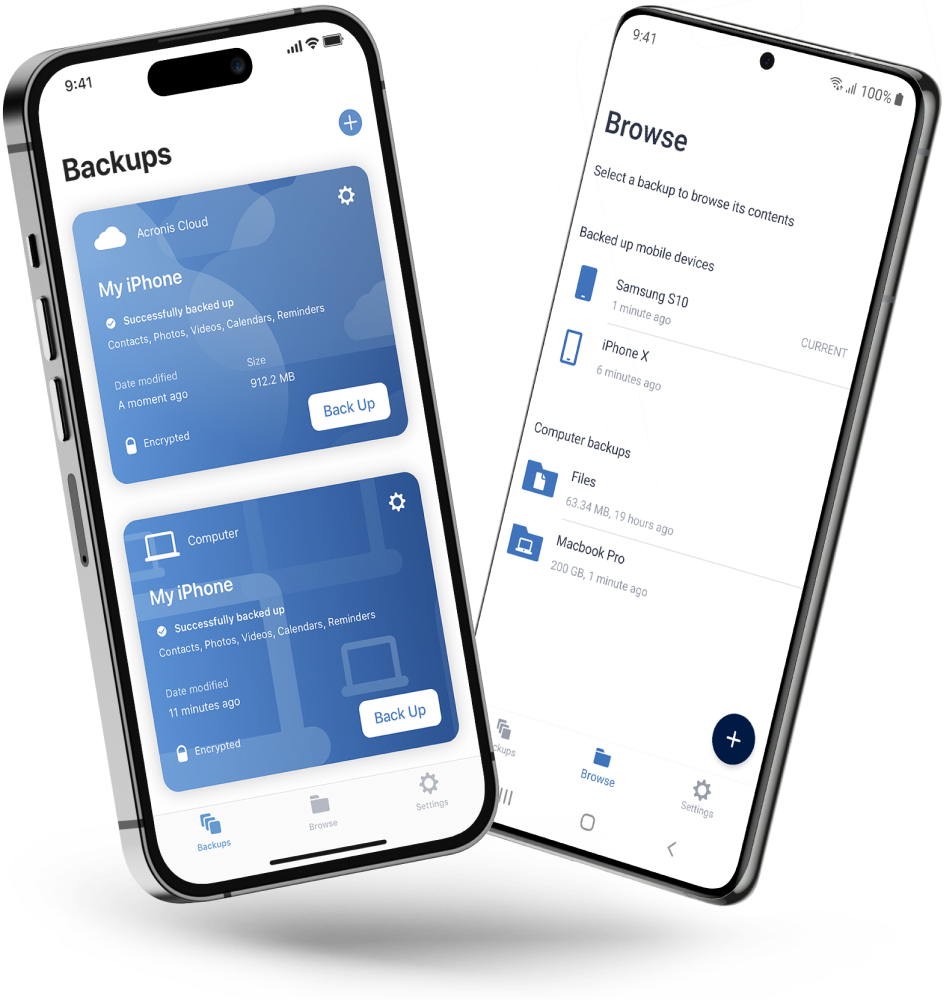
Protect your valuable personal data with Acronis True Image Premium
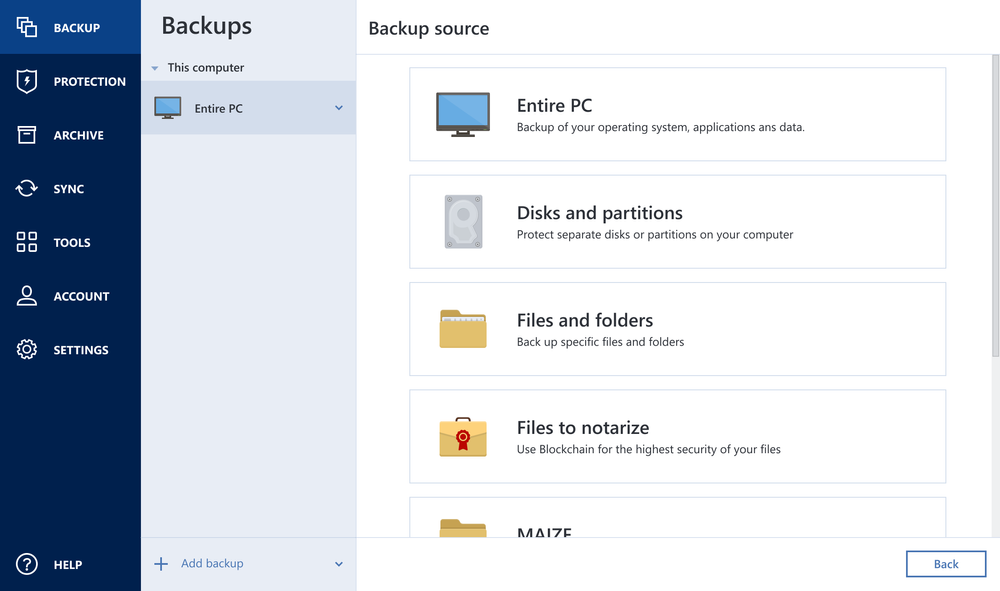
As data use and cyberthreats evolve, how you protect your personal sensitive data, apps and systems must evolve too. Acronis True Image Premium delivers superior cyber protection using leading-edge technologies to ensure your data is authentic, private and secure.
Easy contract verification
