- Over 5,500,000users worldwide
- Over 100,000prevented cyberattacks last year
- Over 500,000,000clones and backups
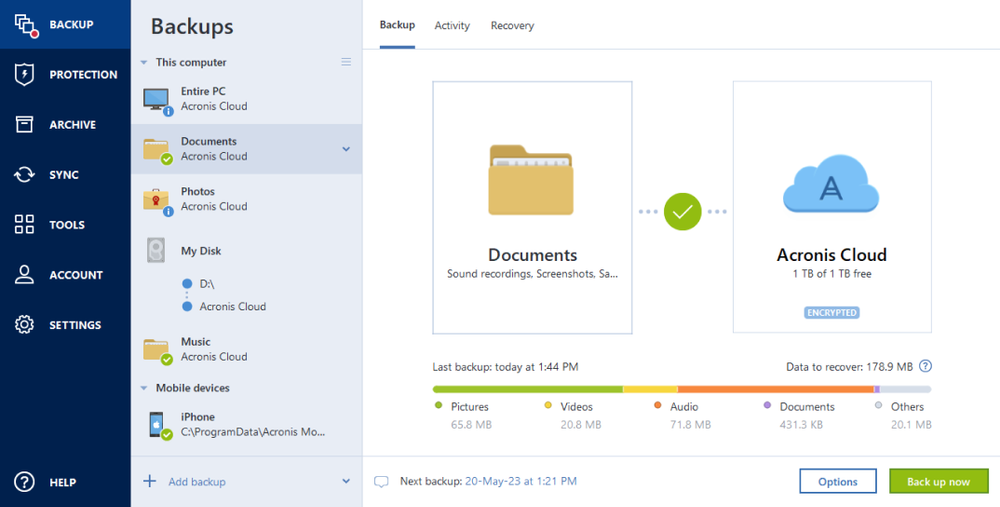
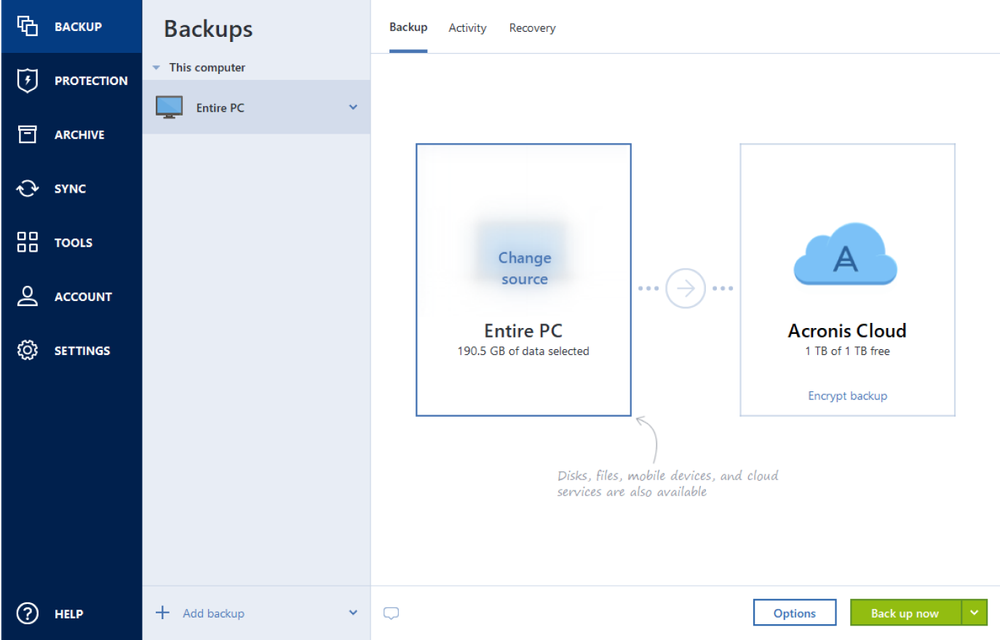
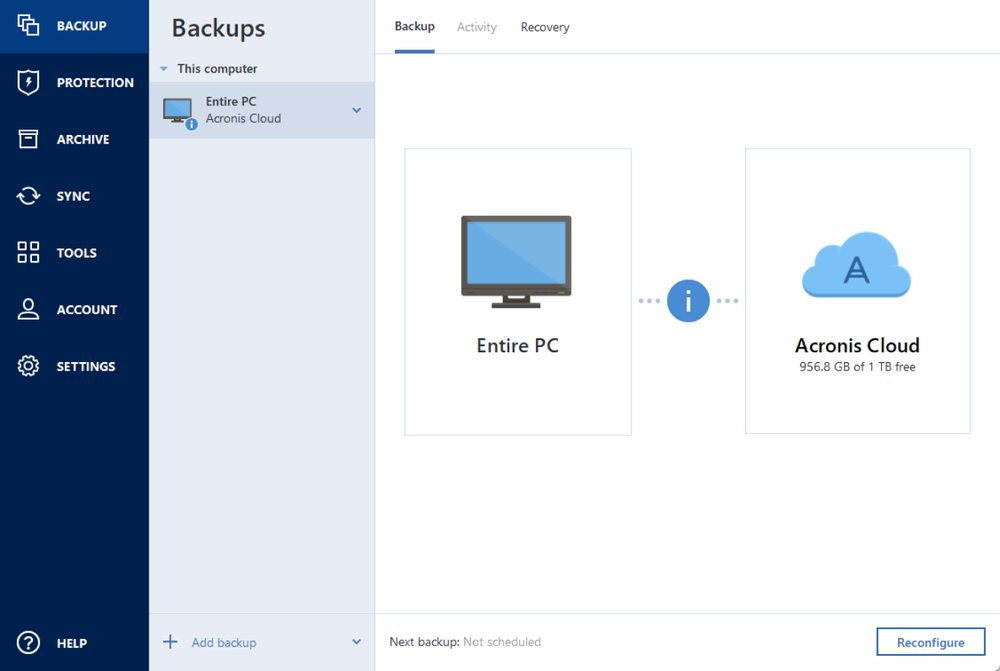
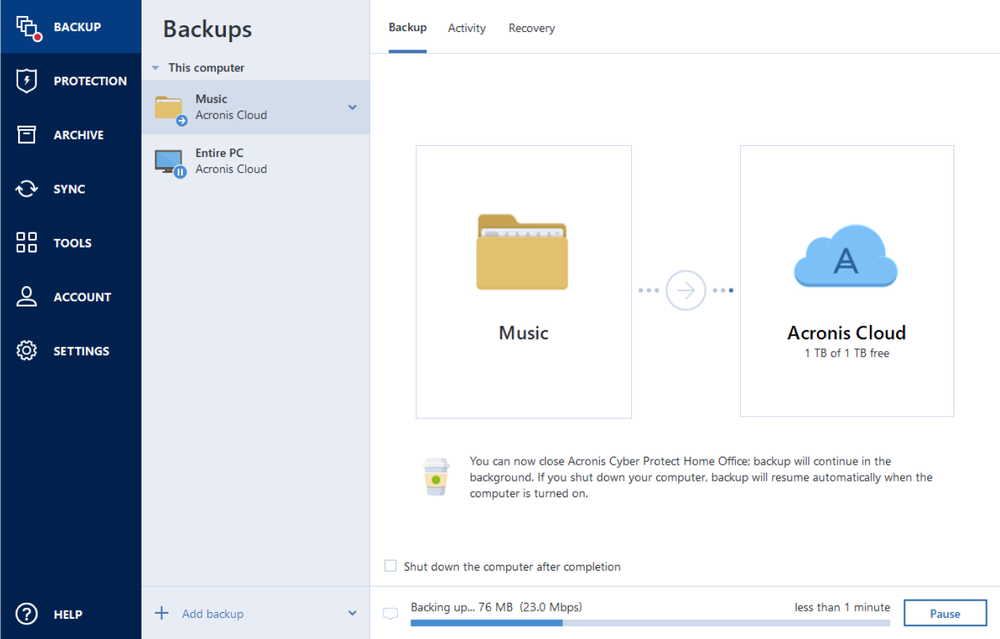
- Full image backupCreate a complete backup image of a whole system in just a few clicks ― no need to configure anything; all your data is protected.
- Local backupFast backup to internal or external drives or network share. Good for quick backup and recovery. Having multiple copies is recommended if you don’t use a cloud backup.
- Cloud backupReliable, secure and speedy backup to Acronis data centers. A great solution for an additional level of protection and remote access to the data.
Choose the Acronis True Image plan that meets your needs
Formerly Acronis Cyber Protect Home Office
Award-winning cyber protection solution
Over 5.5 million users rely on Acronis True Image every day




What our users say
Supported platforms
Microsoft Windows
- Windows 11 (all editions)
- Windows 10 (all editions)
- Windows 8+ (all editions)
- Windows 7 SP1 (all editions)
Windows file systems
- NTFS
- Ext2/Ext3/Ext4
-
ReiserFS(3)
-
Linux SWAP
-
HFS+/HFSX
-
FAT16/32/exFAT
Apple macOS
- macOS Sonoma 14
- macOS Ventura 13
- macOS Monterey 12
- macOS Big Sur 11
macOS file systems
- APFS
- HFS+
- FAT32
- NTFS (including Boot Camp)
Mobile operating systems
- iOS 15 or later
- Android 10 or later
Looking for help?
