; and keep one off-site copy.
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.