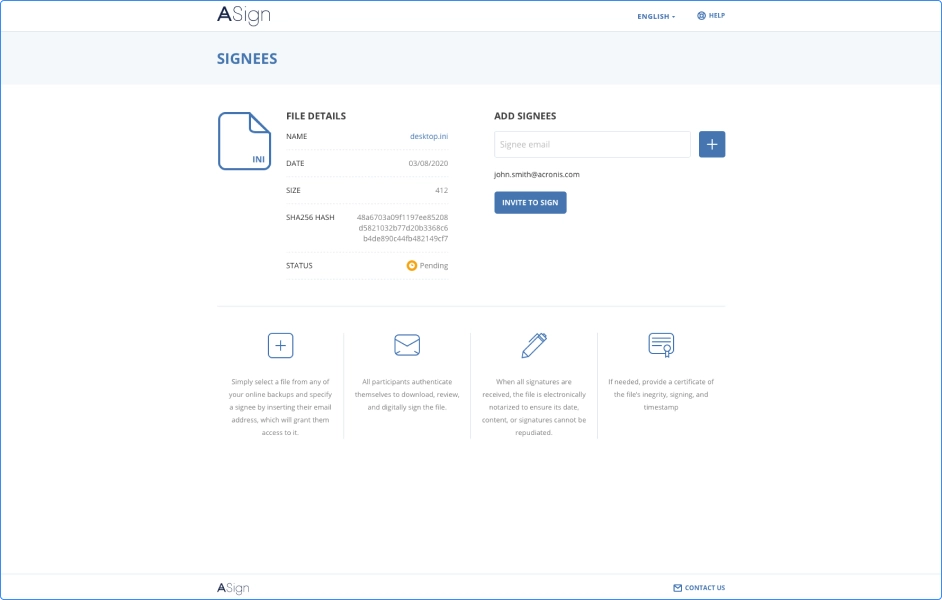
Proving a contract is in force requires verification with an electronic signature. Acronis ASign enables people to electronically sign documents like rental, sales, and insurance agreements, while creating an undeniable, timestamped certificate of proof in the blockchain.Efficient data authentication
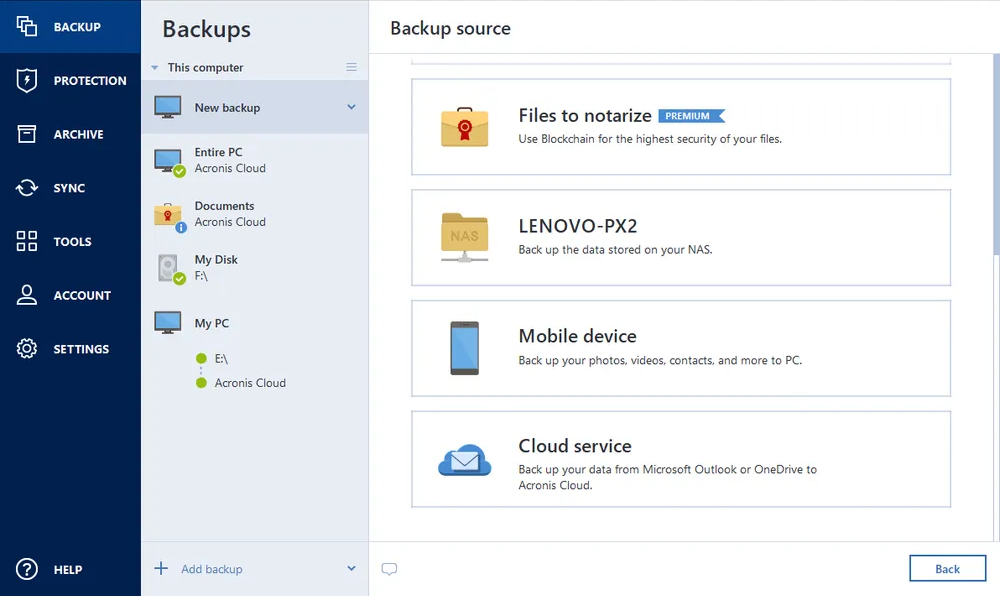
There are many instances when we must verify the authenticity of a file — from property records