Frequently Asked Questions
Why do I need backup software?
Backup software creates reserve copies of your data. In case of a data loss event, you can use these copies to recover the original data. Backups are useful primarily for two purposes:
i. To recover an operating system when it is corrupted or cannot start (called disaster recovery).
ii. To recover specific files and folders after they have been accidentally deleted or corrupted.How often should I back up a computer?
Back up all your data after every significant event in your system. For example, after you bought a new computer, reinstalled the operating system, or installed an important system update.
You can also schedule backups to run automatically and on a regular basis. In this case, you will always have the latest version of your data for recovery.Where are backup files stored?
You can store the backed-up files on your machine, on an external disk, on a networked storage device, or in the cloud.
Can I schedule automatic backups with Acronis software?
Yes. See these procedures for Windows and for Mac.
Can I back up multiple devices with Acronis software?
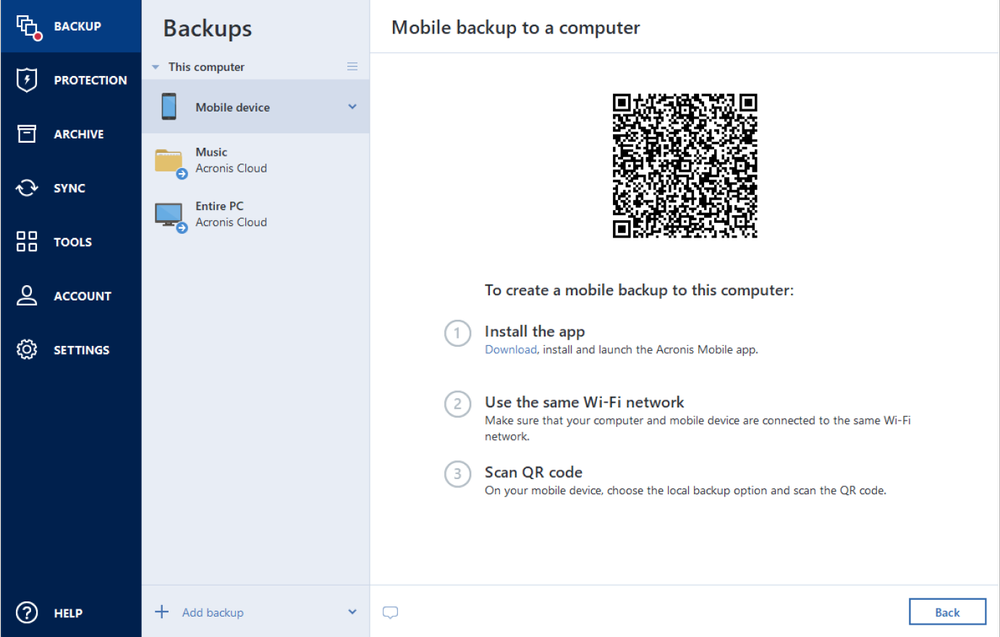