to court documents, to archived backup files. Acronis Notary uses blockchain technology to create a method of confirming data is original and unaltered.Secure backup and recovery
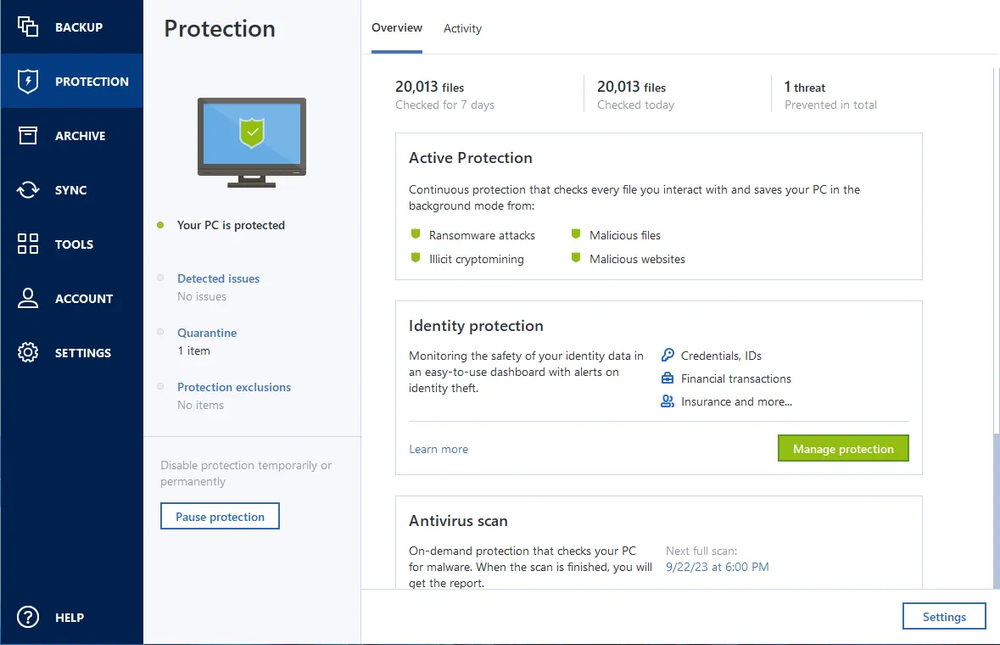
Hackers are always trying new techniques and technologies to attack your data. AI-based defense detects and defeats any malicious attacks – including never-before-seen threats — in real time, and automatically restores any affected files.
Acronis True Image Premium features
Choose the Acronis True Image plan that meets your needs
Formerly Acronis Cyber Protect Home Office
Award-winning cyber protection solution
Over 5.5 million users rely on Acronis True Image every day





What our users say
Supported platforms
Microsoft Windows
- Windows 11 (all editions)
- Windows 10 (all editions)
- Windows 8+ (all editions)
- Windows 7 SP1 (all editions)
Windows file systems
- NTFS
- Ext2/Ext3/Ext4
-
ReiserFS(3)
-
Linux SWAP
-
HFS+/HFSX
-
FAT16/32/exFAT
Apple macOS
- macOS Sequoia 15
- macOS Sonoma 14
- macOS Ventura 13
- macOS Monterey 12
- macOS Big Sur 11
macOS file systems
- APFS
- HFS+
- FAT32
- NTFS (including Boot Camp)
Mobile operating systems
- iOS 15 or later
- Android 10 or later
Looking for help?
Frequently Asked Questions
How does Acronis True Image protect my data?
Acronis True Image protects your data through a combination of backup, disaster recovery and cybersecurity solutions. It creates secure backups of your data, which can be stored locally or in the cloud, ensuring that you can recover your information in case of data loss or corruption. Additionally, it includes active protection features that defend against ransomware and other malware, continuously scanning for and blocking malicious activities.
What measures does Acronis True Image take to prevent unauthorized access to my personal information?
Acronis True Image employs several measures to prevent unauthorized access, including strong encryption, password protection and multifactor authentication options for accessing backups. It also uses advanced AI-based behavioral heuristics to detect and prevent suspicious activities, ensuring that your personal information remains secure against unauthorized access and cyberthreats.
Does Acronis True Image encrypt my data to ensure its confidentiality?
Yes, Acronis True Image uses robust encryption to secure your data. It encrypts your files during and after the backup process, ensuring that your data remains confidential and protected from unauthorized access. The encryption standards used are industry grade, providing strong protection for your data at rest and in transit.
Why do we need data protection?
Data protection is essential to safeguard important information from loss, theft, or corruption. With increasing cyberthreats and data breaches, protecting data ensures continuity of personal and professional activities, compliance with legal and regulatory requirements, and protection of privacy. It also helps in quickly recovering from hardware malfunctions, software issues or cyberattacks.
Why is data protection so important?
Data protection is crucial for several reasons:
- Security: Protects sensitive information from unauthorized access and cyberthreats.
- Privacy: Ensures personal information is kept confidential.
- Compliance: Helps comply with legal and regulatory obligations regarding data security and privacy.
- Integrity: Maintains the accuracy and reliability of data.
- Trust: Builds and maintains trust with customers and stakeholders by demonstrating commitment to data security.
What is the difference between Acronis True Image Premium subscription and Essentials?
The main difference between the Premium and Essentials subscriptions for Acronis True Image lies in the level of features and services offered. The Premium subscription includes more advanced features such as enhanced cybersecurity capabilities, Identity Protection, cloud storage space, and additional tools like blockchain-based file certification and electronic signature capabilities. In contrast, the Essential subscription provides essential backup and recovery functions along with basic anti-malware protection, suitable for users with less complex needs.
How to make an electronic signature that is legal and binding?
To create a legal and binding eSignature with Acronis True Image, which is included in the Premium subscription, follow these steps:
- Prepare the document: Open the document that needs to be signed within Acronis True Image. Ensure it is in its final form before signing.
- Access the eSignature feature: Navigate to the eSignature tool within the Acronis software. This feature might be integrated into the document management or security settings.
- Create your signature: You can create your eSignature using a drawing tool or by uploading an image of your signature. Some versions might allow you to type your name and select a stylized font.
- Apply the signature: Place the signature in the designated signature field on your document. Ensure it is correctly positioned and sized appropriately.
- Save and secure the document: Once the signature is applied, save the document. Acronis True Image will encrypt the document to ensure the signature and the document's integrity are maintained.
- Verify legal requirements: Ensure that the eSignature meets all local legal requirements for electronic signatures. This might include verifying that the method of capturing the signature and the type of document are both compliant with local laws.
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.