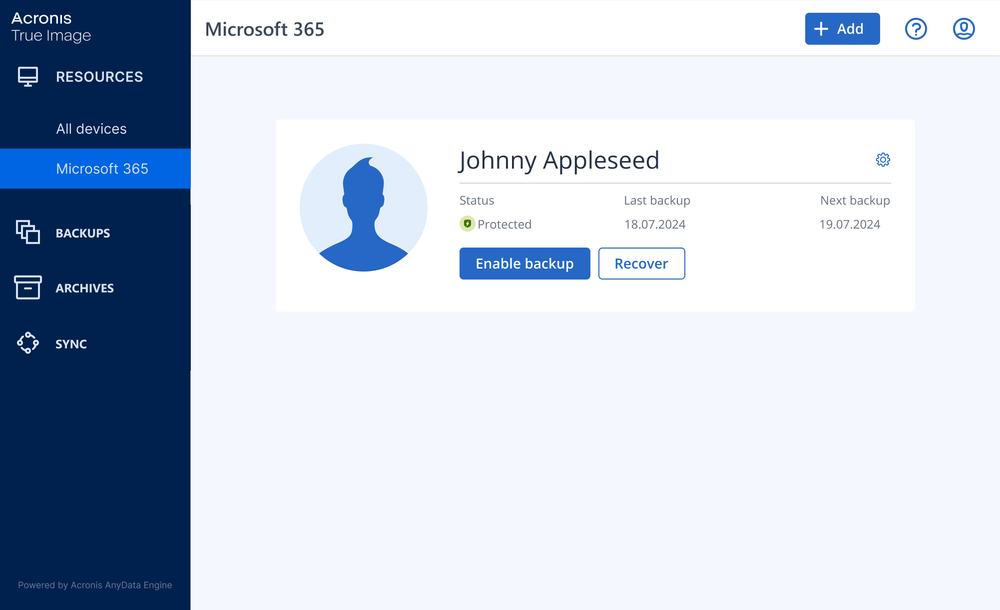
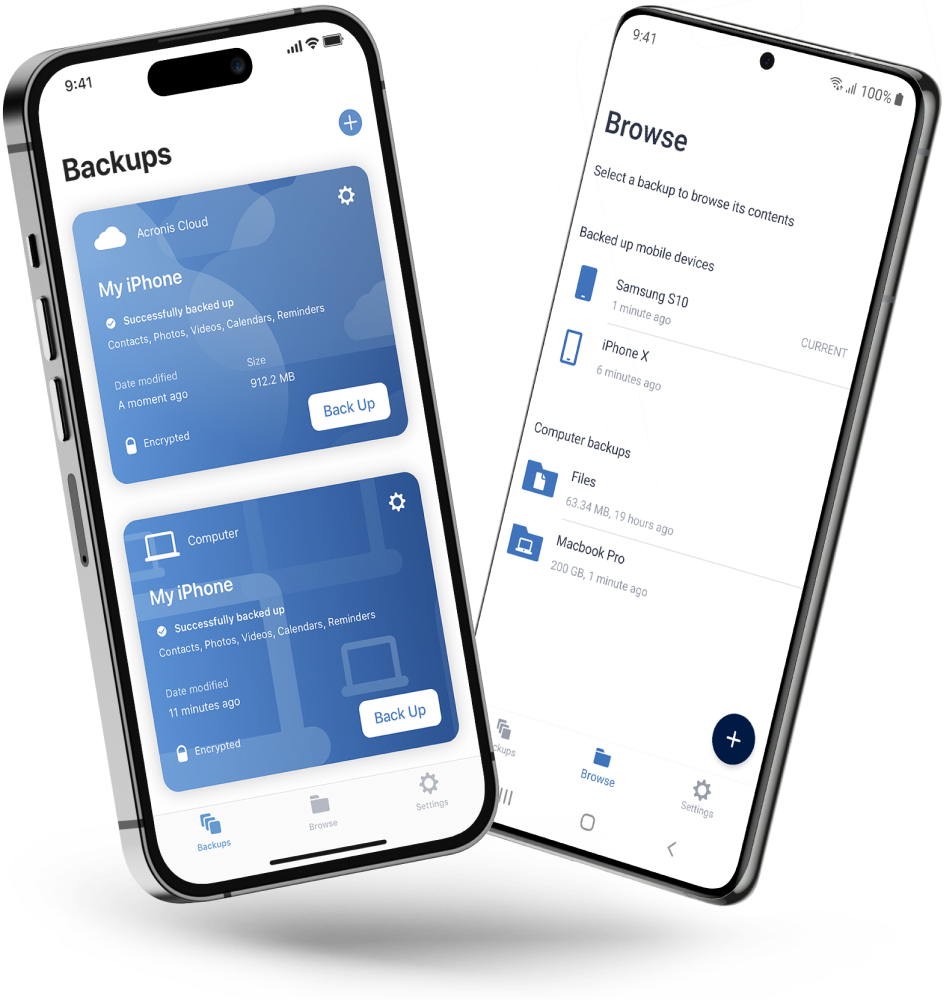
Yes. You can back up data on all computers, smartphones, and tablets registered for the same account. For more information on backing up multiple devices, see the procedures for Windows and for Mac.
Can I monitor and manage backups remotely?
Yes, you can. Online Dashboard allows you to track and control the protection status and backups of all computers, smartphones, and tablets registered for the same account. For more information, see the procedures for Windows and for Mac.
What security measures have Acronis backup software?
Acronis True Image provides the following types of protection:
i. Active Protection runs constantly in the background to protect your machines in real time while you work as usual.
ii. Antivirus Scans run on-demand to perform in-depth searches for malicious software throughout the whole system.
iii. Vulnerability assessment is a daily scan that runs in the background, detects vulnerabilities in your system and apps, and then assesses their severity.
iv. Identity protection prevents cybercriminals from stealing your personal information.
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.